666:
1395:
636:
1304:) worked on dynamic face recognition. The research focused primarily on the extraction of body biometric features from video and identifying subjects from those features. To conduct its studies, the university created databases of synchronized multi-camera video sequences of body motion, human faces under a wide range of imaging conditions, AU coded expression videos, and hyperspectal and polarimetric images of faces. The video sequences of body motion data consisted of six separate viewpoints of 25 subjects walking on a treadmill. Four separate 11-second gaits were tested for each: slow walk, fast walk, inclined, and carrying a ball.
646:
656:
626:
69:
55:
1204:
720:
616:
27:
696:
708:
1109:. "Effective analysis across heterogenous databases" means the ability to take things from databases which are designed to store different types of data—such as a database containing criminal records, a phone call database and a foreign intelligence database. The Web is considered an "unstructured public data source" because it is publicly accessible and contains many different types of data—blogs, emails, records of visits to websites, etc.—all of which need to be analyzed and stored efficiently.
1294:. Gait recognition was a key component of HumanID, because it could be employed on low-resolution video feeds and therefore help identify subjects at a distance. They planned to develop a system that recovered static body and stride parameters of subjects as they walked, while also looking into the ability of time-normalized joint angle trajectories in the walking plane as a way of recognizing gait. The university also worked on finding and tracking faces by expressions and speech.
732:
763:
1237:
751:
676:
1344:
1093:
43:
1134:
1465:(SAIC) a $ 19 million contract to develop the "Information Awareness Prototype System", the core architecture to integrate all of TIA's information extraction, analysis, and dissemination tools. This was done through its consulting arm, Hicks & Associates, which employed many former Defense Department and military officials.
1416:
was first coined at the 1999 annual DARPAtech conference in a presentation by the deputy director of the Office of
Information Systems Management, Brian Sharkey. Sharkey applied the phrase to a conceptual method by which the government could sift through massive amounts of data becoming available via
1781:
Poindexter and his office proved to be more polarizing than expected; its Total
Information Awareness programme (later changed to Terrorism Information Awareness), which aimed to sift through huge amounts of data to track terrorists, was attacked on privacy grounds, and Congress eventually cancelled
1491:
The report arrived on May 20. It disclosed that the program's computer tools were still in their preliminary testing phase. Concerning the pattern recognition of transaction information, only synthetic data created by researchers was being processed. The report also conceded that a full prototype of
1149:
EELD was designed to design systems with the ability to extract data from multiple sources (e.g., text messages, social networking sites, financial records, and web pages). It was to develop the ability to detect patterns comprising multiple types of links between data items or communications (e.g.,
1385:
and policies, and report misuses of data. There were also plans for TIA to have an application that could "anonymize" data, so that information could be linked to an individual only by court order (especially for medical records gathered by the bio-surveillance project). A set of audit logs were to
1355:
by monitoring non-traditional data sources such as animal sentinels, behavioral indicators, and pre-diagnostic medical data. It would leverage existing disease models, identify abnormal health early indicators, and mine existing databases to determine the most valuable early indicators for abnormal
1066:
to assist human analysts. It was designed to support both top-down and bottom-up approaches; a policymaker could hypothesize an attack and use Genoa to look for supporting evidence of it or compile pieces of intelligence into a diagram and suggest possible outcomes. Human analysts could then modify
2986:
On the Web site of this particular program, the Total
Information Awareness Program, they cite a Latin slogan—"Knowledge is power"—something we would all agree with, and state: The total information awareness of transnational threats requires keeping track of individuals and understanding how they
2038:
The most widely reported data-mining project—the
Pentagon's Total Information Awareness (TIA) program—was shut down by Congress because of widespread privacy fears. The project sought to use credit-card, medical and travel records to search for terrorists and was dubbed by privacy advocates as a
1220:
speech, which is much more complex due to an essentially unlimited vocabulary and grammar, Communicator takes on task-specific issues so that there are constrained vocabularies (the system only needs to be able to understand language related to war). Research was also started on foreign-language
1211:
Communicator was to develop "dialogue interaction" technology to enable warfighters to talk to computers, such that information would be accessible on the battlefield or in command centers without a keyboard-based interface. Communicator was to be wireless, mobile, and to function in a networked
1215:
The dialogue interaction software was to interpret dialogue's context to improve performance, and to automatically adapt to new topics so conversation could be natural and efficient. Communicator emphasized task knowledge to compensate for natural language effects and noisy environments. Unlike
1534:
for the 2004 fiscal year, a classified annex provided the funding. It was stipulated that the technologies were limited for military or foreign intelligence purposes against non-U.S. citizens. Most of the original project goals and research findings were preserved, but the privacy protection
1364:
As a "virtual, centralized, grand database", the scope of surveillance included credit card purchases, magazine subscriptions, web browsing histories, phone records, academic grades, bank deposits, gambling histories, passport applications, airline and railway tickets, driver's licenses, gun
1158:
Wargaming the asymmetric environment (WAE) focused on developing automated technology that could identify predictive indicators of terrorist activity or impending attacks by examining individual and group behavior in broad environmental context and the motivation of specific terrorists.
1112:
Another goal was to develop "a large, distributed system architecture for managing the huge volume of raw data input, analysis results, and feedback, that will result in a simpler, more flexible data store that performs well and allows us to retain important data indefinitely".
1104:
technology at the time was insufficient for storing and organizing such enormous quantities of data. So they developed techniques for virtual data aggregation to support effective analysis across heterogeneous databases, as well as unstructured public data sources, such as the
1326:
was compiling a database to test facial systems. The data included a set of nine static pictures taken from different viewpoints, a video of each subject looking around a room, a video of the subject speaking, and one or more videos of the subject showing facial expressions.
1608:
The
Information Awareness Prototype System was reclassified as "Basketball" and work on it continued by SAIC, supervised by ARDA. As late as September 2004, Basketball was fully funded by the government and being tested in a research center jointly run by ARDA and SAIC.
2987:
fit into models. To this end, this office would seek to develop a way to integrate databases into a "virtual centralized grand database". They would be in a position to look at education, travel, and medical records, and develop risk profiles for millions of
Americans
1167:
Translingual information detection, extraction and summarization (TIDES) developed advanced language processing technology to enable
English speakers to find and interpret critical information in multiple languages without requiring knowledge of those languages.
1141:
Evidence extraction and link discovery (EELD) developed technologies and tools for automated discovery, extraction and linking of sparse evidence contained in large amounts of classified and unclassified data sources (such as phone call records from the
1380:
TIA's
Genisys component, in addition to integrating and organizing separate databases, was to run an internal "privacy protection program". This was intended to restrict analysts' access to irrelevant information on private U.S. citizens, enforce
1150:
financial transactions, communications, travel, etc.). It is designed to link items relating potential "terrorist" groups and scenarios, and to learn patterns of different groups or scenarios to identify new organizations and emerging threats.
1041:
Supported collaboration, analytical reasoning and information sharing so that analysts could hypothesize, test and propose theories and mitigating strategies, so decision-makers could effectively evaluate the impact of policies and courses of
852:
Although the program was formally suspended, other government agencies later adopted some of its software with only superficial changes. TIA's core architecture continued development under the code name "Basketball". According to a 2012
830:, TIA was meant to correlate detailed information about people in order to anticipate and prevent terrorist incidents before execution. The program modeled specific information sets in the hunt for terrorists around the globe. Admiral
1513:
On
September 30, 2003, Congress officially cut off TIA's funding and the Information Awareness Office (with the Senate voting unanimously against it) because of its unpopular perception by the general public and the media. Senators
1024:
TIA's goal was to revolutionize the United States' ability to detect, classify and identify foreign terrorists and decipher their plans, thereby enabling the U.S. to take timely action to preempt and disrupt terrorist activity.
1449:
division of DARPA, which managed TIA's development. The office temporarily operated out of the fourth floor of DARPA's headquarters, while
Poindexter looked for a place to permanently house TIA's researchers. Soon
1472:. Groove made it possible for analysts from many different agencies to share intelligence data instantly, and linked specialized programs that were designed to look for patterns of suspicious behavior.
1488:
passed in February, the Defense Department was given 90 days to compile a report laying out a schedule of TIA's development and the intended use of allotted funds or face a cutoff of support.
1100:
Genisys aimed to develop technologies that would enable "ultra-large, all-source information repositories". Vast amounts of information were to be collected and analyzed, and the available
1315:
and five-degree-of-freedom cameras. Tests included filming 38 male and 6 female subjects of different ethnicities and physical features walking along a T-shaped path from various angles.
849:
Congress defunded the Information Awareness Office in late 2003 after media reports criticized the government for attempting to establish "Total Information Awareness" over all citizens.
373:
1084:
While Genoa primarily focused on intelligence analysis, Genoa II aimed to provide means by which computers, software agents, policymakers, and field operatives could collaborate.
2152:"Report to Congress Regarding the Terrorism Information Awareness Program: In response to Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, § 111(b)"
2970:
1248:
identification technologies to detect, recognize and identify humans at great distances for "force protection", crime prevention, and "homeland security/defense" purposes.
1441:, he was working with Syntek Technologies, a company often contracted out by the government for work on defense projects. TIA was officially commissioned during the 2002
1484:
voted to limit TIA by restricting its ability to gather information from emails and the commercial databases of health, financial and travel companies. According to the
553:
1503:
began installing access nodes on TIA's classified network. The NSA then started running stacks of emails and intercepted communications through TIA's various programs.
3196:
419:
1656:
launched a campaign to terminate TIA's implementation, claiming that it would "kill privacy in America" because "every aspect of our lives would be catalogued". The
755:
1690:, TIA is portrayed as a UK-based surveillance database that can be used to track and monitor anybody by putting all available government information in one place.
1322:'s Department of Electronics and Computer Science was developing an "automatic gait recognition" system and was in charge of compiling a database to test it. The
338:
543:
2724:
3545:
2323:
1782:
it. "That was a dishonest misuse of DARPA," says Hans Mark, a former director of defense research and engineering now at the University of Texas at Austin.
1287:
2794:. Advanced Sciences and Technologies for Security Applications. Vol. 1 (illustrated ed.). Springer Science & Business Media. p. 283.
520:
2939:
665:
3496:
1038:
Automatically queued analysts based on partial pattern matches and had patterns that covered 90% of all previously known foreign terrorist attacks
3535:
1567:
1462:
958:
3130:
1530:
Reports began to emerge in February 2006 that TIA's components had been transferred to the authority of the NSA. In the Department of Defense
899:
communities. These components consisted of information analysis, collaboration, decision-support tools, language translation, data-searching,
2494:
700:
1368:
Health and biological information TIA collected included drug prescriptions, medical records, fingerprints, gait, face and iris data, and
1575:
472:
1311:'s Institute for Advanced Computer Studies' research focused on recognizing people at a distance by gait and face. Also to be used were
3260:
2628:
1547:
1301:
795:
515:
645:
736:
1593:
931:
2464:
3089:
3056:
568:
401:
391:
3170:
2594:
635:
3565:
3414:
2528:
1618:
1268:
Develop a low-power millimeter wave radar system for wide field of view detection and narrow field of view gait classification.
712:
563:
2912:
2662:
2557:
655:
625:
3560:
3016:
The Defense Department is leading the charge for what it calls Total Information Awareness, a massive database including DNA.
1559:
1009:
353:
348:
3441:
896:
888:
875:). The goal was to integrate components from previous and new government intelligence and surveillance programs, including
1265:
Develop and demonstrate a human identification system that operates out to 150 meters (500 ft) using visible imagery.
1531:
639:
548:
212:
1192:
977:
923:
3480:
3352:
3325:
3039:
2799:
2705:
2443:
2377:
2345:
2232:
2202:
2130:
2093:
1909:
1709:
1666:
1551:
2369:
Balancing Privacy & Security: The Privacy Implications of Government Data Mining Programs: Congressional Hearing
434:
241:
2019:
1925:
1062:
Unlike the other program components, Genoa predated TIA and provided a basis for it. Genoa's primary function was
615:
3555:
2736:
2057:
1546:, which focused on collaboration between machines and humans, was renamed "Topsail" and handed over to the NSA's
1283:
1001:
669:
649:
315:
131:
3570:
3418:
3141:
3100:
1653:
1579:
1555:
1386:
be kept, which would track whether innocent Americans' communications were getting caught up in relevant data.
788:
724:
217:
109:
2816:
1035:
Provided focused warnings within an hour after a triggering event occurred or an evidence threshold was passed
2859:
1954:
1574:
said that Topsail was "in the process of being canceled due to lack of funds". When asked about Topsail in a
1571:
1323:
997:
396:
251:
2284:"Outsourcing Big Brother: Office of Total Information Awareness relies on private sector to track Americans"
3178:
2920:
2565:
1446:
1405:
816:
679:
246:
35:
2694:
Bolle, Ruud M.; Connell, Jonathan; Pankanti, Sharath; Ratha, Nalini K.; Senior, Andrew W. (29 June 2013).
2283:
2291:
1217:
966:
915:
659:
629:
368:
1496:
in an attempt to stem the flow of criticism on its information-gathering practices on average citizens.
1492:
TIA would not be ready until the 2007 fiscal year. Also in May, Total Information Awareness was renamed
3550:
2732:
1685:
1617:
Critics allege that the program could be abused by government authorities as part of their practice of
1297:
1137:
Graphic displaying a simulated application of the evidence extraction and link discovery (EELD) project
1125:
to model the key characteristics of terrorist groups and discriminate them from other societal groups.
985:
170:
20:
1394:
1203:
871:
TIA was intended to be a five-year research project by the Defense Advanced Research Projects Agency (
3291:
3252:
3000:
2888:
2824:
1328:
1319:
1275:
1013:
981:
781:
3513:
1989:
1171:
Outside groups (such as universities, corporations, etc.) were invited to participate in the annual
3145:
2224:
The Pentagon's Brain: An Uncensored History of DARPA, America's Top-Secret Military Research Agency
1510:
to reward investors who predicted terrorist attacks, Poindexter resigned from office on 29 August.
1500:
860:
619:
59:
3446:
1750:
1658:
1398:
1122:
767:
454:
2502:
675:
26:
2971:"Wyden Calls For Congressional Oversight, Accountability of Total Information Awareness Office"
2766:
1507:
1438:
1308:
1005:
970:
558:
1901:
1468:
TIA's earliest version employed software called "Groove", which had been developed in 2000 by
1959:
1225:
1172:
1063:
363:
2636:
1635:
called it "the supersnoop's dream: a Total Information Awareness about every U.S. citizen".
973:, Adroit Systems, CACI Dynamic Systems, ASI Systems International, and Syntek Technologies.
68:
54:
2974:
2024:
1754:
1481:
1426:
906:
TIA research included or planned to include the participation of nine government entities:
586:
477:
3520:
3369:
3225:
2151:
1860:
8:
1714:
1642:
1332:
1255:
Develop algorithms to find and acquire subjects out to 150 meters (500 ft) in range.
1188:
1176:
989:
962:
900:
892:
827:
343:
303:
192:
126:
121:
73:
2758:
1795:
1758:
3490:
3314:
3230:
3201:
2851:
2472:
2256:
2062:
1994:
1865:
1841:
1627:
1570:
signed a $ 3.7 million contract for work on Topsail. In early 2006 a spokesman for the
1184:
993:
424:
3104:
2940:"Your city is spying on you: From iPhones to cameras, you are being watched right now"
2880:
3515:
Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, § 111(b)
3476:
3348:
3321:
3182:
3064:
3035:
2795:
2701:
2602:
2439:
2432:
2373:
2228:
2198:
2126:
1905:
1894:
1845:
1772:
1597:
1486:
Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, § 111(b)
1143:
943:
839:
835:
2536:
1822:
Murray, N. (4 October 2010). "Profiling in the age of total information awareness".
883:, Genisys, SSNA, EELD, WAE, TIDES, Communicator, HumanID and Bio-Surveillance, with
2924:
2670:
2569:
2261:
1833:
1800:
1762:
1291:
1240:
Diagram describing capabilities of the "human identification at a distance" project
1162:
1079:
880:
449:
439:
202:
197:
104:
3397:
3090:"Total Information Awareness Programs: Funding, Composition, and Oversight Issues"
2193:
The Shadow Factory: The Ultra-Secret NSA from 9/11 to the Eavesdropping on America
2191:
846:, TIA was the "biggest surveillance program in the history of the United States".
3342:
3029:
2944:
2789:
2695:
2397:
2367:
2222:
2120:
1824:
1582:
1430:
1401:
1224:
Live exercises were conducted involving small unit logistics operations with the
1070:
Genoa was independently commissioned in 1996 and completed in 2002 as scheduled.
1032:
Increased information coverage by an order of magnitude and afforded easy scaling
831:
444:
99:
2085:
1861:"Pentagon Plans a Computer System That Would Peek at Personal Data of Americans"
1271:
Characterize gait performance from video for human identification at a distance.
3540:
3374:
1673:
1632:
1589:
1106:
855:
707:
497:
942:. They were to be able to access TIA's programs through a series of dedicated
819:. It operated under this title from February to May 2003 before being renamed
3529:
3283:
3068:
2402:
2315:
1837:
1699:
1669:
1563:
1451:
1434:
1244:
The human identification at a distance (HumanID) project developed automated
1121:
Scalable social network analysis (SSNA) aimed to develop techniques based on
1057:
876:
146:
2700:(illustrated ed.). Springer Science & Business Media. p. 239.
1028:
To that end, TIA was to create a counter-terrorism information system that:
2353:
1776:
1676:
said that because of Clapper's lie he lost hope to change things formally.
1586:
1519:
1352:
947:
429:
283:
76:
as of 2007, with countries subject to the most data collection shown in red
1662:
criticized the program for "Fighting terror by terrifying U.S. citizens".
1592:
said they did not know the program's status. Negroponte's deputy, former
1445:. In January 2002 Poindexter was appointed Director of the newly created
1442:
1382:
1236:
884:
731:
487:
358:
3521:
Report to Congress Regarding the Terrorism Information Awareness Program
976:
Universities enlisted to assist with research and development included
887:
knowledge gleaned from the private sector to create a resource for the
482:
141:
1331:
developed multiple systems for identification via facial recognition.
2966:
2122:
Privacy: Total Information Awareness Programs and Latest Developments
1930:
1704:
1638:
1515:
1469:
1245:
843:
719:
686:
538:
492:
293:
273:
187:
158:
136:
1767:
1738:
1351:
The bio-surveillance project was designed to predict and respond to
2828:
2499:
Northeastern University College of Computer and Information Science
1543:
1455:
1343:
1312:
1101:
951:
927:
591:
288:
236:
1175:, topic detection and tracking, automatic content extraction, and
3415:"Q&A on the Pentagon's "Total Information Awareness" Program"
762:
320:
298:
278:
263:
182:
94:
3316:
Nothing to Hide: The False Tradeoff Between Privacy and Security
1672:
lied about a massive data collection on US citizens and others.
1163:
Translingual information detection, extraction and summarization
3031:
Counterterrorism and Cybersecurity: Total Information Awareness
1641:, a former director of defense research and engineering at the
1365:
licenses, toll records, judicial records, and divorce records.
907:
750:
695:
268:
3197:"TECHNOLOGY; Many Tools Of Big Brother Are Now Up And Running"
2763:
University of Maryland Institute for Advanced Computer Studies
42:
2349:
2162:
1646:
1622:
1506:
Following a scandal in the Department of Defense involving a
1475:
1461:
Late that year, the Information Awareness Office awarded the
1207:
Diagram describing capabilities of the "communicator" project
935:
872:
231:
1926:"Pentagon's 'Terror Information Awareness' program will end"
1896:
Spies for Hire: The Secret World of Intelligence Outsourcing
1347:
Graphic describing the goals of the bio-surveillance project
1282:
A number of universities assisted in designing HumanID. The
3034:(2, illustrated, revised ed.). Springer. p. 141.
2020:"U.S. agencies collect, examine personal data on Americans"
1259:
1180:
939:
3344:
The Cost of Counterterrorism: Power, Politics, and Liberty
1092:
19:
Not to be confused with the fictional system portrayed in
3370:"Poindexter Will Be Quitting Over Terrorism Betting Plan"
2693:
2667:
Information Awareness Office (official website -- mirror)
2599:
Information Awareness Office (official website -- mirror)
2533:
Information Awareness Office (official website -- mirror)
1369:
1128:
919:
911:
3473:
Facts and Fears: Hard Truths From A Life In Intelligence
2817:"Automatic Gait Recognition for Human ID at a Distance"
2791:
Optical and Digital Techniques for Information Security
2623:
2621:
2619:
1153:
1133:
2434:
The Watchers: The Rise of America's Surveillance State
1335:
participated in implementing HumanID in poor weather.
1221:
computer interaction for use in coalition operations.
1231:
2616:
2324:
Georgia Institute of Technology College of Computing
1262:
recognition into a 24/7 human identification system.
859:
article, TIA's legacy was "quietly thriving" at the
815:) was a mass detection program by the United States
1116:
1096:
Graphic describing the goals of the Genysis project
46:
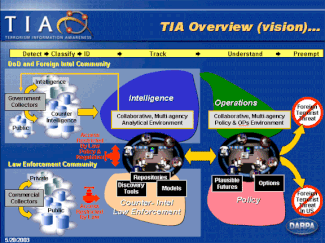
Presentation slide produced by DARPA describing TIA
3313:
2729:Carnegie Mellon University: The Robotics Institute
2657:
2655:
2653:
2459:
2457:
2455:
2431:
2190:
1893:
1433:. A former national security adviser to President
3475:(ebook ed.). New York: Viking. p. 226.
957:Companies contracted to work on TIA included the
3527:
3398:The Total Information Awareness Project Lives On
3057:"The Year in Ideas; Total Information Awareness"
2589:
2587:
1600:, said, "I'd like to answer in closed session."
1425:TIA was proposed as a program shortly after the
1228:to test the technology in extreme environments.
2937:
2650:
2633:Information Awareness Office (official website)
2523:
2521:
2519:
2469:Information Awareness Office (official website)
2452:
1952:
2759:"Human Identification at a Distance: Overview"
2725:"Human Identification at a Distance (HumanID)"
2086:"OVERVIEW OF THE INFORMATION AWARENESS OFFICE"
1987:
1463:Science Applications International Corporation
1274:Develop a multi-spectral infrared and visible
959:Science Applications International Corporation
521:Global surveillance disclosures (2013–present)
3442:"Fighting terror by terrifying U.S. citizens"
3131:"Genoa II DARPAtech 2002 Presentation Script"
2787:
2689:
2687:
2584:
2282:Mayle, Adam; Knott, Alex (17 December 2002).
2277:
2275:
2273:
2271:
2051:
2049:
2047:
1417:digitization and draw important conclusions.
789:
3495:: CS1 maint: multiple names: authors list (
2558:"Wargaming the Asymmetric Environment (WAE)"
2516:
2055:
2014:
2012:
3546:George W. Bush administration controversies
3347:. Cambridge University Press. p. 258.
3223:
2998:
2881:"Evaluation of Face Recognition Algorithms"
2495:"Current Research in Social Network Theory"
2398:"Genoa II: Man and Machine Thinking as One"
2216:
2214:
2146:
2144:
2142:
1793:
1558:). Tools from the program were used in the
1454:was completed and its research moved on to
3334:
3282:Richelson, Jeffrey T. (4 September 2013).
3261:United States Government Publishing Office
3001:"Driving dangerously with the Patriot Act"
2684:
2395:
2346:"Total Information Awareness (TIA) System"
2281:
2268:
2265:, 23 February 2006, retrieved 14 June 2016
2252:
2250:
2248:
2246:
2244:
2184:
2182:
2180:
2114:
2112:
2110:
2083:
2044:
1983:
1981:
1979:
1977:
1887:
1885:
1883:
1736:
1548:Advanced Research and Development Activity
1476:Congressional restrictions and termination
796:
782:
34:system from the official (decommissioned)
3466:
3464:
3439:
3281:
2965:
2425:
2423:
2421:
2391:
2389:
2125:(illustrated ed.). Nova Publishers.
2009:
1766:
2529:"Evidence Extraction and Link Discovery"
2310:
2308:
2220:
2211:
2139:
2039:"supersnoop" system to spy on Americans.
1891:
1732:
1730:
1393:
1359:
1342:
1235:
1202:
1146:, internet histories, or bank records).
1132:
1091:
946:. INSCOM was to house TIA's hardware in
41:
25:
3470:
3404:, 26 April 2006, retrieved 16 June 2016
3361:
3340:
3275:
3087:
2849:
2241:
2227:(illustrated ed.). Little, Brown.
2188:
2177:
2118:
2107:
1974:
1880:
1858:
1550:, or ARDA (ARDA was later moved to the
903:, and privacy-protection technologies.
569:Mass surveillance in the United Kingdom
3528:
3461:
3311:
3128:
2907:
2905:
2719:
2717:
2486:
2429:
2418:
2386:
1821:
1739:"Defence research: Still in the lead?"
1737:Weinberger, Sharon (24 January 2008).
1684:In the 2008 British television series
1619:mass surveillance in the United States
1129:Evidence extraction and link discovery
564:Mass surveillance in the United States
3536:Counterterrorism in the United States
3054:
2959:
2814:
2305:
2058:"Giving In to the Surveillance State"
1953:Jonathan Turley (November 17, 2002).
1787:
1727:
1679:
1420:
516:2005 warrantless surveillance scandal
3367:
2663:"Human Identification at a distance"
2316:"Human Identification at a Distance"
2197:. Knopf Doubleday Publishing Group.
1988:WILLIAM SAFIRE (November 14, 2002).
1195:were given grants to work on TIDES.
1154:Wargaming the asymmetric environment
3341:Donohue, Laura K. (14 April 2008).
3027:
3021:
2902:
2788:Bahram Javidi, ed. (28 June 2005).
2714:
1645:, called it a "dishonest misuse of
1338:
1300:'s Robotics Institute (part of the
1067:the diagram to test various cases.
866:
13:
2492:
2430:Harris, Shane (18 February 2010).
2189:Bamford, James (14 October 2008).
2084:Poindexter, John (2 August 2002).
1859:MARKOFF, JOHN (November 9, 2002).
1232:Human identification at a distance
1193:University of California, Berkeley
14:
3582:
3507:
2372:. DIANE Publishing. p. 126.
2352:. October 3, 2002. Archived from
2094:Federation of American Scientists
1710:Privacy laws of the United States
1667:Director of National Intelligence
1552:Director of National Intelligence
1499:At some point in early 2003, the
74:Map of global NSA data collection
3226:"Senate Rejects Privacy Project"
3224:ADAM CLYMER (January 24, 2003).
2056:SHANE HARRIS (August 22, 2012).
1117:Scalable social network analysis
761:
749:
730:
718:
706:
694:
674:
664:
654:
644:
634:
624:
614:
213:President's Surveillance Program
67:
53:
3440:ROB MORSE (November 20, 2002).
3433:
3407:
3390:
3368:Eric, Schmitt (1 August 2003).
3305:
3245:
3217:
3189:
3163:
3122:
3081:
3048:
2999:Pat M. Holt (October 2, 2003).
2992:
2931:
2873:
2843:
2808:
2781:
2751:
2550:
2396:Dan Verton (1 September 2003).
2360:
2338:
2077:
1900:. Simon and Schuster. pp.
1494:Terrorism Information Awareness
1284:Georgia Institute of Technology
1198:
821:Terrorism Information Awareness
3419:American Civil Liberties Union
3142:Electronic Frontier Foundation
3101:Congressional Research Service
3088:Belasco, Amy (21 March 2003).
2852:"Human Identification Project"
1946:
1918:
1852:
1815:
1796:"Funding for TIA All But Dead"
1654:American Civil Liberties Union
1580:National Intelligence Director
1556:Disruptive Technologies Office
1251:The goals of HumanID were to:
218:Terrorist Surveillance Program
1:
3566:Privacy of telecommunications
3055:Rosen, Jeffrey (2002-12-15).
2860:University of Texas at Dallas
2815:Nixon, M.S. (7 August 2003).
2438:(reprint ed.). Penguin.
1720:
1603:
1576:Senate Intelligence Committee
1572:Air Force Research Laboratory
1525:
1324:University of Texas at Dallas
1046:
397:Senate Intelligence Committee
3561:Privacy in the United States
3179:Information Awareness Office
3028:Lee, Newton (7 April 2015).
2921:Information Awareness Office
2566:Information Awareness Office
2119:Stevens, Gina Marie (2003).
1794:Ryan Singel (14 June 2003).
1612:
1578:hearing that February, both
1447:Information Awareness Office
1406:Information Awareness Office
817:Information Awareness Office
36:Information Awareness Office
7:
3471:Clapper, James R,. (2018).
2292:Center for Public Integrity
1955:"George Bush's Big Brother"
1693:
1414:total information awareness
1073:
967:Lockheed Martin Corporation
809:Total Information Awareness
374:FISA Amendments Act of 2008
369:Protect America Act of 2007
208:Total Information Awareness
32:Total Information Awareness
10:
3587:
3312:Solove, Daniel J. (2011).
2733:Carnegie Mellon University
1538:
1535:mechanics were abandoned.
1408:and chief supporter of TIA
1389:
1375:
1302:School of Computer Science
1298:Carnegie Mellon University
1087:
1077:
1055:
1019:
171:Tailored Access Operations
21:The Last Enemy (TV series)
18:
3320:. Yale University Press.
3292:National Security Archive
3005:Christian Science Monitor
2889:Colorado State University
2825:University of Southampton
1429:in 2001, by Rear Admiral
1329:Colorado State University
1320:University of Southampton
1216:automated translation of
544:Surveillance of reporters
402:National Security Council
16:US mass detection program
3447:San Francisco Chronicle
2221:Jacobsen, Annie (2015).
1838:10.1177/0306396810377002
1501:National Security Agency
1480:On 24 January 2003, the
1437:and a key player in the
1051:
861:National Security Agency
842:". According to Senator
826:Based on the concept of
60:National Security Agency
2288:www.publicintegrity.org
1751:Nature Publishing Group
1659:San Francisco Chronicle
1566:. In October 2005, the
1562:and other parts of the
1123:social network analysis
969:, Schafer Corporation,
3556:Management cybernetics
3396:Mark Williams Pontin.
2767:University of Maryland
1892:Shorrock, Tim (2008).
1665:Still, in 2013 former
1409:
1404:, the director of the
1348:
1309:University of Maryland
1241:
1208:
1138:
1097:
559:Insider Threat Program
47:
39:
3571:Surveillance scandals
3402:MIT Technology Review
2938:Anthony M. Townsend.
1960:The Los Angeles Times
1397:
1360:Scope of surveillance
1346:
1239:
1226:United States Marines
1206:
1173:information retrieval
1136:
1095:
1064:intelligence analysis
364:Homeland Security Act
258:Databases, tools etc.
45:
29:
3284:"The Snowden Affair"
3129:Armour, Tom (2002).
2975:United States Senate
2969:(January 15, 2003).
2885:www.cs.colostate.edu
2673:on February 15, 2009
2505:on February 26, 2015
2025:The Washington Times
1482:United States Senate
1427:September 11 attacks
1288:College of Computing
554:UN diplomatic spying
3205:. December 23, 2002
2913:"Bio- Surveillance"
2821:www.ecs.soton.ac.uk
2697:Guide to Biometrics
2356:on October 3, 2002.
1990:"You Are a Suspect"
1759:2008Natur.451..390W
1715:Situation awareness
1643:University of Texas
1532:appropriations bill
1356:health conditions.
1333:Columbia University
1189:Columbia University
1179:evaluations run by
1177:machine translation
963:Booz Allen Hamilton
901:pattern recognition
893:counterintelligence
828:predictive policing
425:Hepting v. AT&T
344:Privacy Act of 1974
122:Upstream collection
3253:"Joint Resolution"
3231:The New York Times
3202:The New York Times
3061:The New York Times
2063:The New York Times
1995:The New York Times
1866:The New York Times
1680:In popular culture
1628:The New York Times
1560:war in Afghanistan
1554:'s control as the
1439:Iran–Contra affair
1421:Early developments
1410:
1349:
1242:
1209:
1185:Cornell University
1139:
1098:
435:Clapper v. Amnesty
310:GCHQ collaboration
304:BOUNDLESSINFORMANT
48:
40:
3551:Mass surveillance
3288:nsarchive.gwu.edu
3175:www.darpa.mil/iao
2917:www.darpa.mil/iao
2562:www.darpa.mil/iao
2320:www.cc.gatech.edu
1598:Michael V. Hayden
1144:NSA call database
840:counter-terrorism
836:Manhattan Project
806:
805:
3578:
3501:
3500:
3494:
3486:
3468:
3459:
3458:
3456:
3454:
3437:
3431:
3430:
3428:
3426:
3421:. April 20, 2003
3411:
3405:
3394:
3388:
3387:
3385:
3383:
3378:. Washington D.C
3365:
3359:
3358:
3338:
3332:
3331:
3319:
3309:
3303:
3302:
3300:
3298:
3279:
3273:
3272:
3270:
3268:
3249:
3243:
3242:
3240:
3238:
3221:
3215:
3214:
3212:
3210:
3193:
3187:
3186:
3181:. Archived from
3167:
3161:
3160:
3158:
3156:
3150:
3144:. Archived from
3135:
3126:
3120:
3119:
3117:
3115:
3110:on June 27, 2004
3109:
3103:. Archived from
3097:www.au.af.mil/au
3094:
3085:
3079:
3078:
3076:
3075:
3052:
3046:
3045:
3025:
3019:
3018:
3013:
3011:
2996:
2990:
2989:
2983:
2981:
2963:
2957:
2956:
2954:
2952:
2935:
2929:
2928:
2923:. Archived from
2909:
2900:
2899:
2897:
2895:
2877:
2871:
2870:
2868:
2866:
2856:www.utdallas.edu
2850:O'Toole, Alice.
2847:
2841:
2840:
2838:
2836:
2827:. Archived from
2812:
2806:
2805:
2785:
2779:
2778:
2776:
2774:
2755:
2749:
2748:
2746:
2744:
2739:on 9 August 2016
2735:. Archived from
2721:
2712:
2711:
2691:
2682:
2681:
2679:
2678:
2669:. Archived from
2659:
2648:
2647:
2645:
2644:
2635:. Archived from
2625:
2614:
2613:
2611:
2610:
2601:. Archived from
2591:
2582:
2581:
2579:
2577:
2568:. Archived from
2554:
2548:
2547:
2545:
2544:
2535:. Archived from
2525:
2514:
2513:
2511:
2510:
2501:. Archived from
2490:
2484:
2483:
2481:
2480:
2471:. Archived from
2461:
2450:
2449:
2437:
2427:
2416:
2415:
2413:
2411:
2406:. IDG Enterprise
2393:
2384:
2383:
2364:
2358:
2357:
2342:
2336:
2335:
2333:
2331:
2312:
2303:
2302:
2300:
2298:
2279:
2266:
2262:National Journal
2254:
2239:
2238:
2218:
2209:
2208:
2196:
2186:
2175:
2174:
2172:
2170:
2156:
2148:
2137:
2136:
2116:
2105:
2104:
2102:
2100:
2081:
2075:
2074:
2072:
2070:
2053:
2042:
2041:
2035:
2033:
2016:
2007:
2006:
2004:
2002:
1985:
1972:
1971:
1969:
1967:
1950:
1944:
1943:
1941:
1939:
1934:. AP. 2003-09-25
1922:
1916:
1915:
1899:
1889:
1878:
1877:
1875:
1873:
1856:
1850:
1849:
1825:Race & Class
1819:
1813:
1812:
1810:
1808:
1791:
1785:
1784:
1770:
1734:
1522:led the effort.
1339:Bio-surveillance
1292:gait recognition
1276:face recognition
1218:natural language
1080:Project Genoa II
971:SRS Technologies
867:Program synopsis
798:
791:
784:
766:
765:
754:
753:
735:
734:
723:
722:
711:
710:
699:
698:
678:
668:
658:
648:
638:
628:
618:
450:Wikimedia v. NSA
440:Klayman v. Obama
339:Safe Streets Act
71:
57:
50:
49:
3586:
3585:
3581:
3580:
3579:
3577:
3576:
3575:
3526:
3525:
3510:
3505:
3504:
3488:
3487:
3483:
3469:
3462:
3452:
3450:
3438:
3434:
3424:
3422:
3413:
3412:
3408:
3395:
3391:
3381:
3379:
3366:
3362:
3355:
3339:
3335:
3328:
3310:
3306:
3296:
3294:
3280:
3276:
3266:
3264:
3263:. February 2003
3251:
3250:
3246:
3236:
3234:
3222:
3218:
3208:
3206:
3195:
3194:
3190:
3169:
3168:
3164:
3154:
3152:
3148:
3133:
3127:
3123:
3113:
3111:
3107:
3092:
3086:
3082:
3073:
3071:
3053:
3049:
3042:
3026:
3022:
3009:
3007:
2997:
2993:
2979:
2977:
2964:
2960:
2950:
2948:
2936:
2932:
2911:
2910:
2903:
2893:
2891:
2879:
2878:
2874:
2864:
2862:
2848:
2844:
2834:
2832:
2813:
2809:
2802:
2786:
2782:
2772:
2770:
2769:. 17 April 2001
2757:
2756:
2752:
2742:
2740:
2723:
2722:
2715:
2708:
2692:
2685:
2676:
2674:
2661:
2660:
2651:
2642:
2640:
2627:
2626:
2617:
2608:
2606:
2593:
2592:
2585:
2575:
2573:
2556:
2555:
2551:
2542:
2540:
2527:
2526:
2517:
2508:
2506:
2493:Ethier, Jason.
2491:
2487:
2478:
2476:
2463:
2462:
2453:
2446:
2428:
2419:
2409:
2407:
2394:
2387:
2380:
2366:
2365:
2361:
2344:
2343:
2339:
2329:
2327:
2314:
2313:
2306:
2296:
2294:
2280:
2269:
2255:
2242:
2235:
2219:
2212:
2205:
2187:
2178:
2168:
2166:
2154:
2150:
2149:
2140:
2133:
2117:
2108:
2098:
2096:
2082:
2078:
2068:
2066:
2054:
2045:
2031:
2029:
2018:
2017:
2010:
2000:
1998:
1986:
1975:
1965:
1963:
1951:
1947:
1937:
1935:
1924:
1923:
1919:
1912:
1890:
1881:
1871:
1869:
1857:
1853:
1820:
1816:
1806:
1804:
1792:
1788:
1768:10.1038/451390a
1735:
1728:
1723:
1696:
1682:
1615:
1606:
1583:John Negroponte
1541:
1528:
1478:
1431:John Poindexter
1423:
1402:John Poindexter
1392:
1378:
1362:
1341:
1234:
1201:
1165:
1156:
1131:
1119:
1090:
1082:
1076:
1060:
1054:
1049:
1022:
986:Carnegie Mellon
897:law enforcement
869:
832:John Poindexter
802:
773:
772:
760:
748:
729:
717:
705:
693:
605:
597:
596:
582:
574:
573:
534:
526:
525:
511:
503:
502:
468:
460:
459:
445:ACLU v. Clapper
415:
407:
406:
387:
379:
378:
334:
326:
325:
85:
77:
58:
30:Diagram of the
24:
17:
12:
11:
5:
3584:
3574:
3573:
3568:
3563:
3558:
3553:
3548:
3543:
3538:
3524:
3523:
3518:
3509:
3508:External links
3506:
3503:
3502:
3481:
3460:
3432:
3406:
3389:
3375:New York Times
3360:
3353:
3333:
3326:
3304:
3274:
3244:
3216:
3188:
3185:on 2009-02-16.
3162:
3121:
3080:
3047:
3040:
3020:
2991:
2958:
2930:
2927:on 2006-09-19.
2901:
2872:
2842:
2807:
2800:
2780:
2750:
2713:
2706:
2683:
2649:
2629:"Communicator"
2615:
2583:
2572:on 28 May 2012
2549:
2515:
2485:
2451:
2444:
2417:
2385:
2378:
2359:
2337:
2304:
2267:
2240:
2233:
2210:
2203:
2176:
2138:
2131:
2106:
2076:
2043:
2028:. May 28, 2004
2008:
1973:
1945:
1917:
1910:
1879:
1851:
1814:
1786:
1725:
1724:
1722:
1719:
1718:
1717:
1712:
1707:
1702:
1695:
1692:
1687:The Last Enemy
1681:
1678:
1674:Edward Snowden
1633:William Safire
1614:
1611:
1605:
1602:
1590:Robert Mueller
1540:
1537:
1527:
1524:
1477:
1474:
1422:
1419:
1391:
1388:
1377:
1374:
1361:
1358:
1340:
1337:
1280:
1279:
1272:
1269:
1266:
1263:
1258:Fuse face and
1256:
1233:
1230:
1200:
1197:
1164:
1161:
1155:
1152:
1130:
1127:
1118:
1115:
1107:World Wide Web
1089:
1086:
1078:Main article:
1075:
1072:
1056:Main article:
1053:
1050:
1048:
1045:
1044:
1043:
1039:
1036:
1033:
1021:
1018:
982:Colorado State
868:
865:
856:New York Times
804:
803:
801:
800:
793:
786:
778:
775:
774:
771:
770:
758:
745:
744:
740:
739:
727:
715:
703:
690:
689:
683:
682:
672:
662:
652:
642:
632:
622:
611:
610:
606:
603:
602:
599:
598:
595:
594:
589:
583:
580:
579:
576:
575:
572:
571:
566:
561:
556:
551:
546:
541:
535:
532:
531:
528:
527:
524:
523:
518:
512:
509:
508:
505:
504:
501:
500:
498:Edward Snowden
495:
490:
485:
480:
475:
473:William Binney
469:
467:Whistleblowers
466:
465:
462:
461:
458:
457:
452:
447:
442:
437:
432:
427:
422:
416:
413:
412:
409:
408:
405:
404:
399:
394:
388:
385:
384:
381:
380:
377:
376:
371:
366:
361:
356:
351:
346:
341:
335:
332:
331:
328:
327:
324:
323:
318:
312:
311:
307:
306:
301:
296:
291:
286:
281:
276:
271:
266:
260:
259:
255:
254:
249:
244:
239:
234:
228:
227:
223:
222:
221:
220:
210:
205:
200:
195:
190:
185:
179:
178:
174:
173:
167:
166:
162:
161:
155:
154:
150:
149:
144:
139:
134:
129:
124:
118:
117:
113:
112:
107:
102:
97:
91:
90:
86:
83:
82:
79:
78:
72:
64:
63:
15:
9:
6:
4:
3:
2:
3583:
3572:
3569:
3567:
3564:
3562:
3559:
3557:
3554:
3552:
3549:
3547:
3544:
3542:
3539:
3537:
3534:
3533:
3531:
3522:
3519:
3517:
3516:
3512:
3511:
3498:
3492:
3484:
3482:9780525558651
3478:
3474:
3467:
3465:
3449:
3448:
3443:
3436:
3420:
3416:
3410:
3403:
3399:
3393:
3377:
3376:
3371:
3364:
3356:
3354:9781139469579
3350:
3346:
3345:
3337:
3329:
3327:9780300177251
3323:
3318:
3317:
3308:
3293:
3289:
3285:
3278:
3262:
3258:
3254:
3248:
3233:
3232:
3227:
3220:
3204:
3203:
3198:
3192:
3184:
3180:
3176:
3172:
3166:
3151:on 2016-10-08
3147:
3143:
3139:
3132:
3125:
3106:
3102:
3098:
3091:
3084:
3070:
3066:
3062:
3058:
3051:
3043:
3041:9783319172446
3037:
3033:
3032:
3024:
3017:
3006:
3002:
2995:
2988:
2976:
2972:
2968:
2962:
2947:
2946:
2941:
2934:
2926:
2922:
2918:
2914:
2908:
2906:
2890:
2886:
2882:
2876:
2861:
2857:
2853:
2846:
2831:on 2016-08-05
2830:
2826:
2822:
2818:
2811:
2803:
2801:9780387206165
2797:
2793:
2792:
2784:
2768:
2764:
2760:
2754:
2738:
2734:
2730:
2726:
2720:
2718:
2709:
2707:9781475740363
2703:
2699:
2698:
2690:
2688:
2672:
2668:
2664:
2658:
2656:
2654:
2639:on 2009-02-15
2638:
2634:
2630:
2624:
2622:
2620:
2605:on 2009-02-15
2604:
2600:
2596:
2590:
2588:
2571:
2567:
2563:
2559:
2553:
2539:on 2009-02-15
2538:
2534:
2530:
2524:
2522:
2520:
2504:
2500:
2496:
2489:
2475:on 2009-02-16
2474:
2470:
2466:
2460:
2458:
2456:
2447:
2445:9781101195741
2441:
2436:
2435:
2426:
2424:
2422:
2405:
2404:
2403:Computerworld
2399:
2392:
2390:
2381:
2379:9781422320259
2375:
2371:
2370:
2363:
2355:
2351:
2347:
2341:
2325:
2321:
2317:
2311:
2309:
2293:
2289:
2285:
2278:
2276:
2274:
2272:
2264:
2263:
2258:
2253:
2251:
2249:
2247:
2245:
2236:
2234:9780316371650
2230:
2226:
2225:
2217:
2215:
2206:
2204:9780385528399
2200:
2195:
2194:
2185:
2183:
2181:
2165:. 20 May 2003
2164:
2160:
2153:
2147:
2145:
2143:
2134:
2132:9781590338698
2128:
2124:
2123:
2115:
2113:
2111:
2095:
2091:
2087:
2080:
2065:
2064:
2059:
2052:
2050:
2048:
2040:
2027:
2026:
2021:
2015:
2013:
2001:September 20,
1997:
1996:
1991:
1984:
1982:
1980:
1978:
1962:
1961:
1956:
1949:
1933:
1932:
1927:
1921:
1913:
1911:9780743282246
1907:
1903:
1898:
1897:
1888:
1886:
1884:
1868:
1867:
1862:
1855:
1847:
1843:
1839:
1835:
1831:
1827:
1826:
1818:
1803:
1802:
1797:
1790:
1783:
1778:
1774:
1769:
1764:
1760:
1756:
1752:
1748:
1744:
1740:
1733:
1731:
1726:
1716:
1713:
1711:
1708:
1706:
1703:
1701:
1698:
1697:
1691:
1689:
1688:
1677:
1675:
1671:
1670:James Clapper
1668:
1663:
1661:
1660:
1655:
1650:
1648:
1644:
1640:
1636:
1634:
1630:
1629:
1624:
1620:
1610:
1601:
1599:
1595:
1591:
1588:
1584:
1581:
1577:
1573:
1569:
1565:
1564:War on Terror
1561:
1557:
1553:
1549:
1545:
1536:
1533:
1523:
1521:
1517:
1511:
1509:
1504:
1502:
1497:
1495:
1489:
1487:
1483:
1473:
1471:
1466:
1464:
1459:
1457:
1453:
1452:Project Genoa
1448:
1444:
1440:
1436:
1435:Ronald Reagan
1432:
1428:
1418:
1415:
1407:
1403:
1400:
1396:
1387:
1384:
1373:
1371:
1366:
1357:
1354:
1345:
1336:
1334:
1330:
1325:
1321:
1316:
1314:
1310:
1305:
1303:
1299:
1295:
1293:
1289:
1285:
1277:
1273:
1270:
1267:
1264:
1261:
1257:
1254:
1253:
1252:
1249:
1247:
1238:
1229:
1227:
1222:
1219:
1213:
1212:environment.
1205:
1196:
1194:
1190:
1186:
1182:
1178:
1174:
1169:
1160:
1151:
1147:
1145:
1135:
1126:
1124:
1114:
1110:
1108:
1103:
1094:
1085:
1081:
1071:
1068:
1065:
1059:
1058:Project Genoa
1040:
1037:
1034:
1031:
1030:
1029:
1026:
1017:
1015:
1011:
1007:
1003:
999:
995:
991:
987:
983:
979:
974:
972:
968:
964:
960:
955:
953:
949:
945:
941:
937:
933:
929:
925:
921:
917:
913:
909:
904:
902:
898:
894:
890:
886:
882:
878:
874:
864:
862:
858:
857:
850:
847:
845:
841:
837:
834:called it a "
833:
829:
824:
822:
818:
814:
810:
799:
794:
792:
787:
785:
780:
779:
777:
776:
769:
764:
759:
757:
752:
747:
746:
742:
741:
738:
733:
728:
726:
721:
716:
714:
709:
704:
702:
697:
692:
691:
688:
685:
684:
681:
677:
673:
671:
667:
663:
661:
657:
653:
651:
647:
643:
641:
637:
633:
631:
627:
623:
621:
617:
613:
612:
609:United States
608:
607:
604:Collaboration
601:
600:
593:
590:
588:
585:
584:
578:
577:
570:
567:
565:
562:
560:
557:
555:
552:
550:
549:Mail tracking
547:
545:
542:
540:
537:
536:
530:
529:
522:
519:
517:
514:
513:
507:
506:
499:
496:
494:
491:
489:
486:
484:
481:
479:
476:
474:
471:
470:
464:
463:
456:
453:
451:
448:
446:
443:
441:
438:
436:
433:
431:
428:
426:
423:
421:
418:
417:
411:
410:
403:
400:
398:
395:
393:
390:
389:
383:
382:
375:
372:
370:
367:
365:
362:
360:
357:
355:
352:
350:
347:
345:
342:
340:
337:
336:
330:
329:
322:
319:
317:
314:
313:
309:
308:
305:
302:
300:
297:
295:
292:
290:
287:
285:
282:
280:
277:
275:
272:
270:
267:
265:
262:
261:
257:
256:
253:
250:
248:
245:
243:
240:
238:
235:
233:
230:
229:
225:
224:
219:
216:
215:
214:
211:
209:
206:
204:
201:
199:
196:
194:
191:
189:
186:
184:
181:
180:
176:
175:
172:
169:
168:
164:
163:
160:
157:
156:
152:
151:
148:
145:
143:
140:
138:
135:
133:
130:
128:
125:
123:
120:
119:
115:
114:
111:
108:
106:
103:
101:
98:
96:
93:
92:
88:
87:
81:
80:
75:
70:
66:
65:
61:
56:
52:
51:
44:
37:
33:
28:
22:
3514:
3472:
3451:. Retrieved
3445:
3435:
3423:. Retrieved
3409:
3401:
3392:
3380:. Retrieved
3373:
3363:
3343:
3336:
3315:
3307:
3295:. Retrieved
3287:
3277:
3265:. Retrieved
3256:
3247:
3235:. Retrieved
3229:
3219:
3207:. Retrieved
3200:
3191:
3183:the original
3174:
3165:
3153:. Retrieved
3146:the original
3137:
3124:
3112:. Retrieved
3105:the original
3096:
3083:
3072:. Retrieved
3060:
3050:
3030:
3023:
3015:
3008:. Retrieved
3004:
2994:
2985:
2978:. Retrieved
2961:
2949:. Retrieved
2943:
2933:
2925:the original
2916:
2892:. Retrieved
2884:
2875:
2863:. Retrieved
2855:
2845:
2833:. Retrieved
2829:the original
2820:
2810:
2790:
2783:
2771:. Retrieved
2762:
2753:
2741:. Retrieved
2737:the original
2728:
2696:
2675:. Retrieved
2671:the original
2666:
2641:. Retrieved
2637:the original
2632:
2607:. Retrieved
2603:the original
2598:
2574:. Retrieved
2570:the original
2561:
2552:
2541:. Retrieved
2537:the original
2532:
2507:. Retrieved
2503:the original
2498:
2488:
2477:. Retrieved
2473:the original
2468:
2433:
2408:. Retrieved
2401:
2368:
2362:
2354:the original
2340:
2328:. Retrieved
2319:
2295:. Retrieved
2287:
2260:
2257:TIA Lives On
2223:
2192:
2167:. Retrieved
2159:www.epic.org
2158:
2121:
2097:. Retrieved
2089:
2079:
2067:. Retrieved
2061:
2037:
2030:. Retrieved
2023:
1999:. Retrieved
1993:
1964:. Retrieved
1958:
1948:
1936:. Retrieved
1929:
1920:
1895:
1870:. Retrieved
1864:
1854:
1829:
1823:
1817:
1805:. Retrieved
1799:
1789:
1780:
1746:
1742:
1686:
1683:
1664:
1657:
1651:
1637:
1626:
1616:
1607:
1594:NSA director
1587:FBI Director
1542:
1529:
1520:Byron Dorgan
1512:
1505:
1498:
1493:
1490:
1485:
1479:
1467:
1460:
1424:
1413:
1411:
1383:privacy laws
1379:
1367:
1363:
1353:bioterrorism
1350:
1317:
1306:
1296:
1281:
1250:
1243:
1223:
1214:
1210:
1199:Communicator
1170:
1166:
1157:
1148:
1140:
1120:
1111:
1099:
1083:
1069:
1061:
1027:
1023:
1002:Georgia Tech
975:
956:
948:Fort Belvoir
905:
889:intelligence
870:
854:
851:
848:
825:
820:
812:
808:
807:
478:Thomas Drake
455:US v. Moalin
430:Jewel v. NSA
386:Institutions
284:TRAFFICTHIEF
207:
62:surveillance
31:
3453:21 December
3425:19 December
3257:www.gpo.gov
3010:19 December
2980:19 December
2951:19 December
2069:19 December
2032:19 December
1966:19 December
1938:19 December
1872:19 December
1832:(2): 3–24.
1753:: 390–393.
1443:fiscal year
1290:focused on
1014:Southampton
885:data mining
510:Publication
488:Thomas Tamm
420:ACLU v. NSA
359:Patriot Act
333:Legislation
193:Trailblazer
3530:Categories
3237:7 December
3209:7 December
3138:w2.eff.org
3074:2021-04-03
2677:2009-03-15
2643:2009-03-15
2609:2009-03-15
2543:2009-03-15
2509:2009-03-15
2479:2009-03-15
1807:7 December
1721:References
1604:Basketball
1526:After 2003
1191:, and the
1047:Components
483:Mark Klein
226:Since 2007
198:Turbulence
177:Since 2001
165:Since 1998
153:Since 1990
142:ThinThread
116:Since 1978
3491:cite book
3069:0362-4331
2967:Ron Wyden
2465:"Genisys"
1931:USA Today
1846:144001217
1705:Pre-crime
1639:Hans Mark
1613:Criticism
1516:Ron Wyden
1470:Ray Ozzie
1412:The term
1246:biometric
844:Ron Wyden
687:Five Eyes
539:Cablegate
493:Russ Tice
294:XKeyscore
274:Main Core
242:Stateroom
188:STORMBREW
159:RAMPART-A
137:Main Core
1777:18216826
1749:(7177).
1694:See also
1621:. In an
1544:Genoa II
1508:proposal
1456:Genoa II
1313:infrared
1102:database
1074:Genoa II
1006:Maryland
990:Columbia
978:Berkeley
952:Virginia
928:STRATCOM
881:Genoa II
630:CYBERCOM
592:Metadata
581:Concepts
414:Lawsuits
316:MUSCULAR
289:DISHFIRE
237:Dropmire
203:Genoa II
132:FAIRVIEW
105:SHAMROCK
89:Pre-1978
84:Programs
3382:10 June
3171:"Genoa"
3155:20 June
2894:16 June
2865:16 June
2835:16 June
2773:16 June
2743:16 June
2595:"TIDES"
2576:16 June
2330:16 June
2090:fas.org
1755:Bibcode
1700:LifeLog
1539:Topsail
1390:History
1376:Privacy
1278:system.
1088:Genisys
1042:action.
1020:Mission
994:Cornell
863:(NSA).
533:Related
321:Tempora
299:ICREACH
279:MAINWAY
264:PINWALE
247:Bullrun
183:OAKSTAR
127:BLARNEY
100:MINARET
95:ECHELON
38:website
3479:
3351:
3324:
3297:9 June
3267:7 June
3114:7 June
3067:
3038:
2798:
2704:
2442:
2410:3 June
2376:
2326:. 2003
2297:6 June
2231:
2201:
2169:7 June
2129:
2099:3 June
1908:
1844:
1775:
1743:Nature
1012:, and
998:Dallas
938:, and
908:INSCOM
895:, and
587:SIGINT
269:MARINA
252:MYSTIC
110:PROMIS
3541:DARPA
3149:(PDF)
3134:(PDF)
3108:(PDF)
3093:(PDF)
2945:Salon
2350:DARPA
2163:DARPA
2155:(PDF)
1842:S2CID
1801:Wired
1647:DARPA
1623:op-ed
1052:Genoa
944:nodes
936:JFCOM
932:SOCOM
877:Genoa
873:DARPA
743:Other
232:PRISM
147:Genoa
3497:link
3477:ISBN
3455:2013
3427:2013
3384:2016
3349:ISBN
3322:ISBN
3299:2016
3269:2016
3239:2013
3211:2013
3157:2016
3116:2016
3065:ISSN
3036:ISBN
3012:2013
2982:2013
2953:2013
2896:2016
2867:2016
2837:2016
2796:ISBN
2775:2016
2745:2016
2702:ISBN
2578:2016
2440:ISBN
2412:2016
2374:ISBN
2332:2016
2299:2016
2229:ISBN
2199:ISBN
2171:2016
2127:ISBN
2101:2016
2071:2013
2034:2013
2003:2013
1968:2013
1940:2013
1906:ISBN
1874:2013
1809:2013
1773:PMID
1652:The
1625:for
1585:and
1568:SAIC
1518:and
1399:Adm.
1318:The
1307:The
1260:gait
1181:NIST
940:JWAC
924:CIFA
838:for
756:DGSE
737:GCSB
713:GCHQ
701:CSEC
392:FISC
354:ECPA
349:FISA
1902:221
1834:doi
1763:doi
1747:451
1649:".
1370:DNA
1286:'s
1010:MIT
920:CIA
916:DIA
912:NSA
813:TIA
768:BND
725:ASD
680:IAO
670:DHS
660:CIA
650:FBI
640:DOJ
620:CSS
3532::
3493:}}
3489:{{
3463:^
3444:.
3417:.
3400:,
3372:.
3290:.
3286:.
3259:.
3255:.
3228:.
3199:.
3177:.
3173:.
3140:.
3136:.
3099:.
3095:.
3063:.
3059:.
3014:.
3003:.
2984:.
2973:.
2942:.
2919:.
2915:.
2904:^
2887:.
2883:.
2858:.
2854:.
2823:.
2819:.
2765:.
2761:.
2731:.
2727:.
2716:^
2686:^
2665:.
2652:^
2631:.
2618:^
2597:.
2586:^
2564:.
2560:.
2531:.
2518:^
2497:.
2467:.
2454:^
2420:^
2400:.
2388:^
2348:.
2322:.
2318:.
2307:^
2290:.
2286:.
2270:^
2259:,
2243:^
2213:^
2179:^
2161:.
2157:.
2141:^
2109:^
2092:.
2088:.
2060:.
2046:^
2036:.
2022:.
2011:^
1992:.
1976:^
1957:.
1928:.
1904:.
1882:^
1863:.
1840:.
1830:52
1828:.
1798:.
1779:.
1771:.
1761:.
1745:.
1741:.
1729:^
1631:,
1596:,
1458:.
1372:.
1187:,
1183:.
1016:.
1008:,
1004:,
1000:,
996:,
992:,
988:,
984:,
980:,
965:,
961:,
954:.
950:,
934:,
930:,
926:,
922:,
918:,
914:,
910:,
891:,
879:,
823:.
3499:)
3485:.
3457:.
3429:.
3386:.
3357:.
3330:.
3301:.
3271:.
3241:.
3213:.
3159:.
3118:.
3077:.
3044:.
2955:.
2898:.
2869:.
2839:.
2804:.
2777:.
2747:.
2710:.
2680:.
2646:.
2612:.
2580:.
2546:.
2512:.
2482:.
2448:.
2414:.
2382:.
2334:.
2301:.
2237:.
2207:.
2173:.
2135:.
2103:.
2073:.
2005:.
1970:.
1942:.
1914:.
1876:.
1848:.
1836::
1811:.
1765::
1757::
811:(
797:e
790:t
783:v
23:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.