27:
3110:
247:
However, due to the incomplete nature of the round function, two large ciphertexts of 53 or more 32-bit words identical in all but 12 words can be found by a simple brute-force collision search requiring 2 memory, 2 time and 2+2 chosen plaintexts, in other words with a total time*memory complexity of
204:
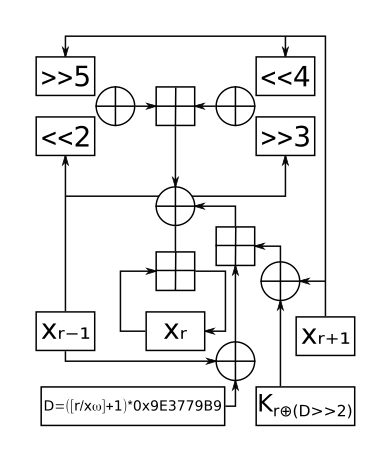
round function to each word in the block and combines it additively with its leftmost neighbour. Slow diffusion rate of the decryption process was immediately exploited to break the cipher. Corrected Block TEA uses a more involved round function which makes use of both immediate neighbours in
200:) block cipher. XXTEA operates on variable-length blocks that are some arbitrary multiple of 32 bits in size (minimum 64 bits). The number of full cycles depends on the block size, but there are at least six (rising to 32 for small block sizes). The original Block TEA applies the
248:
2, which is actually 2 for any such cipher. It is currently unknown if such partial collisions pose any threat to the security of the cipher. Eight full cycles would raise the bar for such collision search above complexity of parallel brute-force attacks.
251:
The unusually small size of the XXTEA algorithm would make it a viable option in situations where there are extreme constraints e.g. legacy hardware systems (perhaps embedded) where the amount of available
980:
or other unwanted behavior – it would be better placed inside the 'Coding Part' block. Also, in the definition of MX some programmers would prefer to use bracketing to clarify operator precedence.
225:
Even if the correct usage of always changing the data sent (possibly by a message number) is employed, only identical messages give the same result and the information leakage is minimal.
3090:
2920:
3180:
3185:
3170:
291:
To cipher "212 bytes or more" algorithm performs just 6 rounds, and carefully chosen bit patterns allows to detect and analyze avalanche effect.
2758:
2693:
1774:
189:, and the algorithm was presented in an unpublished technical report in October 1998 (Wheeler and Needham, 1998). It is not subject to any
284:
against full-round XXTEA with wide block, requiring 2 queries for a block size of 212 bytes or more, and negligible work. It is based on
186:
2520:
1876:
2510:
2004:
299:
The original formulation of the
Corrected Block TEA algorithm, published by David Wheeler and Roger Needham, is as follows:
2673:
2647:
2515:
2411:
215:
For ease of use and general security the large block version is to be preferred when applicable for the following reasons.
1680:
219:
A single bit change will change about one half of the bits of the entire block, leaving no place where the changes start.
2488:
182:
47:
2751:
228:
The message number should always be checked as this redundancy is the check against a random message being accepted.
2657:
1767:
2536:
235:
2969:
2900:
2714:
3165:
2744:
1804:
3085:
3040:
2843:
2600:
1760:
2964:
2617:
2527:
2505:
1818:
285:
234:
If it is not acceptable to have very long messages, they can be broken into chunks say of 60 words and
3080:
2622:
2478:
2431:
1906:
1636:
91:
3175:
3070:
3060:
2915:
2688:
2570:
2445:
1814:
239:
3065:
3055:
2848:
2808:
2801:
2786:
2781:
2627:
2416:
1787:
281:
167:
134:
3160:
2853:
2796:
2719:
2595:
2590:
2542:
196:
Formally speaking, XXTEA is a consistent incomplete source-heavy heterogeneous UFN (unbalanced
3113:
2959:
2905:
2709:
2532:
2391:
1969:
257:
960:
if n is zero result is 1 and no coding or decoding takes place, otherwise the result is zero
3075:
2999:
2612:
2495:
2421:
2104:
2084:
253:
111:
8:
2828:
2575:
2552:
1871:
997:#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key ^ z)))
3135:
2944:
2928:
2870:
2560:
2468:
2180:
2109:
2079:
2024:
977:
969:
3004:
2994:
2860:
2280:
1979:
1939:
1934:
1901:
1861:
1809:
26:
2939:
2791:
2652:
2547:
2426:
2285:
2165:
2134:
1828:
1724:
2499:
2483:
2472:
2406:
2365:
2330:
2260:
2240:
2114:
1994:
1989:
1944:
1699:
197:
307:#define MX ((z>>5^y<<2) + (y>>3^z<<4) ^ (sum^y) + (k^z))
3014:
2934:
2890:
2833:
2818:
2637:
2585:
2396:
2381:
2320:
2315:
2200:
1949:
1684:
104:
3154:
3095:
3050:
3009:
2989:
2880:
2838:
2813:
2632:
2580:
2459:
2441:
2230:
2205:
2195:
2019:
2009:
1856:
1624:
178:
126:
51:
3045:
2885:
2875:
2865:
2823:
2767:
2565:
2386:
2350:
2215:
2094:
2049:
1881:
1833:
1783:
261:
211:
Needham & Wheeler make the following comments on the use of Block TEA:
156:
144:
3024:
2175:
2170:
2054:
2984:
2954:
2949:
2910:
2607:
2325:
2265:
2149:
2144:
2089:
1959:
1822:
3140:
2974:
2340:
2335:
2225:
2139:
2034:
2014:
1722:
1697:
265:
160:
208:
XXTEA is likely to be more efficient than XTEA for longer messages.
3019:
2979:
2678:
2642:
2436:
2099:
1974:
1954:
1866:
81:
1661:
1627:
that, just like XXTEA, is designed to be very simple to implement.
170:
requiring 2 queries and negligible work. See cryptanalysis below.
2345:
2295:
2255:
2245:
2190:
2185:
2029:
1838:
269:
983:
A clarified version including those improvements is as follows:
2895:
2683:
2305:
2300:
2235:
2220:
2210:
2155:
2129:
2124:
2119:
1999:
1984:
190:
174:
2401:
2310:
2290:
2275:
2064:
2044:
1964:
1929:
2250:
2159:
2074:
2069:
2059:
2039:
1911:
1896:
1630:
943:
BTEA will encode or decode n words as a single block where
201:
69:
3145:
2355:
2270:
1891:
1886:
1620:
963:
assumes 32 bit 'long' and same endian coding and decoding
2921:
Cryptographically secure pseudorandom number generator
1723:
David J. Wheeler and Roger M. Needham (October 1998).
1698:
Roger M. Needham and David J. Wheeler (October 1997).
280:
An attack published in 2010 by E. Yarrkov presents a
1782:
1744:
1730:. Computer Laboratory, Cambridge University, England
1705:. Computer Laboratory, Cambridge University, England
1681:"Tinyness: An Overview of TEA and Related Ciphers"
1678:
231:Cut and join attacks do not appear to be possible.
3152:
1655:
1653:
159:designed to correct weaknesses in the original
2752:
1768:
1659:
1650:
3181:History of computing in the United Kingdom
2759:
2745:
1775:
1761:
3186:Science and technology in Cambridgeshire
137:requiring 2 queries and negligible work.
3171:Computer security in the United Kingdom
96:arbitrary, at least two words (64 bits)
3153:
2740:
1756:
968:Note that the initialization of z is
1716:
238:analogously to the methods used for
222:There is no choice of mode involved.
1691:
205:processing each word in the block.
13:
1672:
939:According to Needham and Wheeler:
25:
14:
3197:
3129:
1679:Matthew D. Russell (2004-02-27).
294:
116:depends on the block size; ~52+6*
3109:
3108:
2766:
275:
2970:Information-theoretic security
1:
1643:
256:is minimal, or alternatively
187:Cambridge Computer Laboratory
1660:Elias Yarrkov (2010-05-04).
7:
3136:a JavaScript implementation
3086:Message authentication code
3041:Cryptographic hash function
2844:Cryptographic hash function
1614:
951:v is the n word data vector
20:Corrected Block TEA (XXTEA)
10:
3202:
2965:Harvest now, decrypt later
957:n is negative for decoding
286:differential cryptanalysis
105:Unbalanced Feistel Network
3104:
3081:Post-quantum cryptography
3033:
2774:
2736:
2702:
2666:
2658:Time/memory/data tradeoff
2455:
2374:
1920:
1847:
1795:
1752:
1748:
1666:Cryptology ePrint Archive
976:< 1 which may cause a
166:XXTEA is vulnerable to a
133:XXTEA is vulnerable to a
132:
124:
110:
100:
90:
80:
75:
65:
57:
43:
38:
24:
3071:Quantum key distribution
3061:Authenticated encryption
2916:Random number generation
2446:Whitening transformation
1662:"Cryptanalysis of XXTEA"
1633:: Block TEA's precursor.
994:#define DELTA 0x9e3779b9
985:
304:#define DELTA 0x9e3779b9
301:
3066:Public-key cryptography
3056:Symmetric-key algorithm
2849:Key derivation function
2809:Cryptographic primitive
2802:Authentication protocol
2787:Outline of cryptography
2782:History of cryptography
2417:Confusion and diffusion
282:chosen-plaintext attack
168:chosen-plaintext attack
135:chosen-plaintext attack
2854:Secure Hash Algorithms
2797:Cryptographic protocol
966:
258:single-board computers
245:
151:(often referred to as
30:
2960:End-to-end encryption
2906:Cryptojacking malware
2710:Initialization vector
941:
213:
29:
3166:Broken block ciphers
3141:a PHP implementation
3076:Quantum cryptography
3000:Trusted timestamping
2489:3-subset MITM attack
2105:Intel Cascade Cipher
2085:Hasty Pudding cipher
1725:"Correction to XTEA"
3146:a CL implementation
2829:Cryptographic nonce
2528:Differential-linear
1639:: XTEA's precursor.
1360:/* Decoding Part */
954:k is the 4 word key
685:/* Decoding Part */
149:Corrected Block TEA
21:
2945:Subliminal channel
2929:Pseudorandom noise
2871:Key (cryptography)
2601:Differential-fault
1819:internal mechanics
978:segmentation fault
970:Undefined behavior
177:'s designers were
120:(6-32 full cycles)
33:One round of XXTEA
31:
19:
3126:
3125:
3122:
3121:
3005:Key-based routing
2995:Trapdoor function
2861:Digital signature
2732:
2731:
2728:
2727:
2715:Mode of operation
2392:Lai–Massey scheme
1108:/* Coding Part */
451:/* Coding Part */
141:
140:
3193:
3112:
3111:
2940:Insecure channel
2792:Classical cipher
2761:
2754:
2747:
2738:
2737:
2586:Power-monitoring
2427:Avalanche effect
2135:Khufu and Khafre
1788:security summary
1777:
1770:
1763:
1754:
1753:
1750:
1749:
1746:
1745:
1739:
1738:
1736:
1735:
1729:
1720:
1714:
1713:
1711:
1710:
1704:
1700:"Tea extensions"
1695:
1689:
1688:
1683:. Archived from
1676:
1670:
1669:
1657:
1610:
1607:
1604:
1601:
1598:
1595:
1592:
1589:
1586:
1583:
1580:
1577:
1574:
1571:
1568:
1565:
1562:
1559:
1556:
1553:
1550:
1547:
1544:
1541:
1538:
1535:
1532:
1529:
1526:
1523:
1520:
1517:
1514:
1511:
1508:
1505:
1502:
1499:
1496:
1493:
1490:
1487:
1484:
1481:
1478:
1475:
1472:
1469:
1466:
1463:
1460:
1457:
1454:
1451:
1448:
1445:
1442:
1439:
1436:
1433:
1430:
1427:
1424:
1421:
1418:
1415:
1412:
1409:
1406:
1403:
1400:
1397:
1394:
1391:
1388:
1385:
1382:
1379:
1376:
1373:
1370:
1367:
1364:
1361:
1358:
1355:
1352:
1349:
1346:
1343:
1340:
1337:
1334:
1331:
1328:
1325:
1322:
1319:
1316:
1313:
1310:
1307:
1304:
1301:
1298:
1295:
1292:
1289:
1286:
1283:
1280:
1277:
1274:
1271:
1268:
1265:
1262:
1259:
1256:
1253:
1250:
1247:
1244:
1241:
1238:
1235:
1232:
1229:
1226:
1223:
1220:
1217:
1214:
1211:
1208:
1205:
1202:
1199:
1196:
1193:
1190:
1187:
1184:
1181:
1178:
1175:
1172:
1169:
1166:
1163:
1160:
1157:
1154:
1151:
1148:
1145:
1142:
1139:
1136:
1133:
1130:
1127:
1124:
1121:
1118:
1115:
1112:
1109:
1106:
1103:
1100:
1097:
1094:
1091:
1088:
1085:
1082:
1079:
1076:
1073:
1070:
1067:
1064:
1061:
1058:
1055:
1052:
1049:
1046:
1043:
1040:
1037:
1034:
1031:
1028:
1025:
1022:
1019:
1016:
1013:
1010:
1007:
1004:
1001:
998:
995:
992:
991:<stdint.h>
989:
935:
932:
929:
926:
923:
920:
917:
914:
911:
908:
905:
902:
899:
896:
893:
890:
887:
884:
881:
878:
875:
872:
869:
866:
863:
860:
857:
854:
851:
848:
845:
842:
839:
836:
833:
830:
827:
824:
821:
818:
815:
812:
809:
806:
803:
800:
797:
794:
791:
788:
785:
782:
779:
776:
773:
770:
767:
764:
761:
758:
755:
752:
749:
746:
743:
740:
737:
734:
731:
728:
725:
722:
719:
716:
713:
710:
707:
704:
701:
698:
695:
692:
689:
686:
683:
680:
677:
674:
671:
668:
665:
662:
659:
656:
653:
650:
647:
644:
641:
638:
635:
632:
629:
626:
623:
620:
617:
614:
611:
608:
605:
602:
599:
596:
593:
590:
587:
584:
581:
578:
575:
572:
569:
566:
563:
560:
557:
554:
551:
548:
545:
542:
539:
536:
533:
530:
527:
524:
521:
518:
515:
512:
509:
506:
503:
500:
497:
494:
491:
488:
485:
482:
479:
476:
473:
470:
467:
464:
461:
458:
455:
452:
449:
446:
443:
440:
437:
434:
431:
428:
425:
422:
419:
416:
413:
410:
407:
404:
401:
398:
395:
392:
389:
386:
383:
380:
377:
374:
371:
368:
365:
362:
359:
356:
353:
350:
347:
344:
341:
338:
335:
332:
329:
326:
323:
320:
317:
314:
311:
308:
305:
22:
18:
3201:
3200:
3196:
3195:
3194:
3192:
3191:
3190:
3176:Feistel ciphers
3151:
3150:
3132:
3127:
3118:
3100:
3029:
2770:
2765:
2724:
2698:
2667:Standardization
2662:
2591:Electromagnetic
2543:Integral/Square
2500:Piling-up lemma
2484:Biclique attack
2473:EFF DES cracker
2457:
2451:
2382:Feistel network
2370:
1995:CIPHERUNICORN-E
1990:CIPHERUNICORN-A
1922:
1916:
1849:
1843:
1797:
1791:
1781:
1743:
1742:
1733:
1731:
1727:
1721:
1717:
1708:
1706:
1702:
1696:
1692:
1677:
1673:
1658:
1651:
1646:
1617:
1612:
1611:
1608:
1605:
1602:
1599:
1596:
1593:
1590:
1587:
1584:
1581:
1578:
1575:
1572:
1569:
1566:
1563:
1560:
1557:
1554:
1551:
1548:
1545:
1542:
1539:
1536:
1533:
1530:
1527:
1524:
1521:
1518:
1515:
1512:
1509:
1506:
1503:
1500:
1497:
1494:
1491:
1488:
1485:
1482:
1479:
1476:
1473:
1470:
1467:
1464:
1461:
1458:
1455:
1452:
1449:
1446:
1443:
1440:
1437:
1434:
1431:
1428:
1425:
1422:
1419:
1416:
1413:
1410:
1407:
1404:
1401:
1398:
1395:
1392:
1389:
1386:
1383:
1380:
1377:
1374:
1371:
1368:
1365:
1362:
1359:
1356:
1353:
1350:
1347:
1344:
1341:
1338:
1335:
1332:
1329:
1326:
1323:
1320:
1317:
1314:
1311:
1308:
1305:
1302:
1299:
1296:
1293:
1290:
1287:
1284:
1281:
1278:
1275:
1272:
1269:
1266:
1263:
1260:
1257:
1254:
1251:
1248:
1245:
1242:
1239:
1236:
1233:
1230:
1227:
1224:
1221:
1218:
1215:
1212:
1209:
1206:
1203:
1200:
1197:
1194:
1191:
1188:
1185:
1182:
1179:
1176:
1173:
1170:
1167:
1164:
1161:
1158:
1155:
1152:
1149:
1146:
1143:
1140:
1137:
1134:
1131:
1128:
1125:
1122:
1119:
1116:
1113:
1110:
1107:
1104:
1101:
1098:
1095:
1092:
1089:
1086:
1083:
1080:
1077:
1074:
1071:
1068:
1065:
1062:
1059:
1056:
1053:
1050:
1047:
1044:
1041:
1038:
1035:
1032:
1029:
1026:
1023:
1020:
1017:
1014:
1011:
1008:
1005:
1002:
999:
996:
993:
990:
987:
937:
936:
933:
930:
927:
924:
921:
918:
915:
912:
909:
906:
903:
900:
897:
894:
891:
888:
885:
882:
879:
876:
873:
870:
867:
864:
861:
858:
855:
852:
849:
846:
843:
840:
837:
834:
831:
828:
825:
822:
819:
816:
813:
810:
807:
804:
801:
798:
795:
792:
789:
786:
783:
780:
777:
774:
771:
768:
765:
762:
759:
756:
753:
750:
747:
744:
741:
738:
735:
732:
729:
726:
723:
720:
717:
714:
711:
708:
705:
702:
699:
696:
693:
690:
687:
684:
681:
678:
675:
672:
669:
666:
663:
660:
657:
654:
651:
648:
645:
642:
639:
636:
633:
630:
627:
624:
621:
618:
615:
612:
609:
606:
603:
600:
597:
594:
591:
588:
585:
582:
579:
576:
573:
570:
567:
564:
561:
558:
555:
552:
549:
546:
543:
540:
537:
534:
531:
528:
525:
522:
519:
516:
513:
510:
507:
504:
501:
498:
495:
492:
489:
486:
483:
480:
477:
474:
471:
468:
465:
462:
459:
456:
453:
450:
447:
444:
441:
438:
435:
432:
429:
426:
423:
420:
417:
414:
411:
408:
405:
402:
399:
396:
393:
390:
387:
384:
381:
378:
375:
372:
369:
366:
363:
360:
357:
354:
351:
348:
345:
342:
339:
336:
333:
330:
327:
324:
321:
318:
315:
312:
309:
306:
303:
297:
278:
198:Feistel network
58:First published
34:
17:
12:
11:
5:
3199:
3189:
3188:
3183:
3178:
3173:
3168:
3163:
3149:
3148:
3143:
3138:
3131:
3130:External links
3128:
3124:
3123:
3120:
3119:
3117:
3116:
3105:
3102:
3101:
3099:
3098:
3093:
3091:Random numbers
3088:
3083:
3078:
3073:
3068:
3063:
3058:
3053:
3048:
3043:
3037:
3035:
3031:
3030:
3028:
3027:
3022:
3017:
3015:Garlic routing
3012:
3007:
3002:
2997:
2992:
2987:
2982:
2977:
2972:
2967:
2962:
2957:
2952:
2947:
2942:
2937:
2935:Secure channel
2932:
2926:
2925:
2924:
2913:
2908:
2903:
2898:
2893:
2891:Key stretching
2888:
2883:
2878:
2873:
2868:
2863:
2858:
2857:
2856:
2851:
2846:
2836:
2834:Cryptovirology
2831:
2826:
2821:
2819:Cryptocurrency
2816:
2811:
2806:
2805:
2804:
2794:
2789:
2784:
2778:
2776:
2772:
2771:
2764:
2763:
2756:
2749:
2741:
2734:
2733:
2730:
2729:
2726:
2725:
2723:
2722:
2717:
2712:
2706:
2704:
2700:
2699:
2697:
2696:
2691:
2686:
2681:
2676:
2670:
2668:
2664:
2663:
2661:
2660:
2655:
2650:
2645:
2640:
2635:
2630:
2625:
2620:
2615:
2610:
2605:
2604:
2603:
2598:
2593:
2588:
2583:
2573:
2568:
2563:
2558:
2550:
2545:
2540:
2533:Distinguishing
2530:
2525:
2524:
2523:
2518:
2513:
2503:
2493:
2492:
2491:
2486:
2476:
2465:
2463:
2453:
2452:
2450:
2449:
2439:
2434:
2429:
2424:
2419:
2414:
2409:
2404:
2399:
2397:Product cipher
2394:
2389:
2384:
2378:
2376:
2372:
2371:
2369:
2368:
2363:
2358:
2353:
2348:
2343:
2338:
2333:
2328:
2323:
2318:
2313:
2308:
2303:
2298:
2293:
2288:
2283:
2278:
2273:
2268:
2263:
2258:
2253:
2248:
2243:
2238:
2233:
2228:
2223:
2218:
2213:
2208:
2203:
2198:
2193:
2188:
2183:
2178:
2173:
2168:
2163:
2152:
2147:
2142:
2137:
2132:
2127:
2122:
2117:
2112:
2107:
2102:
2097:
2092:
2087:
2082:
2077:
2072:
2067:
2062:
2057:
2052:
2047:
2042:
2037:
2032:
2027:
2025:Cryptomeria/C2
2022:
2017:
2012:
2007:
2002:
1997:
1992:
1987:
1982:
1977:
1972:
1967:
1962:
1957:
1952:
1947:
1942:
1937:
1932:
1926:
1924:
1918:
1917:
1915:
1914:
1909:
1904:
1899:
1894:
1889:
1884:
1879:
1874:
1869:
1864:
1859:
1853:
1851:
1845:
1844:
1842:
1841:
1836:
1831:
1826:
1812:
1807:
1801:
1799:
1793:
1792:
1780:
1779:
1772:
1765:
1757:
1741:
1740:
1715:
1690:
1687:on 2007-08-12.
1671:
1648:
1647:
1645:
1642:
1641:
1640:
1634:
1628:
1616:
1613:
986:
965:
964:
961:
958:
955:
952:
302:
296:
295:Reference code
293:
277:
274:
244:
243:
232:
229:
226:
223:
220:
139:
138:
130:
129:
122:
121:
114:
108:
107:
102:
98:
97:
94:
88:
87:
84:
78:
77:
73:
72:
67:
63:
62:
59:
55:
54:
45:
41:
40:
36:
35:
32:
15:
9:
6:
4:
3:
2:
3198:
3187:
3184:
3182:
3179:
3177:
3174:
3172:
3169:
3167:
3164:
3162:
3161:Block ciphers
3159:
3158:
3156:
3147:
3144:
3142:
3139:
3137:
3134:
3133:
3115:
3107:
3106:
3103:
3097:
3096:Steganography
3094:
3092:
3089:
3087:
3084:
3082:
3079:
3077:
3074:
3072:
3069:
3067:
3064:
3062:
3059:
3057:
3054:
3052:
3051:Stream cipher
3049:
3047:
3044:
3042:
3039:
3038:
3036:
3032:
3026:
3023:
3021:
3018:
3016:
3013:
3011:
3010:Onion routing
3008:
3006:
3003:
3001:
2998:
2996:
2993:
2991:
2990:Shared secret
2988:
2986:
2983:
2981:
2978:
2976:
2973:
2971:
2968:
2966:
2963:
2961:
2958:
2956:
2953:
2951:
2948:
2946:
2943:
2941:
2938:
2936:
2933:
2930:
2927:
2922:
2919:
2918:
2917:
2914:
2912:
2909:
2907:
2904:
2902:
2899:
2897:
2894:
2892:
2889:
2887:
2884:
2882:
2881:Key generator
2879:
2877:
2874:
2872:
2869:
2867:
2864:
2862:
2859:
2855:
2852:
2850:
2847:
2845:
2842:
2841:
2840:
2839:Hash function
2837:
2835:
2832:
2830:
2827:
2825:
2822:
2820:
2817:
2815:
2814:Cryptanalysis
2812:
2810:
2807:
2803:
2800:
2799:
2798:
2795:
2793:
2790:
2788:
2785:
2783:
2780:
2779:
2777:
2773:
2769:
2762:
2757:
2755:
2750:
2748:
2743:
2742:
2739:
2735:
2721:
2718:
2716:
2713:
2711:
2708:
2707:
2705:
2701:
2695:
2692:
2690:
2687:
2685:
2682:
2680:
2677:
2675:
2672:
2671:
2669:
2665:
2659:
2656:
2654:
2651:
2649:
2646:
2644:
2641:
2639:
2636:
2634:
2631:
2629:
2626:
2624:
2621:
2619:
2616:
2614:
2613:Interpolation
2611:
2609:
2606:
2602:
2599:
2597:
2594:
2592:
2589:
2587:
2584:
2582:
2579:
2578:
2577:
2574:
2572:
2569:
2567:
2564:
2562:
2559:
2557:
2556:
2551:
2549:
2546:
2544:
2541:
2538:
2534:
2531:
2529:
2526:
2522:
2519:
2517:
2514:
2512:
2509:
2508:
2507:
2504:
2501:
2497:
2494:
2490:
2487:
2485:
2482:
2481:
2480:
2477:
2474:
2470:
2467:
2466:
2464:
2461:
2460:cryptanalysis
2454:
2447:
2443:
2442:Key whitening
2440:
2438:
2435:
2433:
2430:
2428:
2425:
2423:
2420:
2418:
2415:
2413:
2410:
2408:
2405:
2403:
2400:
2398:
2395:
2393:
2390:
2388:
2385:
2383:
2380:
2379:
2377:
2373:
2367:
2364:
2362:
2359:
2357:
2354:
2352:
2349:
2347:
2344:
2342:
2339:
2337:
2334:
2332:
2329:
2327:
2324:
2322:
2319:
2317:
2314:
2312:
2309:
2307:
2304:
2302:
2299:
2297:
2294:
2292:
2289:
2287:
2284:
2282:
2279:
2277:
2274:
2272:
2269:
2267:
2264:
2262:
2259:
2257:
2254:
2252:
2249:
2247:
2244:
2242:
2239:
2237:
2234:
2232:
2231:New Data Seal
2229:
2227:
2224:
2222:
2219:
2217:
2214:
2212:
2209:
2207:
2204:
2202:
2199:
2197:
2194:
2192:
2189:
2187:
2184:
2182:
2179:
2177:
2174:
2172:
2169:
2167:
2164:
2161:
2157:
2153:
2151:
2148:
2146:
2143:
2141:
2138:
2136:
2133:
2131:
2128:
2126:
2123:
2121:
2118:
2116:
2113:
2111:
2108:
2106:
2103:
2101:
2098:
2096:
2093:
2091:
2088:
2086:
2083:
2081:
2078:
2076:
2073:
2071:
2068:
2066:
2063:
2061:
2058:
2056:
2053:
2051:
2048:
2046:
2043:
2041:
2038:
2036:
2033:
2031:
2028:
2026:
2023:
2021:
2018:
2016:
2013:
2011:
2008:
2006:
2003:
2001:
1998:
1996:
1993:
1991:
1988:
1986:
1983:
1981:
1978:
1976:
1973:
1971:
1970:BEAR and LION
1968:
1966:
1963:
1961:
1958:
1956:
1953:
1951:
1948:
1946:
1943:
1941:
1938:
1936:
1933:
1931:
1928:
1927:
1925:
1919:
1913:
1910:
1908:
1905:
1903:
1900:
1898:
1895:
1893:
1890:
1888:
1885:
1883:
1880:
1878:
1875:
1873:
1870:
1868:
1865:
1863:
1860:
1858:
1855:
1854:
1852:
1846:
1840:
1837:
1835:
1832:
1830:
1827:
1824:
1820:
1816:
1813:
1811:
1808:
1806:
1803:
1802:
1800:
1794:
1789:
1785:
1784:Block ciphers
1778:
1773:
1771:
1766:
1764:
1759:
1758:
1755:
1751:
1747:
1726:
1719:
1701:
1694:
1686:
1682:
1675:
1667:
1663:
1656:
1654:
1649:
1638:
1635:
1632:
1629:
1626:
1625:stream cipher
1622:
1619:
1618:
984:
981:
979:
975:
971:
962:
959:
956:
953:
950:
949:
948:
946:
940:
300:
292:
289:
287:
283:
276:Cryptanalysis
273:
271:
267:
263:
259:
255:
249:
241:
237:
233:
230:
227:
224:
221:
218:
217:
216:
212:
209:
206:
203:
199:
194:
192:
188:
184:
183:David Wheeler
180:
179:Roger Needham
176:
171:
169:
164:
162:
158:
154:
150:
146:
136:
131:
128:
127:cryptanalysis
123:
119:
115:
113:
109:
106:
103:
99:
95:
93:
89:
85:
83:
79:
76:Cipher detail
74:
71:
68:
64:
60:
56:
53:
52:Roger Needham
49:
48:David Wheeler
46:
42:
37:
28:
23:
3046:Block cipher
2886:Key schedule
2876:Key exchange
2866:Kleptography
2824:Cryptosystem
2768:Cryptography
2618:Partitioning
2576:Side-channel
2554:
2521:Higher-order
2506:Differential
2387:Key schedule
2360:
1732:. Retrieved
1718:
1707:. Retrieved
1693:
1685:the original
1674:
1665:
982:
973:
967:
944:
942:
938:
298:
290:
279:
262:Raspberry Pi
260:such as the
250:
246:
214:
210:
207:
195:
172:
165:
157:block cipher
152:
148:
145:cryptography
142:
125:Best public
117:
66:Derived from
61:October 1998
16:Block cipher
3034:Mathematics
3025:Mix network
2703:Utilization
2689:NSA Suite B
2674:AES process
2623:Rubber-hose
2561:Related-key
2469:Brute-force
1848:Less common
92:Block sizes
3155:Categories
2985:Ciphertext
2955:Decryption
2950:Encryption
2911:Ransomware
2653:Chi-square
2571:Rotational
2511:Impossible
2432:Block size
2326:Spectr-H64
2150:Ladder-DES
2145:Kuznyechik
2090:Hierocrypt
1960:BassOmatic
1923:algorithms
1850:algorithms
1823:Triple DES
1798:algorithms
1734:2008-07-04
1709:2008-07-04
1644:References
409:0x9e3779b9
2975:Plaintext
2628:Black-bag
2548:Boomerang
2537:Known-key
2516:Truncated
2341:Threefish
2336:SXAL/MBAL
2226:MultiSwap
2181:MacGuffin
2140:KN-Cipher
2080:Grand Cru
2035:CS-Cipher
2015:COCONUT98
266:Banana Pi
161:Block TEA
101:Structure
82:Key sizes
70:Block TEA
44:Designers
3114:Category
3020:Kademlia
2980:Codetext
2923:(CSPRNG)
2901:Machines
2679:CRYPTREC
2643:Weak key
2596:Acoustic
2437:Key size
2281:Red Pike
2100:IDEA NXT
1980:Chiasmus
1975:CAST-256
1955:BaseKing
1940:Akelarre
1935:Adiantum
1902:Skipjack
1867:CAST-128
1862:Camellia
1810:Blowfish
1615:See also
1450:>>
1189:>>
1066:unsigned
1045:uint32_t
1030:uint32_t
1009:uint32_t
988:#include
778:>>
526:>>
355:unsigned
86:128 bits
2775:General
2720:Padding
2638:Rebound
2346:Treyfer
2296:SAVILLE
2256:PRESENT
2246:NOEKEON
2191:MAGENTA
2186:Madryga
2166:Lucifer
2030:CRYPTON
1839:Twofish
1829:Serpent
947:> 1
270:Arduino
236:chained
191:patents
185:of the
155:) is a
39:General
2896:Keygen
2684:NESSIE
2633:Davies
2581:Timing
2496:Linear
2456:Attack
2375:Design
2366:Zodiac
2331:Square
2306:SHACAL
2301:SC2000
2261:Prince
2241:Nimbus
2236:NewDES
2221:MULTI2
2211:MISTY1
2154:LOKI (
2130:KHAZAD
2125:KeeLoq
2120:KASUMI
2115:Kalyna
2000:CLEFIA
1985:CIKS-1
1945:Anubis
1796:Common
1600:rounds
1408:rounds
1378:rounds
1327:rounds
1111:rounds
1075:rounds
925:return
913:return
649:return
175:cipher
112:Rounds
2931:(PRN)
2566:Slide
2422:Round
2407:P-box
2402:S-box
2361:XXTEA
2321:Speck
2316:Simon
2311:SHARK
2291:SAFER
2276:REDOC
2201:Mercy
2160:89/91
2110:Iraqi
2075:G-DES
2065:FEA-M
2045:DES-X
2010:Cobra
1965:BATON
1950:Ascon
1930:3-Way
1921:Other
1728:(PDF)
1703:(PDF)
1591:while
1582:DELTA
1459:&
1414:DELTA
1318:while
1198:&
1171:DELTA
1033:const
904:DELTA
787:&
745:while
739:DELTA
535:&
508:DELTA
478:while
403:DELTA
153:XXTEA
118:words
2694:CNSA
2553:Mod
2479:MITM
2251:NUSH
2206:MESH
2196:MARS
2070:FROG
2060:FEAL
2040:DEAL
2020:Crab
2005:CMEA
1912:XTEA
1897:SEED
1877:IDEA
1872:GOST
1857:ARIA
1631:XTEA
1623:: A
1492:>
1348:<
1336:else
1228:<
1096:>
1003:btea
1000:void
972:for
820:>
673:<
661:else
565:<
490:>
439:>
415:long
358:long
340:long
331:long
319:long
313:btea
310:long
202:XTEA
181:and
173:The
2648:Tau
2608:XSL
2412:SPN
2356:xmx
2351:UES
2286:S-1
2271:RC2
2216:MMB
2095:ICE
2050:DFC
1907:TEA
1892:RC6
1887:RC5
1882:LEA
1834:SM4
1815:DES
1805:AES
1637:TEA
1621:RC4
1576:sum
1468:for
1447:sum
1402:sum
1207:for
1186:sum
1165:sum
1135:sum
1060:sum
1036:key
1021:int
898:sum
796:for
775:sum
751:sum
727:sum
544:for
523:sum
502:sum
385:sum
268:or
254:RAM
240:DES
143:In
3157::
2176:M8
2171:M6
2158:,
2156:97
2055:E2
1821:,
1664:.
1652:^
1603:);
1597:--
1579:-=
1570:MX
1567:-=
1537:MX
1534:-=
1504:--
1483:-1
1432:do
1390:52
1351:-1
1339:if
1330:);
1324:--
1309:MX
1306:+=
1276:MX
1273:+=
1243:++
1234:-1
1168:+=
1159:do
1123:52
1087:if
901:-=
892:MX
889:-=
862:MX
859:-=
832:--
811:-1
754:!=
715:52
676:-1
664:if
640:MX
637:+=
610:MX
607:+=
580:++
571:-1
505:+=
487:--
466:52
430:if
288:.
272:.
264:,
193:.
163:.
147:,
50:,
2760:e
2753:t
2746:v
2555:n
2539:)
2535:(
2502:)
2498:(
2475:)
2471:(
2462:)
2458:(
2448:)
2444:(
2266:Q
2162:)
1825:)
1817:(
1790:)
1786:(
1776:e
1769:t
1762:v
1737:.
1712:.
1668:.
1609:}
1606:}
1594:(
1588:}
1585:;
1573:;
1564:v
1561:=
1558:y
1555:;
1552:v
1549:=
1546:z
1543:}
1540:;
1531:v
1528:=
1525:y
1522:;
1519:v
1516:=
1513:z
1510:{
1507:)
1501:p
1498:;
1495:0
1489:p
1486:;
1480:n
1477:=
1474:p
1471:(
1465:;
1462:3
1456:)
1453:2
1444:(
1441:=
1438:e
1435:{
1429:;
1426:v
1423:=
1420:y
1417:;
1411:*
1405:=
1399:;
1396:n
1393:/
1387:+
1384:6
1381:=
1375:;
1372:n
1369:-
1366:=
1363:n
1357:{
1354:)
1345:n
1342:(
1333:}
1321:(
1315:}
1312:;
1303:v
1300:=
1297:z
1294:;
1291:v
1288:=
1285:y
1282:}
1279:;
1270:v
1267:=
1264:z
1261:;
1258:v
1255:=
1252:y
1249:{
1246:)
1240:p
1237:;
1231:n
1225:p
1222:;
1219:0
1216:=
1213:p
1210:(
1204:;
1201:3
1195:)
1192:2
1183:(
1180:=
1177:e
1174:;
1162:{
1156:;
1153:v
1150:=
1147:z
1144:;
1141:0
1138:=
1132:;
1129:n
1126:/
1120:+
1117:6
1114:=
1105:{
1102:)
1099:1
1093:n
1090:(
1084:;
1081:e
1078:,
1072:,
1069:p
1063:;
1057:,
1054:z
1051:,
1048:y
1042:{
1039:)
1027:,
1024:n
1018:,
1015:v
1012:*
1006:(
974:n
945:n
934:}
931:;
928:1
922:}
919:;
916:0
910:}
907:;
895:;
886:v
883:=
880:y
877:;
874:v
871:=
868:z
865:;
856:v
853:=
850:y
847:,
844:v
841:=
838:z
835:)
829:p
826:;
823:0
817:p
814:;
808:n
805:=
802:p
799:(
793:;
790:3
784:)
781:2
772:(
769:=
766:e
763:{
760:)
757:0
748:(
742:;
736:*
733:q
730:=
724:;
721:n
718:/
712:+
709:6
706:=
703:q
700:;
697:n
694:-
691:=
688:n
682:{
679:)
670:n
667:(
658:}
655:;
652:0
646:}
643:;
634:v
631:=
628:z
625:;
622:v
619:=
616:y
613:;
604:v
601:=
598:z
595:,
592:v
589:=
586:y
583:)
577:p
574:;
568:n
562:p
559:;
556:0
553:=
550:p
547:(
541:;
538:3
532:)
529:2
520:(
517:=
514:e
511:;
499:{
496:)
493:0
484:q
481:(
475:;
472:n
469:/
463:+
460:6
457:=
454:q
448:{
445:)
442:1
436:n
433:(
427:;
424:q
421:,
418:p
412:;
406:=
400:,
397:e
394:,
391:0
388:=
382:,
379:v
376:=
373:y
370:,
367:v
364:=
361:z
352:{
349:)
346:k
343:*
337:,
334:n
328:,
325:v
322:*
316:(
242:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.