141:
83:
334:
325:
592:. As the signals from tags are very low-power (their cross-section is small, and the exits are wide), jamming requires little power. Evidently, shoplifters will not feel the need to follow radio transmission regulations; hence crude, easy-to-build transmitters will be adequate for them. However, due to their high frequency of operation, building a jammer can be difficult for microwave circuits; these systems are therefore less likely to be jammed. Although jamming is easy to perform, it is also easy to detect. A simple firmware upgrade should be adequate for modern DSP-based EAS systems to detect jamming. Nevertheless, the vast majority of EAS systems do not currently detect it.
510:. More sophisticated systems are available, which are more difficult to circumvent. These solutions tend to be product category specific as in the case of high value added electronics and consumables; consequently they are more expensive. Examples are "Safers", transparent secure boxes that completely enclose the article to be protected, Spiders that wrap around packaging and Electronic Merchandise Security Systems that allow phones and tablets to be used securely in the store before purchase. All of these require specific detachers or electronic keys at the point-of-sale desk. They have the advantages of being reusable, strong visual deterrents to potential theft.
254:
182:
199:
412:) coupled to one microwave and one electrostatic antenna. At the exit, one antenna emits a low-frequency (about 100 kHz) field, and another one emits a microwave field. The tag acts as a mixer re-emitting a combination of signals from both fields. This modulated signal triggers the alarm. These tags are permanent and somewhat costly. They are mostly used in clothing stores and have practically been withdrawn from use.
22:
312:
467:
not especially desirable either for the retailer or the manufacturer. The practical totality of EAS labels are discarded with the product packaging. This is of particular application in everyday items that consumers might carry on their person to avoid the inconvenience of potentially live reactivated EAS tags when walking in and out of retail stores.
438:
store actually has an anti-shoplifting system to deactivate a label they will only deactivate the one that is part of their system. If a store does not use an EAS system, they will not deactivate any tags at all. This is often the reason why people trigger an alarm entering a store, which can cause great frustration for both customers and staff.
121:; these tags can only be removed or deactivated by employees when the item is properly purchased or checked out. If merchandise bearing an active tag passes by an antenna installed at an entrance/exit, an alarm sounds alerting staff that merchandise is leaving the store unauthorized. Some stores also have antennas at entrances to
536:
that it cannot be removed. Some detachers actually have security tags inside them, to alert store personnel of them being removed from (or being brought into) the store. With increasing prevalence, stores have metal detectors at the entrance that can warn against the presence of booster bags or detachers.
572:
The shielding technique is well known amongst shoplifters and store owners. Some countries have specific laws against it. In any case, possession of such a bag demonstrates a prior-intent to commit a crime, which in many jurisdictions raises shoplifting from misdemeanor to felony status, because they
399:
Deactivation of RF labels is also dependent on the size of the label and the power of the deactivation pad (the larger the label, the greater the field it generates for deactivation to take place. For this reason very small labels can cause issues for consistent deactivation). It is common to find RF
535:
A detacher is used to remove re-usable hard tags. The type of detacher used will depend on the type of tag. There are a variety of detachers available, with the majority using powerful magnets. Any store that uses an anti-shoplifting system and has a detacher should take care to keep it secured such
466:
However, they may miss some tags or be unable to remove or deactivate all of them, especially if concealed or integrated tags are used. As a service to retailers, many manufacturers integrate security tags in the packaging of their products, or even inside the product itself, though this is rare and
395:
Efficiency is an important factor when choosing an overall EAS solution given that time lost attempting to deactivate labels can be an important drag of cashier productivity as well as customer satisfaction if unwanted alarms are caused by tags that have not been effectively deactivated at the point
233:
The EM systems can be used by libraries to protect books and media. In shops, unlike AM and RF, EM can be placed on small or round items and products with foil packaging or metal objects, like cosmetics, baby milk cans, medicines, DIY tools, homeware etc. EM systems can also detect objects placed in
189:
Concealed EAS systems have no visible pedestals or hindrance in the store facade. These systems are installed below the floor and dropped from the ceiling and can protect merchandise of retailers from being stolen. There are site conditions and other parameters which enable them to be installed, but
544:
Deactivation of magnetic tags is achieved by straightforward magnetization using a strong magnet. Magneto-acoustic tags require demagnetization. However, sticking a powerful magnet on them will bias disposable magnetic tags and prevent resonance in magneto-acoustic tags. Similarly, sticking a piece
494:
Tags can be equipped with a built-in alarm which sounds when the tag detects tampering or unauthorized removal from the store. The tag not only triggers the store's electronic article surveillance system, but also sounds an alarm attached to the merchandise. The local alarm continues to sound for
420:
Source tagging is the application of EAS security tags at the source, the supplier or manufacturer, instead of at the retail side of the chain. For the retailer, source tagging eliminates the labor expense needed to apply the EAS tags themselves, and reduces the time between receipt of merchandise
564:
Although the amount of shielding required depends on the system, its sensitivity, and the distance and orientation of the tags relative to its antennas, total enclosure of tags is not strictly necessary. Indeed, some shoplifters use clothes lined with aluminum foil. Low-frequency magnetic systems
474:
Shoplifting tools are illegal in many jurisdictions, and can, in any case, serve as evidence against the perpetrators. Hence, informed shoplifters, although they decrease their risk of being caught by the EAS, expose themselves to much greater judicial risks if they get caught with tools, booster
391:
is the most efficient of the three technologies (RF, EM, AM – there are no microwave labels) given that the reliable "remote" deactivation distance can be up to 30 cm (11.8 in). It also benefits the user in terms of running costs, since the RF de-activator only activates to send a pulse
291:
frequency of the amorphous strips. This causes the strip to vibrate longitudinally by magnetostriction, and it continues to oscillate after the burst is over. The vibration causes a change in magnetization in the amorphous strip, which induces an AC voltage in the receiver antenna. If this signal
437:
One significant problem from source tagging is something called "tag pollution" caused when non-deactivated tags carried around by customers cause unwanted alarms, decreasing the effectiveness and integrity of the EAS system. The problem is that no store has more than one system. Therefore, if a
424:
The high-speed application of EAS labels, suited for commercial packaging processes, was perfected via modifications to standard pressure-sensitive label applicators. Today, consumer goods are source tagged at high speeds with the EAS labels incorporated into the packaging or the product itself.
371:
Deactivation for 8.2 MHz label tags is typically achieved using a deactivation pad. In the absence of such a device, labels can be rendered inactive by punching a hole, or by covering the circuit with a metallic label, a "detuner". The deactivation pad functions by partially destroying the
353:
421:
and when the merchandise is ready for sale. For the supplier, the main benefit is the preservation of the retail packaging aesthetics by easing the application of security tags within product packaging. Source tagging allows the EAS tags to be concealed and more difficult to remove.
392:
when a circuit is present. Both EM and AM deactivation units are on all the time and consume considerably more electricity. The reliability of "remote" deactivation (i.e. non-contact or non-proximity deactivation) capability makes for a fast and efficient throughput at the checkout.
526:
from the coils crosses them will prevent detection, as the tag won't be coupled to the coils. This shortcoming, documented in the first EAS patents, can be solved by using multiple coils or by placing them in another arrangement such as a figure-of-eight. Sensitivity will still be
561:, shielding the tags from the antennas. Although some vendors claim that their acousto-magnetic systems cannot be defeated by bags shielded with aluminum foil, a sufficient amount of shielding (in the order of 30 layers of standard 20 μm foil) will defeat all standard systems.
428:
The most common source tags are AM strips and 8.2 MHz radio frequency labels. Most manufacturers use both when source tagging in the USA. In Europe there is little demand for AM tagging given that the Food and
Department Store environments are dominated by RF technology.
400:
deactivation built into barcode flat and vertical scanners at the POS in food retail especially in Europe and Asia where RF EAS technology has been the standard for nearly a decade. In apparel retail deactivation usually takes the form of flat pads of approx. 30x30 cm.
451:
EAS systems can provide a solid deterrent against casual theft. The occasional shoplifter, not being familiar with these systems and their mode of operation, will either get caught by them, or preferably, will be dissuaded from attempting any theft in the first place.
603:
Magneto-harmonic systems need to bring the tags to magnetic saturation and thus create magnetic fields strong enough to be felt through a small magnet. They routinely interfere with CRT displays. Demagnetization-remagnetization units also create intense fields.
226:(magnetic "hardness"). Detection is achieved by sensing harmonics and sum or difference signals generated by the non-linear magnetic response of the material under a mixture of low-frequency (in the 10 Hz to 1000 Hz range) magnetic fields.
229:
When the ferromagnetic material is magnetized, it biases the amorphous metal strip into saturation, where it no longer produces harmonics. Deactivation of these tags is therefore done with magnetization. Activation requires demagnetization.
545:
of metal, such as a large coin on a disposable radio-frequency tag will shield it. Non-disposable tags require stronger magnets or pieces of metal to disable or shield since the strips are inside the casing and thus further away.
295:
When the semi-hard magnet is magnetized, the tag is activated. The magnetized strip makes the amorphous strip respond much more strongly to the detectors, because the DC magnetic field given off by the strip offsets the
276:
and a strip of a magnetically semi-hard metallic strip, which is used as a biasing magnet (to increase signal strength) and to allow deactivation. These strips are not bound together but free to oscillate mechanically.
485:
In summary, while even the least expensive EAS systems will catch most occasional shoplifters, a broader range of measures are still required for an effective response that can protect profits without impeding sales.
376:. Though this sounds violent, in reality, both the process and the result are unnoticeable to the naked eye. The deactivator causes a micro short circuit in the label. This is done by submitting the tag to a strong
463:. A similar situation would be the loss of signal that a cell phone suffers inside an elevator: The electro-magnetic, or radio waves are effectively blocked, reducing the ability to send or receive information.
918:
470:
Hard tags, typically used for clothing or ink tags, known as benefit denial tags, may reduce the rate of tag manipulation. Also, shoplifters deactivating or detaching tags may be spotted by the shop staff.
621:, reported instances where acousto-magnetic EAS systems located at the front of retail stores caused a pacemaker to fail and a defibrillator to trigger, shocking the persons in which they were implanted.
624:
There are also concerns that some installations are intentionally reconfigured to exceed the rated specifications by the manufacturer, thereby exceeding tested and certified magnetic field levels.
368:
peak anywhere from 1.75 MHz to 9.5 MHz. The standard frequency for retail use is 8.2 MHz. Sensing is achieved by sweeping around the resonant frequency and detecting the dip.
919:
http://www.statutelaw.gov.uk/content.aspx?LegType=All+P...1&activeTextDocId=2922479&linkToATDocumentId=1204274&linkToATVersionNumber=3&showProsp=1�
970:
992:
300:
within the amorphous metal. The tag can also be deactivated by demagnetizing the strip, making the response small enough so that it will not be detected by the detectors.
610:
Radio-frequency systems tend to be the least interfering because of their lower power and operating frequency in the MHz range, making it easy to shield against them.
459:. These are typically large paper bags that have been lined with multiple layers of aluminium foil to effectively shield the RF label from detection, much like a
32:
518:
Except for microwave, the detection rate for all these tags depends on their orientation relative to the detection loops. For a pair of planar loops forming a
503:
A single EAS detector, suitable for a small shop, is accessible to all retail stores, and should form a part of any coherent loss or profit protection system.
1036:
137:
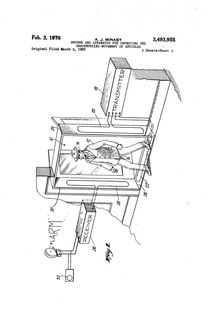
in 1964. He filed a patent for his "Method and
Apparatus for Detecting the Unauthorized Movement of Articles" in 1965 with the patent being granted in 1970.
1078:"Electronic Article Surveillance Systems and Interactions With Implantable Cardiac Devices: Risk of Adverse Interactions in Public and Commercial Spaces"
482:
to cut bottle tags) can lead to the suspect being arrested for suspicion of theft or "Going equipped for stealing, etc." within the UK judicial system.
140:
1212:
742:
1077:
1130:
880:
1159:
807:
1058:
921:
588:
Like most systems that rely on transmission of electromagnetic signals through a hostile medium, EAS sensors can be rendered inoperative by
455:
Informed shoplifters are conscious of how tags can be removed or deactivated. A common method of defeating RF tags is the use of so-called
1010:
713:
47:
82:
1187:
966:
899:
860:
836:
996:
569:
magnetic coupling. Magnetic shielding, with steel or mu-metal, would be more effective, but also cumbersome and expensive.
303:
AM tags are three dimensional plastic tags, much thicker than electro-magnetic strips and are thus seldom used for books.
678:"Modified Planar Square-Loop Antenna for Electronic Article Surveillance Radio Frequency Identification Applications"
69:
1222:
653:
1028:
600:
All electronic article surveillance systems emit electromagnetic energy and thus can interfere with electronics.
117:. EAS systems typically consist of two components: EAS antennas and EAS tags or labels. EAS tags are attached to
51:
638:
333:
324:
245:
with embedded microwires, which is used to detect confidential documents if they are removed from a building.
1202:
734:
945:
125:
to deter shoppers from taking unpaid-for merchandise into the restroom where they could remove the tags.
39:
1084:
1207:
495:
several minutes after leaving the store, attracting attention to the shopper carrying the merchandise.
1122:
1115:
877:
553:
Most systems can be circumvented by placing the tagged goods in a bag lined with aluminum foil. The
522:, magnetic field lines will be approximately parallel in their center. Orienting the tag so that no
1165:
799:
607:
Acousto-magnetic systems use less power but their signals are pulsed in the 100 Hz range.
219:
1014:
917:
Statute Law database, Theft Act (1968) (c. 60) s. 25(1), "Going equipped for stealing, etc.",
284:, which implies that they can efficiently convert magnetic energy into mechanical vibrations.
1102:
292:
meets the required parameters (correct frequency, repetition, etc.), the alarm is activated.
287:
The detectors for such tags emit periodic tonal bursts at about 58 kHz, the same as the
238:
773:
618:
8:
297:
215:
1172:
896:
857:
777:
190:
often malls insist on concealed system as a mandate to improve the shopping experience.
1217:
705:
566:
785:
91:
1197:
709:
697:
677:
643:
381:
828:
781:
689:
633:
377:
266:
265:
These are similar to magnetic tags in that they are made of two strips: a strip of
380:
field at the resonant frequency, which induces voltages exceeding the capacitor's
925:
903:
884:
864:
388:
273:
258:
207:
114:
1192:
577:
519:
270:
253:
242:
223:
43:
693:
1181:
1154:
764:
Herzer, G. (2003). "Magnetic materials for electronic article surveillance".
701:
589:
565:
will require more shielding than radio-frequency systems due to their use of
523:
134:
122:
110:
181:
558:
479:
460:
218:
value. Except for permanent tags, this strip is also lined with a strip of
527:
orientation-dependent but detection will be possible at all orientations.
153:
There are several major types of electronic article surveillance systems:
648:
614:
554:
456:
102:
361:
475:
bags, or while trying to remove tags, as this shows intent to steal.
373:
365:
288:
157:
Electro-magnetic, also known as magneto-harmonic or
Barkhausen effect
133:
EAS tags that could be attached to items in stores were invented by
352:
144:
Arthur Minasy's original patent for
Electronic Article Surveillance
198:
878:
http://veripakproducts.com/Tag%20Pollution%20Survey%20Results.pdf
211:
937:
676:
Zahid, M. N.; Jiang, J.; Rafique, U.; Eric, D. (October 2020).
539:
343:
185:
A concealed EAS system with antennas hanging above the entrance
106:
87:
446:
409:
118:
1075:
280:
Amorphous metals are used in such systems due to their good
1059:"Retailers Applaud Senate Crackdown on Booster Bag Thefts"
938:"Checkpoint label business solutions and Sensormatic tags"
895:
Sensormatic, "Global Source
Tagging / Glossary of Terms",
576:
To deter the use of booster bags, some stores have add-on
311:
506:
Disposable tags cost a matter of cents and may have been
408:
These permanent tags are made of a non-linear element (a
478:
The possession of shoplifting tools (e.g. lined bags or
897:
http://www.sensormatic.com/Products/GST/glossary.aspx
675:
682:
50:, and by adding encyclopedic content written from a
913:
911:
1123:"Cell phones safe to use in hospitals: U.S. study"
595:
1179:
908:
876:VeriPak Products, Tag Pollution Survey Results,
160:Acousto-magnetic, also known as magnetostrictive
306:
86:Electronic article surveillance antennas at an
1076:J. Rod Gimbel; James W. Cox Jr (March 2007).
364:(L for inductor, C for capacitor) that has a
540:Electro-magnetic activation and deactivation
766:Journal of Magnetism and Magnetic Materials
248:
193:
169:Video surveillance systems (to some extent)
447:Occasional versus professional shoplifters
101:(EAS) is a type of system used to prevent
1213:Automatic identification and data capture
1083:. Mayo Clinic Proceedings. Archived from
489:
113:, or unwanted removal of properties from
70:Learn how and when to remove this message
351:
310:
252:
202:EM labels in different sizes and colors.
197:
180:
176:
139:
81:
973:from the original on September 11, 2016
580:systems which sense metallic surfaces.
1180:
763:
31:contains content that is written like
498:
745:from the original on 19 January 2023
671:
669:
403:
15:
1039:from the original on 29 August 2018
800:"How Anti-shoplifting Devices Work"
507:
342:RF tag placed under the label of a
13:
993:"Acousto-Magnetic Technology]"
573:are considered a "burglary tool."
513:
234:foil bags or in metal briefcases.
206:These tags are made of a strip of
172:Concealed EAS surveillance systems
163:Radio frequency (RF, 8.2 MHz)
14:
1234:
1161:How Anti-shoplifting Devices Work
1148:
1120:Study referenced in news article
666:
415:
261:image of an acousto-magnetic tag.
111:pilferage of books from libraries
654:Evaluation of binary classifiers
432:
332:
323:
20:
1188:Retail processes and techniques
1133:from the original on 2007-03-20
1069:
1051:
1021:
1003:
985:
959:
948:from the original on 2016-11-27
930:
839:from the original on 2010-03-18
810:from the original on 2006-04-27
716:from the original on 2023-11-09
241:(IP) protection against theft:
99:Electronic article surveillance
969:. Alpha High Theft Solutions.
889:
870:
850:
821:
792:
757:
727:
639:Radio-frequency identification
596:Interference and health issues
360:These tags are essentially an
1:
786:10.1016/S0304-8853(02)00930-7
659:
441:
237:A further application is the
1029:"Newsbrief: Shoplifting bag"
548:
530:
307:Radio frequency (RF) systems
7:
627:
508:embedded during manufacture
10:
1239:
967:"2 & 3 Alarm Hard Tag"
613:A March 2007 study by the
583:
387:In terms of deactivation,
128:
694:10.1134/S1064226920100071
249:Acousto-magnetic systems
194:Electro-magnetic systems
148:
1223:Retailing-related crime
858:"Global Source Tagging"
356:Series 304 RF EAS label
282:magnetoelastic coupling
214:) which has a very low
1110:Cite journal requires
735:"Method and apparatus"
490:Tags containing alarms
357:
316:
262:
220:ferromagnetic material
203:
186:
145:
95:
355:
314:
256:
239:intellectual property
201:
184:
177:Concealed EAS systems
143:
85:
52:neutral point of view
1011:"About booster bags"
772:(254–255): 598–602.
619:Rochester, Minnesota
1203:American inventions
1173:EAS Security System
778:2003JMMM..254..598H
298:magnetic anisotropy
216:magnetic saturation
44:promotional content
1168:on August 13, 2009
1063:Retail Council NYS
924:2023-11-09 at the
902:2010-03-08 at the
883:2011-07-17 at the
863:2010-03-12 at the
499:Installation costs
358:
317:
263:
204:
187:
146:
96:
92:Torp shopping mall
46:and inappropriate
1208:Wireless locating
804:HowStuffWorks.com
688:(10): 1161–1166.
644:Barkhausen effect
404:Microwave systems
382:breakdown voltage
80:
79:
72:
1230:
1169:
1164:, archived from
1142:
1141:
1139:
1138:
1119:
1113:
1108:
1106:
1098:
1096:
1095:
1089:
1082:
1073:
1067:
1066:
1055:
1049:
1048:
1046:
1044:
1035:. 14 June 1994.
1025:
1019:
1018:
1013:. Archived from
1007:
1001:
1000:
995:. Archived from
989:
983:
982:
980:
978:
963:
957:
956:
954:
953:
934:
928:
915:
906:
893:
887:
874:
868:
854:
848:
847:
845:
844:
825:
819:
818:
816:
815:
796:
790:
789:
761:
755:
754:
752:
750:
731:
725:
724:
722:
721:
673:
634:Active packaging
336:
327:
267:magnetostrictive
222:with a moderate
115:office buildings
75:
68:
64:
61:
55:
33:an advertisement
24:
23:
16:
1238:
1237:
1233:
1232:
1231:
1229:
1228:
1227:
1178:
1177:
1158:
1151:
1146:
1145:
1136:
1134:
1121:
1111:
1109:
1100:
1099:
1093:
1091:
1087:
1080:
1074:
1070:
1057:
1056:
1052:
1042:
1040:
1033:The Independent
1027:
1026:
1022:
1009:
1008:
1004:
991:
990:
986:
976:
974:
965:
964:
960:
951:
949:
936:
935:
931:
926:Wayback Machine
916:
909:
904:Wayback Machine
894:
890:
885:Wayback Machine
875:
871:
865:Wayback Machine
855:
851:
842:
840:
827:
826:
822:
813:
811:
798:
797:
793:
762:
758:
748:
746:
739:ppubs.uspto.gov
733:
732:
728:
719:
717:
674:
667:
662:
630:
598:
586:
551:
542:
533:
516:
514:Tag orientation
501:
492:
449:
444:
435:
418:
406:
389:radio frequency
378:electromagnetic
362:LC tank circuit
350:
349:
348:
347:
339:
338:
337:
329:
328:
309:
274:amorphous metal
251:
208:amorphous metal
196:
179:
151:
131:
76:
65:
59:
56:
37:
25:
21:
12:
11:
5:
1236:
1226:
1225:
1220:
1215:
1210:
1205:
1200:
1195:
1190:
1176:
1175:
1170:
1150:
1149:External links
1147:
1144:
1143:
1129:. 2007-03-09.
1112:|journal=
1068:
1050:
1020:
1017:on 2008-02-07.
1002:
999:on 2007-08-29.
984:
958:
929:
907:
888:
869:
849:
833:Vitag Security
829:"System types"
820:
806:. April 2000.
791:
756:
726:
664:
663:
661:
658:
657:
656:
651:
646:
641:
636:
629:
626:
597:
594:
585:
582:
578:metal detector
557:will act as a
550:
547:
541:
538:
532:
529:
520:Helmholtz coil
515:
512:
500:
497:
491:
488:
448:
445:
443:
440:
434:
431:
417:
416:Source tagging
414:
405:
402:
341:
340:
331:
330:
322:
321:
320:
319:
318:
308:
305:
250:
247:
243:Security paper
224:coercive field
195:
192:
178:
175:
174:
173:
170:
167:
164:
161:
158:
150:
147:
130:
127:
78:
77:
48:external links
28:
26:
19:
9:
6:
4:
3:
2:
1235:
1224:
1221:
1219:
1216:
1214:
1211:
1209:
1206:
1204:
1201:
1199:
1196:
1194:
1191:
1189:
1186:
1185:
1183:
1174:
1171:
1167:
1163:
1162:
1156:
1155:HowStuffWorks
1153:
1152:
1132:
1128:
1124:
1117:
1104:
1090:on 2007-09-28
1086:
1079:
1072:
1064:
1060:
1054:
1038:
1034:
1030:
1024:
1016:
1012:
1006:
998:
994:
988:
972:
968:
962:
947:
943:
939:
933:
927:
923:
920:
914:
912:
905:
901:
898:
892:
886:
882:
879:
873:
866:
862:
859:
856:Sensormatic,
853:
838:
834:
830:
824:
809:
805:
801:
795:
787:
783:
779:
775:
771:
767:
760:
744:
740:
736:
730:
715:
711:
707:
703:
699:
695:
691:
687:
683:
679:
672:
670:
665:
655:
652:
650:
647:
645:
642:
640:
637:
635:
632:
631:
625:
622:
620:
616:
611:
608:
605:
601:
593:
591:
581:
579:
574:
570:
568:
562:
560:
556:
546:
537:
528:
525:
524:magnetic flux
521:
511:
509:
504:
496:
487:
483:
481:
476:
472:
468:
464:
462:
458:
453:
439:
433:Tag pollution
430:
426:
422:
413:
411:
401:
397:
393:
390:
385:
383:
379:
375:
369:
367:
363:
354:
345:
335:
326:
313:
304:
301:
299:
293:
290:
285:
283:
278:
275:
272:
271:ferromagnetic
268:
260:
255:
246:
244:
240:
235:
231:
227:
225:
221:
217:
213:
209:
200:
191:
183:
171:
168:
165:
162:
159:
156:
155:
154:
142:
138:
136:
135:Arthur Minasy
126:
124:
120:
116:
112:
108:
107:retail stores
104:
100:
93:
89:
84:
74:
71:
63:
53:
49:
45:
41:
35:
34:
29:This article
27:
18:
17:
1166:the original
1160:
1135:. Retrieved
1126:
1103:cite journal
1092:. Retrieved
1085:the original
1071:
1062:
1053:
1041:. Retrieved
1032:
1023:
1015:the original
1005:
997:the original
987:
975:. Retrieved
961:
950:. Retrieved
942:Dragon Guard
941:
932:
891:
872:
852:
841:. Retrieved
832:
823:
812:. Retrieved
803:
794:
769:
765:
759:
747:. Retrieved
738:
729:
718:. Retrieved
685:
681:
623:
612:
609:
606:
602:
599:
587:
575:
571:
563:
559:Faraday cage
552:
543:
534:
517:
505:
502:
493:
484:
480:wire cutters
477:
473:
469:
465:
461:Faraday cage
457:booster bags
454:
450:
436:
427:
423:
419:
407:
398:
394:
386:
370:
359:
302:
294:
286:
281:
279:
264:
236:
232:
228:
205:
188:
152:
132:
98:
97:
66:
60:October 2020
57:
42:by removing
38:Please help
30:
649:Tattle-Tape
615:Mayo Clinic
555:booster bag
119:merchandise
103:shoplifting
1182:Categories
1137:2007-04-22
1094:2007-04-22
977:August 28,
952:2016-11-27
843:2010-03-16
814:2006-05-12
720:2021-04-12
660:References
567:near-field
442:Discussion
40:improve it
1218:Packaging
1043:27 August
710:226364958
702:1064-2269
549:Shielding
531:Detaching
396:of sale.
374:capacitor
366:resonance
289:resonance
166:Microwave
123:restrooms
90:store in
1198:Security
1131:Archived
1037:Archived
971:Archived
946:Archived
922:Archived
900:Archived
881:Archived
861:Archived
837:Archived
808:Archived
743:Archived
714:Archived
628:See also
315:RF label
94:, Sweden
1127:Reuters
774:Bibcode
590:jamming
584:Jamming
259:cutaway
212:metglas
129:History
88:H&M
749:19 May
708:
700:
346:bottle
344:liquor
1193:Theft
1088:(PDF)
1081:(PDF)
706:S2CID
410:diode
149:Types
105:from
1116:help
1045:2017
979:2016
751:2023
698:ISSN
782:doi
770:254
690:doi
617:in
1184::
1157::
1125:.
1107::
1105:}}
1101:{{
1061:.
1031:.
944:.
940:.
910:^
835:.
831:.
802:.
780:.
768:.
741:.
737:.
712:.
704:.
696:.
686:65
684:.
680:.
668:^
384:.
269:,
257:A
109:,
1140:.
1118:)
1114:(
1097:.
1065:.
1047:.
981:.
955:.
867:.
846:.
817:.
788:.
784::
776::
753:.
723:.
692::
210:(
73:)
67:(
62:)
58:(
54:.
36:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.