20:
362:
380:
392:
734:
object; Removal of
Attribute Index; Support for tokenization; NIST Key Type attribute; Fixed length Unique Identifiers; Several new attributes and query extensions; Delegated Logins; Hashed Passwords; Multiple Unique ID placeholders; ReEncrypt support using data references; Set Attribute operation;
329:
technical committee. It is the stated objective of both the PKCS#11 and KMIP committees to align the standards where practical. For example, the PKCS#11 Sensitive and
Extractable attributes are being added to KMIP version 1.4. Many of the same people are on the technical committees of both KMIP and
217:
KMIP is a stateless protocol in which messages are sent from a client to a server and then the client normally awaits on a reply. Each request may contain many operations thus enables the protocol to efficiently handle large numbers of keys. There are also advanced features for processing requests
642:
Documentation is freely available from the OASIS website. This includes the formal technical specification and a usage guide to assist people that are unfamiliar with the specification. A substantial library of test cases is also provided. These are used to test the interoperability of clients and
717:
Better asynchronous operations; Import/export of keys to other servers; Support of PKCS #12; Standardized key wrapping; Certify
Attributes; Client & Server Correlation Values; Descriptive Attributes; AEAD support; AES-XTS support; Create Secret Data; RSA PSS Support; Many extensions to Query.
172:
Re-Key, creating a new key that can replace an existing key. There are also attributes that can be used to have the server automatically rotate keys after a given period or number of uses. The Name is moved to the new key and is normally used to retrieve a key for protection operations such as
101:
which can be used for storing metadata about their keys. Some attributes are derived directly from the Value, like the cryptographic-algorithm and key-length. Other attributes are defined in the specification for the management of objects like the
Application-Specific Identifier which is usually
208:
Operations are provided for manipulating Key-state in conformance with the NIST life-cycle guidelines. A Key-state may be interrogated using the State attribute or the attributes that record dates of each transformation such as
Activation Date. Dates can be specified into the future thus keys
125:
Public and
Private Keys used for asymmetric-algorithms like RSA and ECDH. Separate objects are used for storing the public and private key, thus a user may have permission to access one but not the other. Related objects usually contain Link attributes containing the other object's unique
89:
like symmetric and asymmetric keys, certificates, and user defined objects. Clients then use the protocol for accessing these objects subject to a security model that is implemented by the servers. Operations are provided to create, locate, retrieve and update managed objects.
729:
Removal of deprecated items; Efficient representation of attributes; Replacement of "x-" convention for custom attributes; Client Log operation; Date Time resolution 1 microsecond; Locate
Destroyed; Better Error Handling and Result Reasons; Improved client Provisioning; new
259:
User objects can be created and authorized to perform specific operations on specific managed objects. Both
Managed Objects and Users can be assigned to groups, and those groups can form a hierarchy which facilitates efficient management of complex operating environments.
407:
The following shows the XML encoding of a request to Locate a key named "MyKeyName" and return its value wrapped in a different key with ID "c6d14516-4d38-0644-b810-1913b9aef4da". (TTLV is a more common wire protocol, but XML is more human readable.)
757:
Add an explicit concept of KMIP users, modeled as System
Objects; Lifecycle improvements to references to other objects using names as well as unique identifiers; Formalize object groups and hierarchies; Obliterate administrative operation;
275:
block chaining. A client then only needs to specify that they wish to create a "SecretAgent" key to have those defaults provided. It is also possible to enforce constraints on key parameters that implement security policy.
247:
protocol in order to ensure integrity and security. However, it is also possible to register and retrieve keys that are wrapped (encrypted) using another key on the server, which provides an additional level of security.
266:
Default values of attributes can be provided, so that simple clients need not specify cryptographic and other parameters. For example, an administrative user might specify that all "SecretAgent" keys should be 192 bit
333:
KMIP 2.0 provides a standardized mechanism to transport PKCS#11 messages from clients to servers. This can be used to target different PKCS#11 implementations without the need to recompile the programs that use it.
105:
Each object is identified by a unique and immutable object-identifier generated by the server and is used for getting object-values. Managed-objects may also be given a number of mutable yet globally unique
318:. PKCS#11 provides cryptographic operations to encrypt and decrypt, as well as operations for simple key management. There is considerable amount of overlap between the PKCS#11 API and the KMIP protocol.
369:
Vendors demonstrate interoperability during a process organized by the OASIS KMIP technical committee in the months before each RSA security conference. These demonstrations are informally known as
205:(NIST). Keys are created in an Initial state, and must be Activated before they can be used. Keys may then be Deactivated and eventually Destroyed. A key may also be marked being Compromised.
182:
Encrypt, Decrypt, MAC etc. Cryptographic operations performed on the key management server. A key itself could be marked being not-Extractable, in which case its value never leaves the server.
379:
70:
keys are supported, including the ability to sign certificates. KMIP also allows for clients to ask a server to encrypt or decrypt data, without needing direct access to the key.
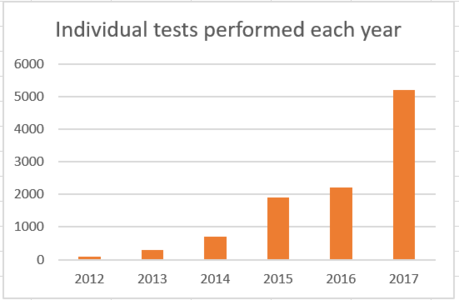
373:. KMIP interops have been held every year since 2010. The following chart shows the number of individual tests performed by each client and server vendor combination since 2012.
160:
Get, retrieving an object's value given its unique identifier. The returned value may be wrapped (encrypted) with another key that is on the server for additional security.
746:
Ping; Process and query asynchronous requests; Standardize server side key rotation; Set and query attribute defaults; Set and query constraints on attributes;
296:
has put forth various profiles describing the requirements for compliance towards storage arrays and tape libraries, but any organization can create a profile.
73:
The KMIP standard was first released in 2010. Clients and servers are commercially available from multiple vendors. The KMIP standard effort is governed by the
173:
encrypt and sign. The old key can also be retrieved using the Unique
Identifier for process operations such as decryption and signature verification.
202:
189:
166:
Add Attributes, Get Attributes, Modify Attributes and Set Attribute. These can be used to manipulate mutable attributes of a managed object.
288:, which are subsets of the KMIP specification showing common usage for a particular context. A particular KMIP implementation is said to be
391:
695:
Cryptographic Operations (Encrypt, Decrypt, Sign etc.). Introduction of Profiles, including Application Identifiers for tape libraries.
236:
There are also well defined XML and JSON encodings of the protocol for environments where binary is not appropriate. A very compact
831:
62:
by simplifying encryption key management. Keys may be created on a server and then retrieved, possibly wrapped by other keys. Both
256:
KMIP provides standardized mechanisms to manage a KMIP server by suitably authorized administrative clients using System Objects.
263:
KMIP also provides a provisioning system that facilitates providing end points with credentials using simple one time passwords.
817:
102:
derived from tape-identification data. Additional identifiers can be defined by the server or client per application need.
926:
229:(tag, type, length, value). Nested TTLV structures allow for encoding of complex, multi-operation messages in a single
873:
859:
916:
706:
Streaming Cryptographic Operations; Client Registration; Locate offset/Limit; Deprecate Templates; RNG queries;
941:
272:
936:
845:
354:
The KMIP standard is defined using a formal specification document, testcases, and profiles put forth by the
342:
The OASIS KMIP Technical Committee maintains a list of known KMIP implementations, which can be found on the
132:
Split Keys, with each split being a distinct object that can be managed independently from the other splits.
268:
731:
222:
931:
791:
315:
244:
292:
to a profile when it fulfills all the requirements set forth in a profile specification document.
921:
67:
63:
385:
Individual interoperability tests performed by each server/client vendor combination since 2012
308:
47:
643:
servers, but they also provide concrete examples of the usage of each standard KMIP feature.
365:
Interop booths at the 2015 RSA conference. Each vendor interoperates with each other vendor.
899:
343:
355:
326:
293:
74:
24:
8:
154:
Create, creating a new managed object such as a symmetric key, and return the identifier.
358:
KMIP technical committee. These documents are publicly available on the OASIS website.
51:
19:
221:
The KMIP protocol specifies several different types of encodings. The main one is a
346:. As of March 2017, there are 28 implementations and 61 KMIP products in this list.
321:
The two standards were originally developed independently. PKCS#11 was created by
946:
97:
like a key-block containing a cryptographic-key. These objects comprise mutable
77:. Technical details can also be found on the official KMIP page and kmip wiki.
55:
28:
910:
891:
209:
automatically become unavailable for specified operations when they expire.
361:
322:
230:
846:"OASIS Key Management Interoperability Protocol (KMIP) TC | OASIS"
792:"OASIS Key Management Interoperability Protocol (KMIP) TC | OASIS"
770:
59:
44:
157:
Create Key Pair, creating two objects that represent asymmetric keys.
818:"KMIP Storage Array with Self-Encrypting Drives Profile Version 1.0"
804:
304:
16:
Communication protocol for the manipulation of cryptographic keys
243:
All of these protocols are expected to be transmitted using
240:
encoding is also provided for applications that require it.
118:
The types of managed-objects being managed by KMIP include:
349:
237:
169:
Locate, retrieving a list of objects based on a predicates.
311:
185:
Export and Import keys to and from other KMIP servers.
138:
Opaque Data for client and server defined extensions.
50:
that defines message formats for the manipulation of
163:
Register, storing an externally generated key value.
397:
Results of 2017 OASIS KMIP interoperability testing
201:Each key has a cryptographic state defined by the
110:attribute which can be used for Locating objects.
908:
614:"c6d14516-4d38-0644-b810-1913b9aef4da"
325:, but the standard is now also governed by an
203:National Institute of Standards and Technology
122:Symmetric-Keys used for algorithms like AES.
900:"KMIP Implementations known to the KMIP TC"
93:Each managed object comprises an immutable
299:
150:The operations provided by KMIP include:
360:
350:Interoperability between implementations
37:Key Management Interoperability Protocol
18:
832:"KMIP Tape Library Profile Version 1.0"
652:Summary of KMIP versions and features.
337:
176:(Re-)Certify - certifies a certificate.
909:
251:
212:
13:
646:
85:A KMIP server stores and controls
14:
958:
884:
773:Security in Storage Working Group
623:</KeyWrappingSpecification>
620:</EncryptionKeyInformation>
196:
892:"OASIS KMIP Technical Committee"
805:https://wiki.oasis-open.org/kmip
637:
599:<EncryptionKeyInformation>
578:<KeyWrappingSpecification>
390:
378:
279:
135:Secret Data, such as passwords.
874:"KMIP Specification v3.0 WD09"
866:
860:"KMIP Specification v2.1 WD07"
852:
838:
824:
810:
798:
784:
80:
58:server. This facilitates data
1:
777:
225:encoding of messages, called
145:
141:Certificate Signing Requests.
188:Operations to implement the
7:
764:
650:
284:KMIP also defines a set of
179:Split and Join N of M keys.
10:
963:
402:
129:Certificates and PGP Keys.
113:
927:Public key infrastructure
27:2017 interop at the 2017
735:PKCS #11 encapsulation.
458:</ProtocolVersion>
440:<ProtocolVersionMinor
422:<ProtocolVersionMajor
410:
316:hardware security module
917:Cryptographic protocols
632:</RequestMessage>
626:</RequestPayload>
587:"Enumeration"
545:"Enumeration"
530:</RequestPayload>
473:"Enumeration"
419:<ProtocolVersion>
300:Relationship to PKCS#11
575:<RequestPayload>
563:"ByteString"
515:"TextString"
503:<RequestPayload>
491:"ByteString"
461:</RequestHeader>
413:<RequestMessage>
366:
48:communication protocol
32:
942:Computer data storage
557:<UniqueBatchItemID
521:"MyKeyName"
485:<UniqueBatchItemID
416:<RequestHeader>
364:
22:
937:Cloud infrastructure
602:<UniqueIdentifier
338:KMIP implementations
75:OASIS standards body
23:Participants in the
653:
608:"Integer"
593:"Encrypt"
527:</Attributes>
446:"Integer"
428:"Integer"
651:
629:</BatchItem>
581:<WrappingMethod
533:</BatchItem>
506:<Attributes>
479:"Locate"
367:
314:used to control a
52:cryptographic keys
33:
762:
761:
536:<BatchItem>
464:<BatchItem>
252:System management
223:type–length–value
213:Message structure
954:
903:
895:
878:
877:
870:
864:
863:
856:
850:
849:
842:
836:
835:
828:
822:
821:
814:
808:
802:
796:
795:
788:
674:Initial version
660:Committee Draft
654:
633:
630:
627:
624:
621:
618:
615:
612:
609:
606:
603:
600:
597:
594:
591:
588:
585:
582:
579:
576:
573:
570:
567:
564:
561:
558:
555:
552:
549:
546:
543:
540:
537:
534:
531:
528:
525:
522:
519:
516:
513:
510:
507:
504:
501:
498:
495:
492:
489:
486:
483:
480:
477:
474:
471:
468:
465:
462:
459:
456:
453:
450:
447:
444:
441:
438:
435:
432:
429:
426:
423:
420:
417:
414:
394:
382:
218:asynchronously.
962:
961:
957:
956:
955:
953:
952:
951:
932:Disk encryption
907:
906:
898:
890:
887:
882:
881:
872:
871:
867:
858:
857:
853:
844:
843:
839:
830:
829:
825:
816:
815:
811:
803:
799:
790:
789:
785:
780:
767:
649:
647:Version history
640:
635:
634:
631:
628:
625:
622:
619:
616:
613:
610:
607:
604:
601:
598:
595:
592:
589:
586:
583:
580:
577:
574:
571:
568:
565:
562:
559:
556:
553:
551:"Get"
550:
547:
544:
541:
538:
535:
532:
529:
526:
523:
520:
517:
514:
511:
508:
505:
502:
499:
496:
493:
490:
487:
484:
481:
478:
475:
472:
469:
466:
463:
460:
457:
454:
451:
448:
445:
442:
439:
436:
433:
430:
427:
424:
421:
418:
415:
412:
405:
398:
395:
386:
383:
352:
340:
302:
282:
254:
215:
199:
192:key life cycle.
148:
116:
87:Managed Objects
83:
17:
12:
11:
5:
960:
950:
949:
944:
939:
934:
929:
924:
922:Key management
919:
905:
904:
896:
886:
885:External links
883:
880:
879:
865:
851:
837:
823:
809:
797:
782:
781:
779:
776:
775:
774:
766:
763:
760:
759:
755:
752:
748:
747:
744:
741:
737:
736:
727:
724:
720:
719:
715:
712:
708:
707:
704:
701:
697:
696:
693:
690:
686:
685:
683:
680:
676:
675:
672:
669:
665:
664:
663:Main Features
661:
658:
648:
645:
639:
636:
411:
404:
401:
400:
399:
396:
389:
387:
384:
377:
351:
348:
339:
336:
301:
298:
281:
278:
253:
250:
231:binary message
214:
211:
198:
197:Key life cycle
195:
194:
193:
186:
183:
180:
177:
174:
170:
167:
164:
161:
158:
155:
147:
144:
143:
142:
139:
136:
133:
130:
127:
123:
115:
112:
82:
79:
56:key management
29:RSA Conference
15:
9:
6:
4:
3:
2:
959:
948:
945:
943:
940:
938:
935:
933:
930:
928:
925:
923:
920:
918:
915:
914:
912:
901:
897:
893:
889:
888:
875:
869:
861:
855:
847:
841:
833:
827:
819:
813:
806:
801:
793:
787:
783:
772:
769:
768:
756:
753:
750:
749:
745:
742:
739:
738:
733:
728:
725:
722:
721:
716:
713:
710:
709:
705:
702:
699:
698:
694:
691:
688:
687:
684:
681:
678:
677:
673:
670:
667:
666:
662:
659:
656:
655:
644:
638:Documentation
569:"2"
539:<Operation
497:"1"
467:<Operation
452:"0"
434:"3"
409:
393:
388:
381:
376:
375:
374:
372:
363:
359:
357:
347:
345:
344:OASIS website
335:
331:
328:
324:
319:
317:
313:
310:
306:
297:
295:
291:
287:
280:KMIP profiles
277:
274:
270:
264:
261:
257:
249:
246:
241:
239:
234:
232:
228:
224:
219:
210:
206:
204:
191:
187:
184:
181:
178:
175:
171:
168:
165:
162:
159:
156:
153:
152:
151:
140:
137:
134:
131:
128:
124:
121:
120:
119:
111:
109:
103:
100:
96:
91:
88:
78:
76:
71:
69:
65:
61:
57:
53:
49:
46:
42:
38:
30:
26:
21:
868:
854:
840:
826:
812:
800:
786:
641:
406:
370:
368:
353:
341:
332:
323:RSA Security
320:
303:
289:
285:
283:
265:
262:
258:
255:
242:
235:
226:
220:
216:
207:
200:
149:
117:
107:
104:
98:
94:
92:
86:
84:
72:
40:
36:
34:
126:identifier.
81:Description
911:Categories
778:References
771:IEEE P1619
290:conformant
271:keys with
146:Operations
99:Attributes
68:asymmetric
60:encryption
45:extensible
692:Jun 2014
682:Jan 2013
330:PKCS#11.
64:symmetric
765:See also
671:Oct 2010
657:Version
509:<Name
371:interops
286:profiles
43:) is an
403:Example
305:PKCS#11
114:Objects
947:Backup
611:value=
590:value=
566:value=
548:value=
518:value=
494:value=
476:value=
449:value=
431:value=
754:2021
743:2019
726:2018
714:2016
703:2015
617:/>
605:type=
596:/>
584:type=
572:/>
560:type=
554:/>
542:type=
524:/>
512:type=
500:/>
488:type=
482:/>
470:type=
455:/>
443:type=
437:/>
425:type=
356:OASIS
327:OASIS
307:is a
294:OASIS
95:Value
54:on a
25:OASIS
807:wiki
668:1.0
238:CBOR
227:TTLV
190:NIST
108:Name
66:and
41:KMIP
35:The
751:3.0
740:2.1
732:CSR
723:2.0
711:1.4
700:1.3
689:1.2
679:1.1
312:API
273:CBC
269:AES
245:TLS
913::
233:.
902:.
894:.
876:.
862:.
848:.
834:.
820:.
794:.
309:C
39:(
31:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.