447:
89:
426:
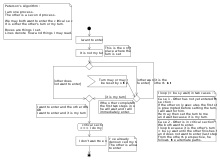
critical section next. Note that for a process or thread, the remainder sections are parts of the code that are not related to the critical section. This selection cannot be postponed indefinitely. A process cannot immediately re-enter the critical section if the other process has set its flag to say that it would like to enter its critical section.
438:, means that the number of times a process is bypassed by another process after it has indicated its desire to enter the critical section is bounded by a function of the number of processes in the system. In Peterson's algorithm, a process will never wait longer than one turn for entrance to the critical section.
450:
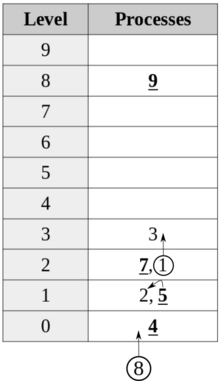
Snapshot of filter algorithm with 10 processes in progress. Last to enter are shown bold and underlined. (NB: Depending on scheduling, the last to enter may not be "correct".) At any time, updates to the table could be: the insertion of a new process at level 0, a change to the last to enter at a
425:
Progress is defined as the following: if no process is executing in its critical section and some processes wish to enter their critical sections, then only those processes that are not executing in their remainder sections can participate in making the decision as to which process will enter its
625:
instruction. Implementation of
Peterson's and related algorithms on processors that reorder memory accesses generally requires use of such operations to work correctly to keep sequential operations from happening in an incorrect order. Note that reordering of memory accesses can happen even on
665:, and other architectures. These instructions are intended to provide a way to build synchronization primitives more efficiently than can be done with pure shared memory approaches.
77:. Entrance to the critical section is granted for process P0 if P1 does not want to enter its critical section or if P1 has given priority to P0 by setting
42:
417:, so there can be no state where both processes are in their critical sections. (This recounts an argument that is made rigorous in Schneider 1997.)
621:
for types of reordering allowed). Such processors invariably give some way to force ordering in a stream of memory accesses, typically through a
446:
335:
The algorithm satisfies the three essential criteria to solve the critical-section problem. The while condition works even with preemption.
587:, until at the final level, only one process is allowed to leave the waiting room and enter the critical section, giving mutual exclusion.
462:
processes. Instead of a boolean flag, it requires an integer variable per process, stored in a single-writer/multiple-reader (SWMR) atomic
498:, each representing a distinct "waiting room" before the critical section. Processes advance from one room to the next, finishing in room
451:
given level, or a process moving up one level (if it is not the last to enter OR there are no other processes at its own level or higher).
45:
in 1981. While
Peterson's original formulation worked with only two processes, the algorithm can be generalized for more than two.
345:
can take on one of two values, it can be replaced by a single bit, meaning that the algorithm requires only three bits of memory.
865:
602:
level, Peterson's algorithm is typically not needed to achieve atomic access. Some processors have special instructions, like
845:
778:
576:
will proceed to the next room, the final one finding itself the last to enter the room. Similarly, at the next level,
826:
393:
and busy waiting). So if both processes are in their critical sections, then we conclude that the state must satisfy
679:
37:
that allows two or more processes to share a single-use resource without conflict, using only shared memory for
373:(meaning that P1 is just now trying to enter the critical section, but graciously waiting), or P1 is at label
684:
650:
689:
353:
P0 and P1 can never be in the critical section at the same time. If P0 is in its critical section, then
611:
590:
Unlike the two-process
Peterson algorithm, the filter algorithm does not guarantee bounded waiting.
694:
747:
Silberschatz. Operating
Systems Concepts: Seventh Edition. John Wiley and Sons, 2005, Page 194.
584:
27:
674:
8:
849:
846:
https://elixir.bootlin.com/linux/v5.6.19/source/arch/arm/mach-tegra/sleep-tegra20.S#L120
822:
774:
658:
599:
441:
638:
607:
463:
74:
34:
810:
618:
478:
553:
That this algorithm achieves mutual exclusion can be proven as follows. Process
622:
610:, which, by locking the memory bus, can be used to provide mutual exclusion in
565:, so another process joined its waiting room. At level zero, then, even if all
473:
additional variables in similar registers. The registers can be represented in
435:
617:
Most modern CPUs reorder memory accesses to improve execution efficiency (see
557:
exits the inner loop when there is either no process with a higher level than
484:
level : array of N integers last_to_enter : array of N − 1 integers
859:
766:
38:
603:
505:, which is the critical section. Specifically, to acquire a lock, process
848:
Example of
Peterson's algorithm formerly being used in the linux kernel (
569:
processes were to enter waiting room zero at the same time, no more than
88:
338:
The three criteria are mutual exclusion, progress, and bounded waiting.
814:
474:
654:
30:
631:
733:, January 1990 ("Proof of a Mutual Exclusion Algorithm", M Hofri).
442:
Filter algorithm: Peterson's algorithm for more than two processes
662:
627:
771:
Concurrent
Programming: Algorithms, Principles, and Foundations
542:
To release the lock upon exiting the critical section, process
716:
G. L. Peterson: "Myths About the Mutual
Exclusion Problem",
646:
455:
The filter algorithm generalizes
Peterson's algorithm to
626:
processors that don't reorder instructions (such as the
377:(trying to enter its critical section, after setting
16:
Concurrent programming algorithm for mutual exclusion
365:(meaning that P1 has left its critical section), or
743:
741:
739:
637:Most such CPUs also have some sort of guaranteed
857:
736:
536:there exists k ≠ i, such that level ≥ ℓ
809:
787:
561:, so the next waiting room is free; or, when
712:
710:
773:. Springer Science & Business Media.
761:
759:
757:
755:
753:
445:
87:
797:, Springer Verlag, 1997, pages 185–196.
707:
858:
765:
819:The Art of Multiprocessor Programming
805:
803:
750:
528:level ← ℓ last_to_enter ← i
348:
13:
800:
429:
53:The algorithm uses two variables:
14:
877:
839:
680:Eisenberg & McGuire algorithm
48:
491:variables take on values up to
866:Concurrency control algorithms
723:
718:Information Processing Letters
1:
357:is true. In addition, either
821:. Elsevier. pp. 28–31.
700:
409:. No state can satisfy both
7:
668:
651:load-link/store-conditional
420:
69:indicates that the process
10:
882:
685:Lamport's bakery algorithm
314:// end of critical section
218:// end of critical section
795:On Concurrent Programming
98:
731:Operating Systems Review
236:
140:
99:
593:
41:. It was formulated by
452:
93:
28:concurrent programming
690:Szymański's algorithm
449:
91:
598:When working at the
434:Bounded waiting, or
92:Peterson's algorithm
20:Peterson's algorithm
720:12(3) 1981, 115–116
385:but before setting
308:// critical section
212:// critical section
73:wants to enter the
24:Peterson's solution
675:Dekker's algorithm
532:last_to_enter = i
453:
94:
793:F. B. Schneider,
630:processor in the
563:i ≠ last_to_enter
333:
332:
873:
833:
832:
811:Herlihy, Maurice
807:
798:
791:
785:
784:
763:
748:
745:
734:
729:As discussed in
727:
721:
714:
644:
639:atomic operation
608:compare-and-swap
582:
575:
568:
564:
560:
556:
549:
545:
508:
504:
497:
490:
472:
461:
416:
412:
408:
404:
400:
396:
392:
388:
384:
380:
376:
372:
368:
364:
360:
356:
349:Mutual exclusion
344:
327:
324:
321:
318:
315:
312:
309:
306:
303:
300:
297:
294:
291:
288:
285:
282:
279:
276:
273:
270:
267:
264:
261:
258:
255:
252:
249:
246:
243:
240:
231:
228:
225:
222:
219:
216:
213:
210:
207:
204:
201:
198:
195:
192:
189:
186:
183:
180:
177:
174:
171:
168:
165:
162:
159:
156:
153:
150:
147:
144:
133:
130:
127:
124:
121:
118:
115:
112:
109:
106:
103:
96:
95:
84:
80:
75:critical section
72:
68:
64:
60:
56:
43:Gary L. Peterson
35:mutual exclusion
881:
880:
876:
875:
874:
872:
871:
870:
856:
855:
842:
837:
836:
829:
808:
801:
792:
788:
781:
764:
751:
746:
737:
728:
724:
715:
708:
703:
671:
649:processors and
642:
619:memory ordering
596:
577:
570:
566:
562:
558:
554:
547:
543:
540:
506:
499:
492:
488:
485:
467:
456:
444:
432:
430:Bounded waiting
423:
414:
410:
406:
402:
398:
394:
390:
386:
382:
378:
374:
370:
366:
362:
358:
354:
351:
342:
329:
328:
325:
322:
319:
316:
313:
310:
307:
304:
301:
298:
295:
292:
289:
286:
283:
280:
277:
274:
271:
268:
265:
262:
259:
256:
253:
250:
247:
244:
241:
238:
233:
232:
229:
226:
223:
220:
217:
214:
211:
208:
205:
202:
199:
196:
193:
190:
187:
184:
181:
178:
175:
172:
169:
166:
163:
160:
157:
154:
151:
148:
145:
142:
135:
134:
131:
128:
125:
122:
119:
116:
113:
110:
107:
104:
101:
82:
78:
70:
66:
62:
58:
54:
51:
17:
12:
11:
5:
879:
869:
868:
854:
853:
841:
840:External links
838:
835:
834:
827:
799:
786:
780:978-3642320279
779:
767:Raynal, Michel
749:
735:
722:
705:
704:
702:
699:
698:
697:
692:
687:
682:
677:
670:
667:
623:memory barrier
595:
592:
583:will proceed,
581: − 2
574: − 1
512:i ← ProcessNo
511:
503: − 1
496: − 1
483:
471: − 1
443:
440:
436:bounded bypass
431:
428:
422:
419:
350:
347:
331:
330:
237:
234:
141:
137:
136:
100:
50:
47:
15:
9:
6:
4:
3:
2:
878:
867:
864:
863:
861:
851:
847:
844:
843:
830:
828:9780123977953
824:
820:
816:
812:
806:
804:
796:
790:
782:
776:
772:
768:
762:
760:
758:
756:
754:
744:
742:
740:
732:
726:
719:
713:
711:
706:
696:
693:
691:
688:
686:
683:
681:
678:
676:
673:
672:
666:
664:
660:
656:
652:
648:
640:
635:
633:
629:
624:
620:
615:
613:
609:
605:
601:
591:
588:
586:
580:
573:
551:
539:
535:
531:
527:
523:
519:
515:
510:
502:
495:
482:
480:
476:
470:
465:
459:
448:
439:
437:
427:
418:
346:
339:
336:
235:
139:
138:
97:
90:
86:
76:
49:The algorithm
46:
44:
40:
39:communication
36:
32:
29:
25:
21:
818:
794:
789:
770:
730:
725:
717:
636:
616:
604:test-and-set
597:
589:
578:
571:
552:
541:
537:
533:
529:
525:
521:
517:
513:
500:
493:
486:
468:
457:
454:
433:
424:
352:
340:
337:
334:
302:// busy wait
206:// busy wait
52:
23:
19:
18:
815:Shavit, Nir
695:Semaphores
641:, such as
475:pseudocode
284:&&
188:&&
852:in v5.7).
701:Footnotes
614:systems.
526:exclusive
509:executes
65:value of
31:algorithm
860:Category
817:(2012).
769:(2012).
669:See also
632:Xbox 360
600:hardware
464:register
421:Progress
415:turn = 1
411:turn = 0
407:turn = 1
403:turn = 0
850:removed
663:PowerPC
628:PowerPC
550:to −1.
375:P1_gate
257:P1_gate
161:P0_gate
26:) is a
825:
777:
524:N − 1
479:arrays
466:, and
460:> 2
341:Since
655:Alpha
559:level
548:level
546:sets
530:while
489:level
363:false
323:false
275:while
227:false
179:while
120:false
114:false
823:ISBN
775:ISBN
659:MIPS
643:XCHG
594:Note
585:etc.
538:wait
518:from
487:The
413:and
405:and
401:and
399:flag
397:and
395:flag
387:turn
383:true
379:flag
367:turn
359:flag
355:flag
343:turn
317:flag
287:turn
281:flag
263:turn
251:true
245:flag
221:flag
191:turn
185:flag
167:turn
155:true
149:flag
129:turn
105:flag
102:bool
79:turn
67:true
63:flag
61:. A
59:turn
57:and
55:flag
33:for
22:(or
653:on
647:x86
645:on
634:).
612:SMP
606:or
534:and
514:for
477:as
389:to
381:to
369:is
361:is
311:...
215:...
126:int
81:to
862::
813:;
802:^
752:^
738:^
709:^
661:,
657:,
522:to
520:0
516:ℓ
481::
290:==
239:P1
194:==
143:P0
123:};
85:.
831:.
783:.
579:N
572:N
567:N
555:i
544:i
507:i
501:N
494:N
469:N
458:N
391:0
371:0
326:;
320:=
305:}
299:{
296:)
293:0
278:(
272:;
269:0
266:=
260::
254:;
248:=
242::
230:;
224:=
209:}
203:{
200:)
197:1
182:(
176:;
173:1
170:=
164::
158:;
152:=
146::
132:;
117:,
111:{
108:=
83:0
71:n
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.