106:(FIB) in a switch—the switch forgets which port connects to the target before the host forgets the MAC address of the target. This can be prevented by configuring the switch with a FIB timeout longer than the ARP cache timeouts of nodes on its network. When a node needs to send a frame to a host after its corresponding ARP cache entry expires it must first send an ARP broadcast frame, which the switch must forward through all ports, to discover the (current) MAC address of the host.
67:
53:
90:
When a bridge or switch has no room left in its forwarding information base and so cannot add an entry for a new node, it must forward any frame addressed to that node through all ports except the one on which the frame was received. This is a common problem on networks with many hosts. Less common
82:
requires that the switch receive a frame from a device before unicast frames can be forwarded to it. Before any such transmission is received, unicast flooding is used to ensure transmissions reach their intended destinations. This is normally a short-lived condition as receipt typically produces a
31:
frame and the switch does not know that the addressee is on any particular switch port. Since the switch has no information regarding which port, if any, the addressee might be reached through, it forwards the frame through all ports aside from the one through which the frame was received.
109:
Misconfigured features of the networks may lead to unicast flooding as well. If there are two layer-2 paths from Host A to B and Host A uses path 1 to talk to Host B, but Host B uses path 2 to respond to Host A, then intermediate switches on path 1 will never learn the destination
87:. An entry is purged when the link goes down on the original port or when it expires due to inactivity (five minutes is the default on many switches). A time limit is necessary because a switch does not necessarily see any indication when a network node is moved or disconnected.
129:
A feature blocking unicast floods is available on Cisco switches but is not enabled by default. After ensuring that timeouts and security features have been configured to maintain table entries on client access ports longer than typical host
172:
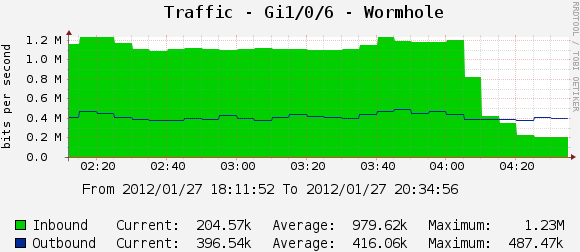
80% of the frames were flooded out never to be received by the destination address, while 20% was valid traffic. In high-volume networks, the flooded traffic may cause ports to saturate, leading to packet loss and high latency.
346:
166:
83:
response that completes the learning process. The process occurs when a device is initially connected to a network segment, or after its address and port identifier is purged from the
162:
When a network is experiencing unicast flooding, network performance may be degraded. Here is a graph of a bridge before and after adjusting the size of the bridge address cache:
387:
217:
154:
implements port isolation such that members of the VLAN are only allowed to communicate via a designated uplink are not allowed to talk to other members of the VLAN.
121:, the address cache on that switch will be flushed causing all subsequent frames to be flooded out of all ports until the addresses are relearned by the switch.
63:, the frame is treated like a broadcast frame and sent to all network segments to which it is attached except the one from which it received the frame:
323:
193:
258:
176:
Another side effect of exhausted address tables is the compromise of data. The security considerations are discussed in the
117:
A final cause of unicast floods are topology changes. When a link state changes on a network port that participates in
49:
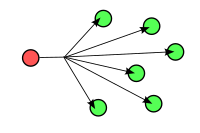
in a network to another. This diagram illustrates the unicast transmission of a frame from one network node to another:
414:
302:
103:
99:
84:
114:
of Host B and intermediate switches on path 2 will never learn the destination MAC address of Host A.
238:
79:
367:
280:
8:
118:
59:
When a switch receives a unicast frame with a destination address not in the switch’s
46:
60:
20:
134:
timeouts, this command is used to quiet down the unicast floods on those ports:
181:
408:
177:
151:
92:
165:
111:
180:—one of several causes of unicast floods. If an end user is running a
131:
143:
41:
28:
66:
259:"Elimination of Asymmetric Forwarding and Unicast Flooding"
52:
150:
are forbidden to communicate with other protected ports.
278:
281:"Troubleshooting Unicast Flooding Due to Topology"
91:is the artificial flooding of address tables in a
184:, the flooded frames can be captured and viewed.
406:
194:Broadcast, unknown-unicast and multicast traffic
300:
365:
102:cache timeout longer than the timeout of the
45:refers to a one-to-one transmission from one
142:Other techniques involve isolating hosts at
324:"Port Unicast and Multicast Flood Blocking"
236:
215:
138:Switch(config-if)# switchport block unicast
211:
209:
98:Another common cause is a host with an
407:
157:
279:Balaji Sivasubramanian (2004-09-10).
206:
303:"Blocking Unknown Unicast Flooding"
13:
164:
65:
51:
14:
426:
16:Treatment of unicast as broadcast
27:occurs when a switch receives a
380:
359:
339:
316:
294:
272:
251:
230:
1:
301:Jeremy Stretch (2010-06-04).
199:
35:
366:Petr Lapukhov (2008-07-14).
347:"Configuring Protected Port"
7:
388:"Configuring Private VLANs"
187:
124:
104:forwarding information base
85:forwarding information base
10:
431:
237:Steven King (2009-06-17).
218:"Fix for unicast flooding"
216:Rudy Rucker (2012-01-27).
368:"Private VLANs Revisited"
73:
78:The learning process of
169:
146:. Ports configured as
70:
56:
415:Internet architecture
168:
69:
55:
80:transparent bridging
261:. Cisco Systems Inc
158:Effects on Networks
119:rapid spanning tree
21:computer networking
239:"Unicast Flooding"
170:
71:
57:
422:
399:
398:
396:
395:
384:
378:
377:
375:
374:
363:
357:
356:
354:
353:
343:
337:
336:
334:
333:
328:
320:
314:
313:
311:
310:
305:. PacketLife.net
298:
292:
291:
289:
288:
276:
270:
269:
267:
266:
255:
249:
248:
246:
245:
234:
228:
227:
225:
224:
213:
61:forwarding table
430:
429:
425:
424:
423:
421:
420:
419:
405:
404:
403:
402:
393:
391:
386:
385:
381:
372:
370:
364:
360:
351:
349:
345:
344:
340:
331:
329:
326:
322:
321:
317:
308:
306:
299:
295:
286:
284:
277:
273:
264:
262:
257:
256:
252:
243:
241:
235:
231:
222:
220:
214:
207:
202:
190:
160:
148:protected ports
140:
127:
76:
38:
17:
12:
11:
5:
428:
418:
417:
401:
400:
379:
358:
338:
315:
293:
271:
250:
229:
204:
203:
201:
198:
197:
196:
189:
186:
182:packet sniffer
159:
156:
136:
126:
123:
75:
72:
37:
34:
15:
9:
6:
4:
3:
2:
427:
416:
413:
412:
410:
389:
383:
369:
362:
348:
342:
325:
319:
304:
297:
283:. Cisco Press
282:
275:
260:
254:
240:
233:
219:
212:
210:
205:
195:
192:
191:
185:
183:
179:
174:
167:
163:
155:
153:
152:Private VLANs
149:
145:
139:
135:
133:
122:
120:
115:
113:
107:
105:
101:
96:
94:
88:
86:
81:
68:
64:
62:
54:
50:
48:
44:
43:
33:
30:
26:
25:unicast flood
22:
392:. Retrieved
382:
371:. Retrieved
361:
350:. Retrieved
341:
330:. Retrieved
318:
307:. Retrieved
296:
285:. Retrieved
274:
263:. Retrieved
253:
242:. Retrieved
232:
221:. Retrieved
178:MAC flooding
175:
171:
161:
147:
141:
137:
128:
116:
108:
97:
93:MAC flooding
89:
77:
58:
40:
39:
24:
18:
112:MAC address
394:2012-04-07
373:2012-04-07
352:2024-08-10
332:2024-07-09
309:2012-01-27
287:2012-01-27
265:2012-01-27
244:2012-01-27
223:2021-03-08
200:References
36:Background
132:ARP cache
409:Category
188:See also
125:Remedies
95:attack.
390:. Cisco
144:Layer 2
42:Unicast
29:unicast
74:Causes
327:(PDF)
47:node
23:, a
100:ARP
19:In
411::
208:^
397:.
376:.
355:.
335:.
312:.
290:.
268:.
247:.
226:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.