362:, which typically negotiate communication parameters for a brief period when a connection is first established, and there after use those parameters to provide optimal information transfer over the channel as a function of its quality and capacity. The "squealing" (which is actually a sound that changes in pitch 100 times every second) noises made by some modems with speaker output immediately after a connection is established are in fact the sounds of modems at both ends engaging in a handshaking procedure; once the procedure is completed, the speaker might be silenced, depending on the settings of operating system or the application controlling the modem.
328:(SSL or TLS) connection starts, the record encapsulates a "control" protocol—the handshake messaging protocol (content type 22). This protocol is used to exchange all the information required by both sides for the exchange of the actual application data by TLS. It defines the messages formatting or containing this information and the order of their exchange. These may vary according to the demands of the client and server—i.e., there are several possible procedures to set up the connection. This initial exchange results in a successful TLS connection (both parties ready to transfer application data with TLS) or an alert message (as specified below).
165:
25:
293:
The reason for the client and server not using a default sequence number such as 0 for establishing the connection is to protect against two incarnations of the same connection reusing the same sequence number too soon, which means a segment from an earlier incarnation of a connection might interfere
143:
A simple handshaking protocol might only involve the receiver sending a message meaning "I received your last message and I am ready for you to send me another one." A more complex handshaking protocol might allow the sender to ask the receiver if it is ready to receive or for the receiver to reply
382:
In mobile device chargers offering special quick-charge abilities to supported devices, the charging process will switch up to a higher output voltage for increased power transfer. But this could cause serious damage to an unsupported device or even result in a fire. It is therefore very important
139:
or hardware features. Handshaking is a technique of communication between two entities. However, within TCP/IP RFCs, the term "handshake" is most commonly used to reference the TCP three-way handshake. For example, the term "handshake" is not present in RFCs covering FTP or SMTP. One exception is
383:
for the device and charger to first perform a handshake to "agree" on mutually supported charge parameters. If such a charger can't identify the connected device or determine its compatibility, it will default to normal but much slower charge parameters within the USB standard.
107:") through the exchange of information that establishes the protocols of a communication link at the start of the communication, before full communication begins. The handshaking process usually takes place in order to establish rules for communication when a
111:
attempts to communicate with another device. Signals are usually exchanged between two devices to establish a communication link. For example, when a computer communicates with another device such as a
289:
In this setup, the synchronize messages act as service requests from one server to the other, while the acknowledgement messages return to the requesting server to let it know the message was received.
370:
This frequently used term describes the use of RTS and CTS signals over a serial interconnection. It is, however, not quite correct; it's not a true form of handshaking, and is better described as
151:
Handshaking facilitates connecting relatively heterogeneous systems or equipment over a communication channel without the need for human intervention to set parameters.
140:
Transport Layer
Security, TLS, setup, FTP RFC 4217. In place of the term "handshake", FTP RFC 3659 substitutes the term "conversation" for the passing of commands.
282:
253:
227:
200:
116:, the two devices will signal each other that they are switched on and ready to work, as well as to agree to which protocols are being used.
39:
746:
716:
119:
Handshaking can negotiate parameters that are acceptable to equipment and systems at both ends of the communication channel, including
173:
549:
307:
144:
with a negative acknowledgement meaning "I did not receive your last message correctly, please resend it" (e.g., if the data was
81:
is a signal between two devices or programs, used to, e.g., authenticate, coordinate. An example is the handshaking between a
627:
433:
500:
319:
182:
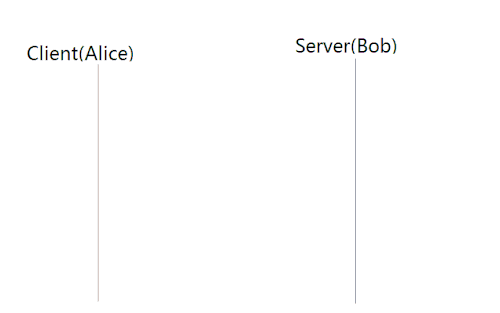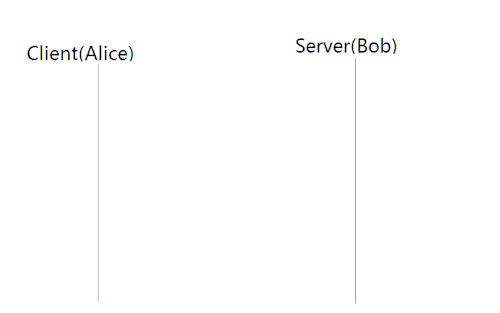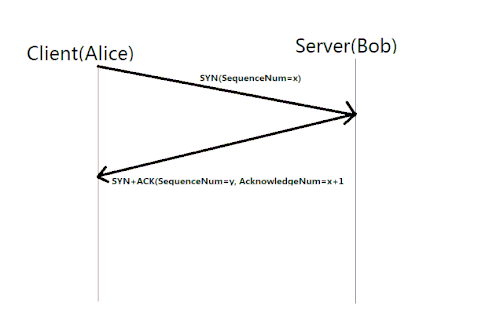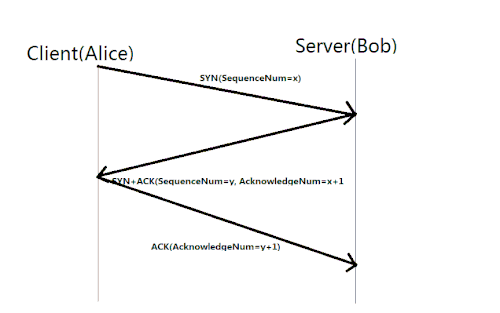
The first host (Alice) sends the second host (Bob) a "synchronize" (SYN) message with its own sequence number
799:
632:
542:
303:
726:
804:
794:
751:
647:
756:
340:
731:
721:
642:
535:
325:
741:
637:
587:
577:
356:
86:
400:
476:
659:
572:
331:
The protocol is used to negotiate the secure attributes of a session. (RFC 5246, p. 37)
514:
136:
8:
261:
232:
38:
Please expand the article to include this information. Further details may exist on the
212:
185:
96:
429:
344:
64:
504:
558:
145:
89:
71:
517:
494:
597:
258:
Alice replies with an acknowledgment (ACK) message with acknowledgement number
164:
788:
104:
59:
This article is about the computer science term. For the greeting habit, see
687:
677:
103:
is an automated process of negotiation between two participants (example "
128:
82:
667:
622:
509:
132:
60:
70:"Automatic negotiation" redirects here. For the Ethernet usage, see
761:
612:
592:
310:
to negotiate authentication, encryption and maximum message size.
124:
120:
108:
527:
617:
206:
24:
736:
607:
582:
371:
306:(SMTP) is the key Internet standard for email transmission. It
428:. Australia: John Wiley & Sons Australia. pp. 92–93.
771:
766:
711:
695:
672:
359:
113:
466:
FTP 959, 3659 (conversation), 2228,4217 (TLS handshake),5797
602:
284:, which Bob receives and to which he doesn't need to reply.
426:
Jacaranda
Information Processes and Technology: HSC Course
365:
496:
The
Transport Layer Security (TLS) Protocol, version 1.2
264:
235:
215:
188:
424:Ware, Peter; Chivers, Bill; Cheleski, Paul (2001).
423:
401:"What is handshaking? - Definition from WhatIs.com"
276:
247:
221:
194:
786:
205:Bob replies with a synchronize-acknowledgment (
355:One classic example of handshaking is that of
543:
320:Transport Layer Security § TLS handshake
294:with a later incarnation of the connection.
36:about Handshaking in, e.g., buses, software.
550:
536:
176:connection requires three separate steps:
159:
508:
377:
457:SMTP RFC 821,5321, 2821, 1869,6531, 2822
350:
163:
209:) message with its own sequence number
787:
16:Signal between two devices or programs
531:
343:uses a four-way handshake defined in
18:
557:
13:
63:. For the mathematical lemma, see
14:
816:
481:TheFreeDictionary's Encyclopedia
334:
313:
168:Example of three way handshaking
23:
487:
469:
460:
451:
442:
417:
393:
1:
386:
366:Serial "Hardware Handshaking"
304:Simple Mail Transfer Protocol
7:
229:and acknowledgement number
10:
821:
341:WPA2 standard for wireless
317:
154:
69:
58:
704:
686:
658:
565:
121:information transfer rate
326:Transport Layer Security
85:and an application in a
297:
255:, which Alice receives.
160:TCP three-way handshake
378:Mobile device charging
278:
249:
223:
196:
172:Establishing a normal
169:
34:is missing information
351:Dial-up access modems
279:
250:
224:
202:, which Bob receives.
197:
167:
135:procedure, and other
800:Network architecture
308:includes handshaking
262:
233:
213:
186:
705:Long range wireless
277:{\displaystyle y+1}
248:{\displaystyle x+1}
274:
245:
219:
192:
170:
97:telecommunications
805:Network protocols
795:Data transmission
782:
781:
448:TCP RFC 793, 2581
345:IEEE 802.11i-2004
222:{\displaystyle y}
195:{\displaystyle x}
65:Handshaking lemma
57:
56:
812:
552:
545:
538:
529:
528:
522:
521:
512:
510:10.17487/RFC5246
491:
485:
484:
473:
467:
464:
458:
455:
449:
446:
440:
439:
421:
415:
414:
412:
411:
405:SearchNetworking
397:
283:
281:
280:
275:
254:
252:
251:
246:
228:
226:
225:
220:
201:
199:
198:
193:
77:In computing, a
52:
49:
43:
27:
19:
820:
819:
815:
814:
813:
811:
810:
809:
785:
784:
783:
778:
700:
682:
654:
561:
559:Internet access
556:
526:
525:
503:. August 2008.
493:
492:
488:
475:
474:
470:
465:
461:
456:
452:
447:
443:
436:
422:
418:
409:
407:
399:
398:
394:
389:
380:
368:
353:
337:
322:
316:
300:
263:
260:
259:
234:
231:
230:
214:
211:
210:
187:
184:
183:
162:
157:
90:virtual machine
75:
72:Autonegotiation
68:
53:
47:
44:
37:
28:
17:
12:
11:
5:
818:
808:
807:
802:
797:
780:
779:
777:
776:
775:
774:
764:
759:
754:
749:
744:
739:
734:
729:
724:
719:
714:
708:
706:
702:
701:
699:
698:
692:
690:
684:
683:
681:
680:
675:
670:
664:
662:
656:
655:
653:
652:
651:
650:
640:
635:
630:
625:
620:
615:
610:
605:
600:
595:
590:
585:
580:
575:
569:
567:
563:
562:
555:
554:
547:
540:
532:
524:
523:
486:
468:
459:
450:
441:
435:978-0701634728
434:
416:
391:
390:
388:
385:
379:
376:
367:
364:
352:
349:
336:
333:
318:Main article:
315:
312:
299:
296:
291:
290:
287:
286:
285:
273:
270:
267:
256:
244:
241:
238:
218:
203:
191:
161:
158:
156:
153:
55:
54:
31:
29:
22:
15:
9:
6:
4:
3:
2:
817:
806:
803:
801:
798:
796:
793:
792:
790:
773:
770:
769:
768:
765:
763:
760:
758:
755:
753:
750:
748:
745:
743:
740:
738:
735:
733:
730:
728:
725:
723:
720:
718:
715:
713:
710:
709:
707:
703:
697:
694:
693:
691:
689:
685:
679:
676:
674:
671:
669:
666:
665:
663:
661:
657:
649:
646:
645:
644:
641:
639:
636:
634:
631:
629:
626:
624:
621:
619:
616:
614:
611:
609:
606:
604:
601:
599:
596:
594:
591:
589:
586:
584:
581:
579:
576:
574:
571:
570:
568:
564:
560:
553:
548:
546:
541:
539:
534:
533:
530:
519:
516:
511:
506:
502:
498:
497:
490:
482:
478:
477:"handshaking"
472:
463:
454:
445:
437:
431:
427:
420:
406:
402:
396:
392:
384:
375:
373:
363:
361:
358:
348:
346:
342:
335:WPA2 wireless
332:
329:
327:
321:
314:TLS handshake
311:
309:
305:
295:
288:
271:
268:
265:
257:
242:
239:
236:
216:
208:
204:
189:
181:
180:
179:
178:
177:
175:
166:
152:
149:
147:
141:
138:
134:
130:
126:
122:
117:
115:
110:
106:
105:Alice and Bob
102:
98:
93:
91:
88:
84:
80:
73:
66:
62:
51:
48:December 2021
41:
35:
32:This article
30:
26:
21:
20:
688:Wireless LAN
678:Wireless USB
660:Wireless PAN
495:
489:
480:
471:
462:
453:
444:
425:
419:
408:. Retrieved
404:
395:
381:
372:flow control
369:
354:
338:
330:
323:
301:
292:
171:
150:
142:
118:
100:
94:
78:
76:
45:
33:
148:en route).
789:Categories
752:Muni Wi-Fi
643:Power-line
410:2018-02-19
387:References
83:hypervisor
757:Satellite
668:Bluetooth
648:Broadband
623:IEEE 1901
146:corrupted
133:interrupt
123:, coding
101:handshake
79:handshake
61:Handshake
40:talk page
762:UMTS-TDD
613:HomePlug
593:Ethernet
137:protocol
125:alphabet
109:computer
618:HomePNA
578:Dial-up
357:dial-up
324:When a
207:SYN-ACK
155:Example
737:iBurst
608:Nessum
583:DOCSIS
432:
360:modems
129:parity
772:WiBro
767:WiMAX
712:5G NR
696:Wi-Fi
673:Li-Fi
573:Cable
566:Wired
114:modem
87:guest
747:MMDS
732:HSPA
727:GPRS
722:EVDO
717:DECT
633:MoCA
628:ISDN
603:G.hn
598:FTTx
518:5246
501:IETF
430:ISBN
339:The
302:The
298:SMTP
99:, a
742:LTE
638:PON
588:DSL
515:RFC
505:doi
174:TCP
95:In
791::
513:.
499:.
479:.
403:.
374:.
347:.
131:,
127:,
92:.
551:e
544:t
537:v
520:.
507::
483:.
438:.
413:.
272:1
269:+
266:y
243:1
240:+
237:x
217:y
190:x
74:.
67:.
50:)
46:(
42:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.