212:
test email message, returns the test email message, and subsequently blocks all other email messages from that spammer. Spammers continue to use the antispam honeypot for spamming, but the spam is never delivered. Meanwhile, the honeypot operator can notify spammers' ISPs and have their
Internet accounts canceled. If honeypot operators detect spammers who use open-proxy servers, they can also notify the proxy server operator to lock down the server to prevent further misuse.
47:
43:
vulnerabilities in a specific network system. A honeypot is a decoy used to protect a network from present or future attacks. Honeypots derive their value from the use by attackers. If not interacted with, the honeypot has little to no value. Honeypots can be used for everything from slowing down or stopping automated attacks, capturing new exploits, to gathering intelligence on emerging threats or early warning and prediction.
129:, multiple honeypots can be hosted on a single physical machine. Therefore, even if the honeypot is compromised, it can be restored more quickly. In general, high-interaction honeypots provide more security by being difficult to detect, but they are expensive to maintain. If virtual machines are not available, one physical computer must be maintained for each honeypot, which can be exorbitantly expensive. Example:
348:(TTPs). Thus, a honeypot needs to emulate essential services in the production network and grant the attacker the freedom to perform adversarial activities to increase its attractiveness to the attacker. Although the honeypot is a controlled environment and can be monitored by using tools such as honeywall, attackers may still be able to use some honeypots as pivot nodes to penetrate production systems.
332:, argues that every system running his honeypot should have a deception port which adversaries can use to detect the honeypot. Cohen believes that this might deter adversaries. Honeypots also allow for early detection of legitimate threats. No matter how the honeypot detects the exploit, it can alert you immediately to the attempted attack.
227:
Spam still flows through open relays, but the volume is much smaller than in 2001-02. While most spam originates in the U.S., spammers hop through open relays across political boundaries to mask their origin. Honeypot operators may use intercepted relay tests to recognize and thwart attempts to relay
139:
simulate only the services frequently requested by attackers. Since they consume relatively few resources, multiple virtual machines can easily be hosted on one physical system, the virtual systems have a short response time, and less code is required, reducing the complexity of the virtual system's
118:
are full-fledged production systems. The activities of the attacker are monitored by using a bug tap that has been installed on the honeypot's link to the network. No other software needs to be installed. Even though a pure honeypot is useful, stealthiness of the defense mechanisms can be ensured by
351:
The second risk of honeypots is that they may attract legitimate users due to a lack of communication in large-scale enterprise networks. For example, the security team who applies and monitors the honeypot may not disclose the honeypot location to all users in time due to the lack of communication
319:
Just as honeypots are weapons against spammers, honeypot detection systems are spammer-employed counter-weapons. As detection systems would likely use unique characteristics of specific honeypots to identify them, such as the property-value pairs of default honeypot configuration, many honeypots in
97:
community targeting different networks. These honeypots do not add direct value to a specific organization; instead, they are used to research the threats that organizations face and to learn how to better protect against those threats. Research honeypots are complex to deploy and maintain, capture
211:
Typically, spammers test a mail server for open relaying by simply sending themselves an email message. If the spammer receives the email message, the mail server obviously allows open relaying. Honeypot operators, however, can use the relay test to thwart spammers. The honeypot catches the relay
42:
The main use for this network decoy is to distract potential attackers from more important information and machines on the real network, learn about the forms of attacks they can suffer, and examine such attacks during and after the exploitation of a honeypot. It provides a way to prevent and see
86:
are easy to use, capture only limited information, and are used primarily by corporations. Production honeypots are placed inside the production network with other production servers by an organization to improve their overall state of security. Normally, production honeypots are low-interaction
172:
Malware honeypots are a decoy designed to intentionally attract malicious software. It does this by imitating a vulnerable system or network, such as a web server. The honeypot is intentionally set up with security flaws that look to invite these malware attacks. Once attacked IT teams can then
150:
is a type of honeypot that masquerades as an open proxy. It can often take form as a server designed to look like a misconfigured HTTP proxy. Probably the most famous open proxy was the default configuration of sendmail (before version 8.9.0 in 1998) which would forward email to and from any
195:
There are several capabilities such honeypots provide to these administrators, and the existence of such fake abusable systems makes abuse more difficult or risky. Honeypots can be a powerful countermeasure to abuse from those who rely on very high volume abuse (e.g., spammers).
63:
Physical honeypots: real machine with its own IP address, this machine simulates behaviors modeled by the system. Many times this modality is not used as much as the high price of acquiring new machines, their maintenance and the complication affected by configuring specialized
311:. In order to understand intruders' techniques in this context, several honeypots has been proposed. Conpot is a low interaction honeypot capable of simulation Siemens PLCs. HoneyPLC is a medium interaction honeypot that can simulate Siemens, Rockwell and other PLC brands.
67:
Virtual honeypots: the use of these types of honeypot allow one to install and simulate hosts on the network from different operating systems, but in order to do so, it is necessary to simulate the TCP/IP of the target operating system. This modality is more
35:(for example, in a network site) that appears to be a legitimate part of the site which contains information or resources of value to attackers. It is actually isolated, monitored, and capable of blocking or analyzing the attackers. This is similar to police
192:. These are servers which accept e-mail from anyone on the Internet—including spammers—and send it to its destination. Some system administrators have created honeypot programs that masquerade as these abusable resources to discover spammer activity.
223:
tools. In the early days of anti-spam honeypots, spammers, with little concern for hiding their location, felt safe testing for vulnerabilities and sending spam directly from their own systems. Honeypots made the abuse riskier and more difficult.
163:
has emerged using basic honeypot technology with the addition of advanced automation for scale. Deception technology addresses the automated deployment of honeypot resources over a large commercial enterprise or government institution.
1195:"Guide to Industrial Control Systems (ICS) Security - Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and other control system configurations such as Programmable Logic Controllers (PLC)"
269:", the term "honeypot" might be more suitable for systems and techniques that are used to detect or counterattack probes. With a spamtrap, spam arrives at its destination "legitimately"—exactly as non-spam email would arrive.
228:
spam through their honeypots. "Thwart" may mean "accept the relay spam but decline to deliver it." Honeypot operators may discover other details concerning the spam and the spammer by examining the captured spam messages.
428:, attempting to obtain a copy of a password file. Cheswick wrote that he and colleagues constructed a "chroot "Jail" (or "roach motel")" which allowed them to observe their attacker over a period of several months.
423:
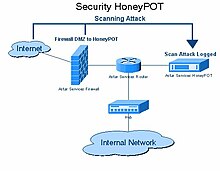
One of the earliest documented cases of the cybersecurity use of a honeypot began in
January 1991. On January 7, 1991, while he worked at AT&T Bell Laboratories Cheswick observed a criminal hacker, known as a
380:. Typically, a honey net is used for monitoring a larger and/or more diverse network in which one honeypot may not be sufficient. Honey nets and honeypots are usually implemented as parts of larger
216:
The apparent source may be another abused system. Spammers and other abusers may use a chain of such abused systems to make detection of the original starting point of the abuse traffic difficult.
362:"A 'honey net' is a network of high interaction honeypots that simulates a production network and configured such that all activity is monitored, recorded and in a degree, discreetly regulated."
320:
use utilise a set of unique characteristics larger and more daunting to those seeking to detect and thereby identify them. This is an unusual circumstance in software; a situation in which
324:(a large number of versions of the same software, all differing slightly from each other) can be beneficial. There's also an advantage in having some easy-to-detect honeypots deployed.
276:, a distributed, open source project that uses honeypot pages installed on websites around the world. These honeypot pages disseminate uniquely tagged spamtrap email addresses and
407:
39 (1976) as "the deliberate planting of apparent flaws in a system for the purpose of detecting attempted penetrations or confusing an intruder about which flaws to exploit".
125:
imitate the activities of the production systems that host a variety of services and, therefore, an attacker may be allowed a lot of services to waste their time. By employing
1735:
920:
445:
The metaphor of a bear being attracted to and stealing honey is common in many traditions, including
Germanic, Celtic, and Slavic. A common Slavic word for the bear is
1611:
72:
Honeypots can be classified based on their deployment (use/action) and based on their level of involvement. Based on deployment, honeypots may be classified as:
960:
523:
329:
1667:
144:. This type of honeypot was one of the first types being created in the late nineties and was mainly used for detecting attacks, not studying them.
296:
firewalls provide/support honeypot architectures so that the intruder runs against a trap database while the web application remains functional.
345:
265:
An email address that is not used for any other purpose than to receive spam can also be considered a spam honeypot. Compared with the term "
1767:
1556:
2016:
292:. As such activities are not recognized by basic firewalls, companies often use database firewalls for protection. Some of the available
935:
1465:
1103:
449:"honey eater". The tradition of bears stealing honey has been passed down through stories and folklore, especially the well known
404:
1868:
1782:
1748:
1449:
1389:
1322:
1243:
1080:
849:
600:
87:
honeypots, which are easier to deploy. They give less information about the attacks or attackers than research honeypots.
1012:
2164:
1787:
866:
381:
2133:
1824:
1723:
964:
876:
739:
702:
652:
1696:
Shepard, E. H., Milne, A. A. (1994). The
Complete Tales of Winnie-the-Pooh. United Kingdom: Dutton Children's Books.
1581:
527:
2021:
1532:
549:
921:"Deception related technology – its not just a "nice to have", its a new strategy of defense – Lawrence Pingree"
321:
1848:
1777:
1128:
2087:
1675:
340:
The goal of honeypots is to attract and engage attackers for a sufficiently long period to obtain high-level
308:
240:
94:
1289:
López-Morales, Efrén; Rubio-Medrano, Carlos; Doupé, Adam; Shoshitaishvili, Yan; Wang, Ruoyu; Bao, Tiffany;
477:
280:
can then be tracked—the corresponding spam mail is subsequently sent to these spamtrap e-mail addresses.
232:
1374:
Proceedings of the 2019 International
Conference on Computational Science and Computational Intelligence
2107:
584:
Proceedings of the 2011 International
Conference on Communication, Computing & Security - ICCCS '11
1975:
304:
1909:
1899:
244:
98:
extensive information, and are used primarily by research, military, or government organizations.
1985:
1070:
341:
27:
mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of
1764:
2036:
1863:
1560:
783:
Litchfield, Samuel; Formby, David; Rogers, Jonathan; Meliopoulos, Sakis; Beyah, Raheem (2016).
1970:
1368:
Cabral, Warren; Valli, Craig; Sikos, Leslie; Wakeling, Samuel (2019). "Review and
Analysis of
1817:
1740:
2143:
2097:
2026:
1884:
160:
1797:
1612:"National Bureau of Standards (February 15, 1976). Glossary for Computer Systems Security"
1533:"illusive networks: Why Honeypots are Stuck in the Past | NEA | New Enterprise Associates"
8:
2092:
1582:"Know Your Enemy: GenII Honey Nets Easier to deploy, harder to detect, safer to maintain"
1469:
936:"What Is a Honeypot in Cybersecurity? Types, Implementation, and Real-World Applications"
502:
425:
416:
28:
581:
Mairh, A; Barik, D; Verma, K; Jena, D (2011). "Honeypot in network security: A survey".
2077:
1914:
1894:
1328:
1249:
1175:
812:
708:
658:
606:
1072:
Certified
Ethical Hacker: Securing Network Infrastructure in Certified Ethical Hacking
2169:
2102:
2056:
1965:
1744:
1719:
1519:
4th
International Conference on New Trends in Information Science and Service Science
1495:
1445:
1385:
1369:
1332:
1318:
1301:. CCS '20. New York, NY, USA: Association for Computing Machinery. pp. 279–291.
1299:
Proceedings of the 2020 ACM SIGSAC Conference on
Computer and Communications Security
1239:
1179:
1167:
1076:
872:
845:
804:
735:
698:
648:
596:
582:
492:
472:
391:
The concept of the honey net first began in 1999 when Lance Spitzner, founder of the
273:
24:
1253:
868:
Architecting Secure Software Systems Page 25 – CRC Press, Taylor & Francis Group
712:
662:
610:
2117:
2082:
1810:
1437:
1377:
1310:
1302:
1231:
1202:
1159:
986:
837:
816:
796:
690:
640:
588:
392:
369:
307:(ICS) are often the target of cyberattacks. One of the main targets within ICS are
130:
36:
2112:
2051:
1955:
1798:
A curated list of honeypots, tools and components focused on open source projects
1771:
1381:
1294:
756:
497:
467:
450:
185:
126:
1732:
2072:
2046:
1853:
1715:
1514:
1431:
1223:
1147:
784:
731:
632:
439:
436:
411:
1639:
1499:
1441:
1288:
1020:
644:
203:
and provide bulk spam capture (which enables operators to determine spammers'
173:
analyze the malware to better understand where it comes from and how it acts.
2158:
2031:
1950:
1858:
1290:
1235:
1171:
808:
289:
1306:
1194:
1043:
748:
694:
592:
1889:
1207:
892:
831:
432:
293:
1640:"An Evening with BerferdIn Which a Cracker is Lured, Endured, and Studied"
1314:
841:
682:
59:
Honeypots can be differentiated based on if they are physical or virtual:
2041:
1960:
800:
482:
462:
1163:
637:
19th Annual Computer Security Applications Conference, 2003. Proceedings
403:
An early formulation of the concept, called "entrapment", is defined in
2000:
1980:
1945:
1589:
487:
325:
200:
189:
1990:
1940:
1346:
1295:"HoneyPLC: A Next-Generation Honeypot for Industrial Control Systems"
1201:(NIST Special Publication (SP) 800-82). Gaithersburg, MD: 155 pages.
220:
207:
and response mechanisms). As described by M. Edwards at ITPRo Today:
1267:
1228:
2016 IEEE Conference on Intelligence and Security Informatics (ISI)
1132:
906:
277:
266:
260:
181:
93:
are run to gather information about the motives and tactics of the
46:
1792:
1995:
1904:
1833:
1802:
782:
1405:
1935:
1930:
1733:
Sean Bodmer; Max Kilger; Gregory Carpenter; Jade Jones (2012).
141:
1736:
Reverse Deception: Organized Cyber Threat Counter-Exploitation
1222:
Jicha, Arthur; Patton, Mark; Chen, Hsinchun (September 2016).
1017:
Intrusion Detection, Honeypots and Incident Handling Resources
893:"Exposing the Underground: Adventures of an Open Proxy Server"
543:
541:
539:
537:
388:
is a centralized collection of honeypots and analysis tools.
830:
Göbel, Jan Gerrit; Dewald, Andreas; Freiling, Felix (2011).
687:
Proceedings of the 45th annual southeast regional conference
534:
204:
32:
1193:
Stouffer, Keith; Falco, Joe; Scarfone, Karen (June 2011).
1013:"Honeypot Software, Honeypot Products, Deception Software"
865:
Talukder, Asoke K.; Chaitanya, Manish (17 December 2008).
219:
This in itself is indicative of the power of honeypots as
101:
Based on design criteria, honeypots can be classified as:
1367:
1372:
Artefacts and Their Potential to be Used Deceptively".
299:
1192:
1512:
785:"Rethinking the Honeypot for Cyber-Physical Systems"
524:"Honeypots: A Security Manager's Guide to Honeypots"
435:
used honeypot techniques to track down users of the
829:
580:
1129:"Secure Your Database Using Honeypot Architecture"
410:The earliest honeypot techniques are described in
1224:"SCADA honeypots: An in-depth analysis of Conpot"
1131:. dbcoretech.com. August 13, 2010. Archived from
907:"Capturing web attacks with open proxy honeypots"
864:
683:"Honeypots: Concepts, approaches, and challenges"
231:Open-relay honeypots include Jackpot, written in
2156:
288:Databases often get attacked by intruders using
1513:Qassrawi, Mahmoud T.; Hongli Zhang (May 2010).
1489:
1221:
987:"Sophos reveals latest spam relaying countries"
757:"Attacks Landscape in the Dark Side of the Web"
1778:Distributed Open Proxy Honeypots Project: WASC
1709:
1062:
1041:
725:
681:Mokube, Iyatiti; Adams, Michele (March 2007).
1818:
1515:"Client honeypots: Approaches and challenges"
395:, published the paper "To Build a Honeypot".
243:by Karl A. Krueger; and spamhole, written in
39:, colloquially known as "baiting" a suspect.
1774:- AP less clear-text WPA2 passphrase hacking
961:"Antispam Honeypots Give Spammers Headaches"
576:
574:
572:
570:
251:is an open-source honeypot (or "proxypot").
1148:"Stuxnet: Dissecting a Cyberwarfare Weapon"
680:
1825:
1811:
1068:
1044:"spamhole – The Fake Open SMTP Relay Beta"
376:Two or more honeypots on a network form a
1206:
754:
567:
521:
50:Diagram of an information system honeypot
1788:SANS Institute: Fundamental Honeypotting
1466:"Honeywall CDROM – The Honeynet Project"
633:"Honeypots: Catching the insider threat"
630:
199:These honeypots can reveal the abuser's
45:
1145:
933:
508:
154:
2157:
1869:Timeline of computer viruses and worms
352:or the prevention of insider threats.
159:Recently, a new market segment called
1806:
1019:. Honeypots.net. 2013. Archived from
314:
1783:SANS Institute: What is a Honey Pot?
676:
674:
672:
283:
167:
31:. Generally, a honeypot consists of
1398:
1042:dustintrammell (27 February 2013).
958:
382:network intrusion detection systems
346:Tactics, Techniques, and Procedures
300:Industrial Control Systems honeypot
184:abuse vulnerable resources such as
13:
1832:
1703:
1559:. Clarkconnect.com. Archived from
547:
272:An amalgam of these techniques is
14:
2181:
2134:Computer and network surveillance
1758:
1075:. Cengage Learning. pp. 3–.
669:
587:. Vol. 1. pp. 600–605.
963:. Windows IT Pro. Archived from
522:Cole, Eric; Northcutt, Stephen.
176:
1690:
1660:
1632:
1604:
1574:
1557:"cisco router Customer support"
1549:
1525:
1506:
1494:. Addison-Wesley Professional.
1483:
1458:
1424:
1361:
1339:
1282:
1260:
1215:
1186:
1139:
1121:
1096:
1035:
1005:
979:
952:
927:
913:
899:
885:
858:
344:(IoC) such as attack tools and
1849:Comparison of computer viruses
1765:The Ultimate Fake Access Point
823:
776:
755:Katakoglu, Onur (2017-04-03).
719:
624:
550:"A Virtual Honeypot Framework"
515:
309:Programmable Logic Controllers
1:
2088:Data loss prevention software
1588:. 12 May 2005. Archived from
355:
254:
119:a more controlled mechanism.
1382:10.1109/CSCI49370.2019.00035
478:Defense strategy (computing)
7:
1152:IEEE Security & Privacy
1146:Langner, Ralph (May 2011).
456:
19:In computer terminology, a
16:Computer security mechanism
10:
2186:
2108:Intrusion detection system
1712:Honeypots tracking hackers
1492:Honeypots Tracking Hackers
1376:. IEEE. pp. 166–171.
1069:Ec-Council (5 July 2009).
728:Honeypots tracking hackers
639:. IEEE. pp. 170–179.
398:
305:Industrial Control Systems
258:
123:High-interaction honeypots
108:high-interaction honeypots
2165:Computer network security
2126:
2065:
2009:
1976:Privacy-invasive software
1923:
1877:
1841:
1442:10.1007/978-1-4302-0007-9
645:10.1109/csac.2003.1254322
137:Low-interaction honeypots
111:low-interaction honeypots
1490:Spitzner, Lance (2002).
1236:10.1109/ISI.2016.7745468
342:Indicators of Compromise
335:
54:
1986:Rogue security software
1710:Lance Spitzner (2002).
1307:10.1145/3372297.3423356
789:IEEE Internet Computing
726:Lance Spitzner (2002).
695:10.1145/1233341.1233399
593:10.1145/1947940.1948065
2022:Classic Mac OS viruses
1864:List of computer worms
1272:, MushMush, 2023-06-23
1208:10.6028/nist.sp.800-82
940:Cybersecurity Exchange
934:Praveen (2023-07-31).
364:
328:, the inventor of the
214:
51:
1741:McGraw-Hill Education
1668:"The word for "bear""
1433:Honeypots for Windows
1104:"What is a honeypot?"
842:10.1524/9783486711516
631:Spitzner, L. (2003).
367:-Lance Spitzner,
360:
209:
49:
2144:Operation: Bot Roast
1678:on 29 September 2013
1351:, SEFCOM, 2023-05-24
1230:. pp. 196–198.
1050:. Dice Holdings, Inc
923:. 28 September 2016.
801:10.1109/MIC.2016.103
689:. pp. 321–326.
509:References and notes
161:deception technology
155:Deception technology
84:Production honeypots
76:production honeypots
2093:Defensive computing
2010:By operating system
1406:"Deception Toolkit"
1164:10.1109/MSP.2011.67
1108:IONOS Digital Guide
140:security. Example:
29:information systems
2078:Antivirus software
1924:Malware for profit
1895:Man-in-the-browser
1842:Infectious malware
1770:2021-02-25 at the
1592:on 25 January 2009
734:. pp. 68–70.
315:Honeypot detection
249:Bubblegum Proxypot
91:Research honeypots
79:research honeypots
52:
2152:
2151:
2103:Internet security
2057:HyperCard viruses
1966:Keystroke logging
1956:Fraudulent dialer
1900:Man-in-the-middle
1750:978-0-07-177249-5
1451:978-1-59059-335-6
1391:978-1-7281-5584-5
1324:978-1-4503-7089-9
1245:978-1-5090-3865-7
1199:NIST Publications
1135:on March 8, 2012.
1082:978-1-4354-8365-1
1023:on 8 October 2003
991:Help Net Security
851:978-3-486-71151-6
602:978-1-4503-0464-1
530:on 16 March 2017.
493:Network telescope
330:Deception Toolkit
284:Database honeypot
274:Project Honey Pot
235:by Jack Cleaver;
168:Malware honeypots
25:computer security
2177:
2118:Network security
2083:Browser security
1827:
1820:
1813:
1804:
1803:
1793:Project Honeypot
1754:
1729:
1697:
1694:
1688:
1687:
1685:
1683:
1674:. Archived from
1664:
1658:
1657:
1655:
1653:
1644:
1636:
1630:
1629:
1627:
1625:
1616:
1608:
1602:
1601:
1599:
1597:
1586:Honeynet Project
1578:
1572:
1571:
1569:
1568:
1553:
1547:
1546:
1544:
1543:
1529:
1523:
1522:
1510:
1504:
1503:
1487:
1481:
1480:
1478:
1477:
1468:. Archived from
1462:
1456:
1455:
1428:
1422:
1421:
1419:
1417:
1402:
1396:
1395:
1365:
1359:
1358:
1357:
1356:
1343:
1337:
1336:
1286:
1280:
1279:
1278:
1277:
1264:
1258:
1257:
1219:
1213:
1212:
1210:
1190:
1184:
1183:
1143:
1137:
1136:
1125:
1119:
1118:
1116:
1115:
1100:
1094:
1093:
1091:
1089:
1066:
1060:
1059:
1057:
1055:
1039:
1033:
1032:
1030:
1028:
1009:
1003:
1002:
1000:
998:
983:
977:
976:
974:
972:
956:
950:
949:
947:
946:
931:
925:
924:
917:
911:
910:
903:
897:
896:
895:. 21 March 2011.
889:
883:
882:
862:
856:
855:
833:Client-Honeypots
827:
821:
820:
780:
774:
773:
771:
770:
761:
752:
746:
745:
723:
717:
716:
678:
667:
666:
628:
622:
621:
619:
617:
578:
565:
564:
562:
560:
545:
532:
531:
526:. Archived from
519:
417:The Cuckoo's Egg
393:Honeynet Project
372:
370:Honeynet Project
186:open mail relays
127:virtual machines
37:sting operations
2185:
2184:
2180:
2179:
2178:
2176:
2175:
2174:
2155:
2154:
2153:
2148:
2127:Countermeasures
2122:
2113:Mobile security
2061:
2052:Palm OS viruses
2017:Android malware
2005:
1919:
1915:Zombie computer
1873:
1837:
1831:
1772:Wayback Machine
1761:
1751:
1726:
1706:
1704:Further reading
1701:
1700:
1695:
1691:
1681:
1679:
1666:
1665:
1661:
1651:
1649:
1642:
1638:
1637:
1633:
1623:
1621:
1619:www.govinfo.gov
1614:
1610:
1609:
1605:
1595:
1593:
1580:
1579:
1575:
1566:
1564:
1555:
1554:
1550:
1541:
1539:
1531:
1530:
1526:
1511:
1507:
1488:
1484:
1475:
1473:
1464:
1463:
1459:
1452:
1430:
1429:
1425:
1415:
1413:
1404:
1403:
1399:
1392:
1366:
1362:
1354:
1352:
1345:
1344:
1340:
1325:
1287:
1283:
1275:
1273:
1266:
1265:
1261:
1246:
1220:
1216:
1191:
1187:
1144:
1140:
1127:
1126:
1122:
1113:
1111:
1110:. 8 August 2017
1102:
1101:
1097:
1087:
1085:
1083:
1067:
1063:
1053:
1051:
1040:
1036:
1026:
1024:
1011:
1010:
1006:
996:
994:
985:
984:
980:
970:
968:
957:
953:
944:
942:
932:
928:
919:
918:
914:
905:
904:
900:
891:
890:
886:
879:
863:
859:
852:
828:
824:
781:
777:
768:
766:
759:
753:
749:
742:
724:
720:
705:
679:
670:
655:
629:
625:
615:
613:
603:
579:
568:
558:
556:
546:
535:
520:
516:
511:
498:Operation Trust
468:Client honeypot
459:
451:Winnie the Pooh
401:
374:
368:
366:
358:
338:
317:
302:
286:
263:
257:
179:
170:
157:
57:
17:
12:
11:
5:
2183:
2173:
2172:
2167:
2150:
2149:
2147:
2146:
2141:
2136:
2130:
2128:
2124:
2123:
2121:
2120:
2115:
2110:
2105:
2100:
2095:
2090:
2085:
2080:
2075:
2073:Anti-keylogger
2069:
2067:
2063:
2062:
2060:
2059:
2054:
2049:
2047:Mobile malware
2044:
2039:
2034:
2029:
2024:
2019:
2013:
2011:
2007:
2006:
2004:
2003:
1998:
1993:
1988:
1983:
1978:
1973:
1968:
1963:
1958:
1953:
1948:
1943:
1938:
1933:
1927:
1925:
1921:
1920:
1918:
1917:
1912:
1907:
1902:
1897:
1892:
1887:
1881:
1879:
1875:
1874:
1872:
1871:
1866:
1861:
1856:
1854:Computer virus
1851:
1845:
1843:
1839:
1838:
1830:
1829:
1822:
1815:
1807:
1801:
1800:
1795:
1790:
1785:
1780:
1775:
1760:
1759:External links
1757:
1756:
1755:
1749:
1730:
1724:
1716:Addison-Wesley
1705:
1702:
1699:
1698:
1689:
1659:
1631:
1603:
1573:
1548:
1524:
1505:
1482:
1457:
1450:
1423:
1397:
1390:
1360:
1338:
1323:
1315:2286/R.I.57069
1293:(2020-11-02).
1291:Ahn, Gail-Joon
1281:
1259:
1244:
1214:
1185:
1138:
1120:
1095:
1081:
1061:
1034:
1004:
993:. 24 July 2006
978:
967:on 1 July 2017
951:
926:
912:
909:. 3 July 2007.
898:
884:
877:
857:
850:
822:
775:
747:
740:
732:Addison-Wesley
718:
703:
668:
653:
623:
601:
566:
533:
513:
512:
510:
507:
506:
505:
500:
495:
490:
485:
480:
475:
470:
465:
458:
455:
437:darknet market
412:Clifford Stoll
400:
397:
359:
357:
354:
337:
334:
316:
313:
301:
298:
285:
282:
259:Main article:
256:
253:
178:
175:
169:
166:
156:
153:
116:Pure honeypots
113:
112:
109:
106:
105:pure honeypots
81:
80:
77:
70:
69:
65:
56:
53:
15:
9:
6:
4:
3:
2:
2182:
2171:
2168:
2166:
2163:
2162:
2160:
2145:
2142:
2140:
2137:
2135:
2132:
2131:
2129:
2125:
2119:
2116:
2114:
2111:
2109:
2106:
2104:
2101:
2099:
2096:
2094:
2091:
2089:
2086:
2084:
2081:
2079:
2076:
2074:
2071:
2070:
2068:
2064:
2058:
2055:
2053:
2050:
2048:
2045:
2043:
2040:
2038:
2037:MacOS malware
2035:
2033:
2032:Linux malware
2030:
2028:
2025:
2023:
2020:
2018:
2015:
2014:
2012:
2008:
2002:
1999:
1997:
1994:
1992:
1989:
1987:
1984:
1982:
1979:
1977:
1974:
1972:
1969:
1967:
1964:
1962:
1959:
1957:
1954:
1952:
1951:Form grabbing
1949:
1947:
1944:
1942:
1939:
1937:
1934:
1932:
1929:
1928:
1926:
1922:
1916:
1913:
1911:
1908:
1906:
1903:
1901:
1898:
1896:
1893:
1891:
1888:
1886:
1883:
1882:
1880:
1876:
1870:
1867:
1865:
1862:
1860:
1859:Computer worm
1857:
1855:
1852:
1850:
1847:
1846:
1844:
1840:
1835:
1828:
1823:
1821:
1816:
1814:
1809:
1808:
1805:
1799:
1796:
1794:
1791:
1789:
1786:
1784:
1781:
1779:
1776:
1773:
1769:
1766:
1763:
1762:
1752:
1746:
1742:
1738:
1737:
1731:
1727:
1725:0-321-10895-7
1721:
1717:
1713:
1708:
1707:
1693:
1677:
1673:
1669:
1663:
1648:
1641:
1635:
1620:
1613:
1607:
1591:
1587:
1583:
1577:
1563:on 2017-01-16
1562:
1558:
1552:
1538:
1534:
1528:
1520:
1516:
1509:
1501:
1497:
1493:
1486:
1472:on 2022-10-11
1471:
1467:
1461:
1453:
1447:
1443:
1439:
1435:
1434:
1427:
1411:
1407:
1401:
1393:
1387:
1383:
1379:
1375:
1371:
1364:
1350:
1349:
1342:
1334:
1330:
1326:
1320:
1316:
1312:
1308:
1304:
1300:
1296:
1292:
1285:
1271:
1270:
1263:
1255:
1251:
1247:
1241:
1237:
1233:
1229:
1225:
1218:
1209:
1204:
1200:
1196:
1189:
1181:
1177:
1173:
1169:
1165:
1161:
1157:
1153:
1149:
1142:
1134:
1130:
1124:
1109:
1105:
1099:
1084:
1078:
1074:
1073:
1065:
1049:
1045:
1038:
1022:
1018:
1014:
1008:
992:
988:
982:
966:
962:
955:
941:
937:
930:
922:
916:
908:
902:
894:
888:
880:
878:9781420087857
874:
871:. CRC Press.
870:
869:
861:
853:
847:
843:
839:
835:
834:
826:
818:
814:
810:
806:
802:
798:
794:
790:
786:
779:
765:
758:
751:
743:
741:0-321-10895-7
737:
733:
729:
722:
714:
710:
706:
704:9781595936295
700:
696:
692:
688:
684:
677:
675:
673:
664:
660:
656:
654:0-7695-2041-3
650:
646:
642:
638:
634:
627:
612:
608:
604:
598:
594:
590:
586:
585:
577:
575:
573:
571:
555:
551:
544:
542:
540:
538:
529:
525:
518:
514:
504:
501:
499:
496:
494:
491:
489:
486:
484:
481:
479:
476:
474:
471:
469:
466:
464:
461:
460:
454:
452:
448:
443:
441:
438:
434:
429:
427:
421:
419:
418:
414:'s 1989 book
413:
408:
406:
396:
394:
389:
387:
383:
379:
373:
371:
363:
353:
349:
347:
343:
333:
331:
327:
323:
322:"versionitis"
312:
310:
306:
297:
295:
291:
290:SQL injection
281:
279:
275:
270:
268:
262:
252:
250:
246:
242:
239:, written in
238:
234:
229:
225:
222:
217:
213:
208:
206:
202:
197:
193:
191:
187:
183:
177:Spam versions
174:
165:
162:
152:
151:destination.
149:
145:
143:
138:
134:
132:
128:
124:
120:
117:
110:
107:
104:
103:
102:
99:
96:
92:
88:
85:
78:
75:
74:
73:
66:
62:
61:
60:
48:
44:
40:
38:
34:
30:
26:
22:
2138:
1910:Trojan horse
1890:Clickjacking
1734:
1711:
1692:
1680:. Retrieved
1676:the original
1671:
1662:
1650:. Retrieved
1647:cheswick.com
1646:
1634:
1622:. Retrieved
1618:
1606:
1594:. Retrieved
1590:the original
1585:
1576:
1565:. Retrieved
1561:the original
1551:
1540:. Retrieved
1536:
1527:
1518:
1508:
1491:
1485:
1474:. Retrieved
1470:the original
1460:
1432:
1426:
1414:. Retrieved
1409:
1400:
1373:
1363:
1353:, retrieved
1347:
1341:
1298:
1284:
1274:, retrieved
1268:
1262:
1227:
1217:
1198:
1188:
1158:(3): 49–51.
1155:
1151:
1141:
1133:the original
1123:
1112:. Retrieved
1107:
1098:
1086:. Retrieved
1071:
1064:
1052:. Retrieved
1047:
1037:
1025:. Retrieved
1021:the original
1016:
1007:
995:. Retrieved
990:
981:
969:. Retrieved
965:the original
959:Edwards, M.
954:
943:. Retrieved
939:
929:
915:
901:
887:
867:
860:
832:
825:
792:
788:
778:
767:. Retrieved
763:
750:
727:
721:
686:
636:
626:
614:. Retrieved
583:
557:. Retrieved
553:
528:the original
517:
446:
444:
433:Dutch police
430:
422:
415:
409:
402:
390:
385:
377:
375:
365:
361:
350:
339:
318:
303:
294:SQL database
287:
271:
264:
248:
236:
230:
226:
218:
215:
210:
198:
194:
190:open proxies
180:
171:
158:
147:
146:
136:
135:
122:
121:
115:
114:
100:
90:
89:
83:
82:
71:
58:
41:
20:
18:
2042:Macro virus
2027:iOS malware
2001:Web threats
1961:Infostealer
1878:Concealment
1537:www.nea.com
1048:SourceForge
795:(5): 9–17.
548:Provos, N.
483:HoneyMonkey
463:Canary trap
2159:Categories
2066:Protection
1981:Ransomware
1946:Fleeceware
1567:2015-07-31
1542:2020-08-07
1500:1153022947
1476:2020-08-07
1355:2023-06-24
1276:2023-06-24
1114:2022-10-14
945:2023-12-05
769:2017-08-09
488:Honeytoken
386:honey farm
356:Honey nets
326:Fred Cohen
255:Email trap
201:IP address
1991:Scareware
1941:Crimeware
1333:226228191
1180:206485737
1172:1558-4046
809:1089-7801
431:In 2017,
378:honey net
237:smtpot.py
221:anti-spam
148:Sugarcane
95:black hat
68:frequent.
2170:Spamming
2139:Honeypot
2098:Firewall
1885:Backdoor
1768:Archived
1672:Pitt.edu
1521:: 19–25.
1436:. 2005.
1348:HoneyPLC
1254:14996905
971:11 March
713:15382890
663:15759542
616:29 April
611:12724269
559:29 April
457:See also
278:spammers
267:spamtrap
261:Spamtrap
182:Spammers
131:Honeynet
64:hardware
21:honeypot
1996:Spyware
1905:Rootkit
1834:Malware
1596:14 June
1416:14 June
1410:All.net
1088:14 June
1054:14 June
1027:14 June
997:14 June
817:1271662
764:acm.org
426:cracker
399:History
1971:Malbot
1936:Botnet
1931:Adware
1836:topics
1747:
1722:
1682:12 Sep
1624:19 Mar
1498:
1448:
1412:. 2013
1388:
1370:Cowrie
1331:
1321:
1269:Conpot
1252:
1242:
1178:
1170:
1079:
875:
848:
815:
807:
738:
711:
701:
661:
651:
609:
599:
554:USENIX
503:Tarpit
473:Cowrie
447:medved
247:. The
241:Python
142:Honeyd
1652:3 Feb
1643:(PDF)
1615:(PDF)
1329:S2CID
1250:S2CID
1176:S2CID
813:S2CID
760:(PDF)
709:S2CID
659:S2CID
607:S2CID
440:Hansa
336:Risks
55:Types
23:is a
1745:ISBN
1720:ISBN
1684:2014
1654:2021
1626:2023
1598:2013
1496:OCLC
1446:ISBN
1418:2013
1386:ISBN
1319:ISBN
1240:ISBN
1168:ISSN
1090:2013
1077:ISBN
1056:2013
1029:2013
999:2013
973:2015
873:ISBN
846:ISBN
805:ISSN
736:ISBN
699:ISBN
649:ISBN
618:2023
597:ISBN
561:2023
405:FIPS
384:. A
233:Java
205:URLs
188:and
33:data
1438:doi
1378:doi
1311:hdl
1303:doi
1232:doi
1203:doi
1160:doi
838:doi
797:doi
691:doi
641:doi
589:doi
2161::
1743:.
1739:.
1718:.
1714:.
1670:.
1645:.
1617:.
1584:.
1535:.
1517:.
1444:.
1408:.
1384:.
1327:.
1317:.
1309:.
1297:.
1248:.
1238:.
1226:.
1197:.
1174:.
1166:.
1154:.
1150:.
1106:.
1046:.
1015:.
989:.
938:.
844:.
836:.
811:.
803:.
793:20
791:.
787:.
762:.
730:.
707:.
697:.
685:.
671:^
657:.
647:.
635:.
605:.
595:.
569:^
552:.
536:^
453:.
442:.
420:.
133:.
1826:e
1819:t
1812:v
1753:.
1728:.
1686:.
1656:.
1628:.
1600:.
1570:.
1545:.
1502:.
1479:.
1454:.
1440::
1420:.
1394:.
1380::
1335:.
1313::
1305::
1256:.
1234::
1211:.
1205::
1182:.
1162::
1156:9
1117:.
1092:.
1058:.
1031:.
1001:.
975:.
948:.
881:.
854:.
840::
819:.
799::
772:.
744:.
715:.
693::
665:.
643::
620:.
591::
563:.
245:C
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.