1068:. Although microkernels are very small by themselves, in combination with all their required auxiliary code they are, in fact, often larger than monolithic kernels. Advocates of monolithic kernels also point out that the two-tiered structure of microkernel systems, in which most of the operating system does not interact directly with the hardware, creates a not-insignificant cost in terms of system efficiency. These types of kernels normally provide only the minimal services such as defining memory address spaces, inter-process communication (IPC) and the process management. The other functions such as running the hardware processes are not handled directly by microkernels. Proponents of microkernels point out those monolithic kernels have the disadvantage that an error in the kernel can cause the entire system to crash. However, with a microkernel, if a kernel process crashes, it is still possible to prevent a crash of the system as a whole by merely restarting the service that caused the error.
547:
may be able to perform many different operations, including read, write, delete or execute, but a user-level application may only be permitted to perform some of these operations (e.g., it may only be allowed to read the file). A common implementation of this is for the kernel to provide an object to the application (typically so called a "file handle") which the application may then invoke operations on, the validity of which the kernel checks at the time the operation is requested. Such a system may be extended to cover all objects that the kernel manages, and indeed to objects provided by other user applications.
562:
needs to access an object protected by a capability, it performs a system call and the kernel then checks whether the application's capability grants it permission to perform the requested action, and if it is permitted performs the access for it (either directly, or by delegating the request to another user-level process). The performance cost of address space switching limits the practicality of this approach in systems with complex interactions between objects, but it is used in current operating systems for objects that are not accessed frequently or which are not expected to perform quickly.
319:) on behalf of the OS. It provides the operating system with an API, procedures and information about how to control and communicate with a certain piece of hardware. Device drivers are an important and vital dependency for all OS and their applications. The design goal of a driver is abstraction; the function of the driver is to translate the OS-mandated abstract function calls (programming calls) into device-specific calls. In theory, a device should work correctly with a suitable driver. Device drivers are used for e.g. video cards, sound cards, printers, scanners, modems, and Network cards.
1267:. Hybrid kernels are similar to microkernels, except they include some additional code in kernel-space to increase performance. These kernels represent a compromise that was implemented by some developers to accommodate the major advantages of both monolithic and microkernels. These types of kernels are extensions of microkernels with some properties of monolithic kernels. Unlike monolithic kernels, these types of kernels are unable to load modules at runtime on their own. This implies running some services (such as the
1014:
systems, and network stacks. Microkernels were invented as a reaction to traditional "monolithic" kernel design, whereby all system functionality was put in a one static program running in a special "system" mode of the processor. In the microkernel, only the most fundamental of tasks are performed such as being able to access some (not necessarily all) of the hardware, manage memory and coordinate message passing between the processes. Some systems that use microkernels are QNX and the HURD. In the case of
874:
be accessed by most programs which cannot be put in a library is in the kernel space: Device drivers, scheduler, memory handling, file systems, and network stacks. Many system calls are provided to applications, to allow them to access all those services. A monolithic kernel, while initially loaded with subsystems that may not be needed, can be tuned to a point where it is as fast as or faster than the one that was specifically designed for the hardware, although more relevant in a general sense.
1350:), providing application developers with the functionalities of a conventional operating system. This comes down to every user writing their own rest-of-the kernel from near scratch, which is a very-risky, complex and quite a daunting assignment - particularly in a time-constrained production-oriented environment, which is why exokernels have never caught on. A major advantage of exokernel-based systems is that they can incorporate multiple library operating systems, each exporting a different
268:. Virtual addressing allows the kernel to make a given physical address appear to be another address, the virtual address. Virtual address spaces may be different for different processes; the memory that one process accesses at a particular (virtual) address may be different memory from what another process accesses at the same address. This allows every program to behave as if it is the only one (apart from the kernel) running and thus prevents applications from crashing each other.
280:). As a result, operating systems can allow programs to use more memory than the system has physically available. When a program needs data which is not currently in RAM, the CPU signals to the kernel that this has happened, and the kernel responds by writing the contents of an inactive memory block to disk (if necessary) and replacing it with the data requested by the program. The program can then be resumed from the point where it was stopped. This scheme is generally known as
1541:
955:
799:), which is common in conventional commercial systems; in fact, every module needing protection is therefore preferably included into the kernel. This link between monolithic design and "privileged mode" can be reconducted to the key issue of mechanism-policy separation; in fact the "privileged mode" architectural approach melds together the protection mechanism with the security policies, while the major alternative architectural approach,
905:
Hence, not far to travel at all. The monolithic Linux kernel can be made extremely small not only because of its ability to dynamically load modules but also because of its ease of customization. In fact, there are some versions that are small enough to fit together with a large number of utilities and other programs on a single floppy disk and still provide a fully functional operating system (one of the most popular of which is
1213:
854:
27:
242:(IPC). These implementations may be located within the kernel itself or the kernel can also rely on other processes it is running. Although the kernel must provide IPC in order to provide access to the facilities provided by each other, kernels must also provide running programs with a method to make requests to access these facilities. The kernel is also responsible for context switching between processes or threads.
1279:
code tainted module has the potential to destabilize a running kernel. It is possible to write a driver for a microkernel in a completely separate memory space and test it before "going" live. When a kernel module is loaded, it accesses the monolithic portion's memory space by adding to it what it needs, therefore, opening the doorway to possible pollution. A few advantages to the modular (or) Hybrid kernel are:
1075:. Servers allow the operating system to be modified by simply starting and stopping programs. For a machine without networking support, for instance, the networking server is not started. The task of moving in and out of the kernel to move data between the various applications and servers creates overhead which is detrimental to the efficiency of microkernels in comparison with monolithic kernels.
202:(RAM) is used to store both program instructions and data. Typically, both need to be present in memory in order for a program to execute. Often multiple programs will want access to memory, frequently demanding more memory than the computer has available. The kernel is responsible for deciding which memory each process can use, and determining what to do when not enough memory is available.
1166:), which some developers argue is necessary to increase the performance of the system. Some developers also maintain that monolithic systems are extremely efficient if well written. The monolithic model tends to be more efficient through the use of shared kernel memory, rather than the slower IPC system of microkernel designs, which is typically based on
1596:, which allowed users to complete operations in stages, feeding a file through a chain of single-purpose tools. Although the end result was the same, using smaller programs in this way dramatically increased flexibility as well as ease of development and use, allowing the user to modify their workflow by adding or removing a program from the chain.
295:). The applications are not permitted by the processor to address kernel memory, thus preventing an application from damaging the running kernel. This fundamental partition of memory space has contributed much to the current designs of actual general-purpose kernels and is almost universal in such systems, although some research kernels (e.g.,
921:
servers to provide more functionality. This particular approach defines a high-level virtual interface over the hardware, with a set of system calls to implement operating system services such as process management, concurrency and memory management in several modules that run in supervisor mode. This design has several flaws and limitations:
476:. A call gate is a special address stored by the kernel in a list in kernel memory at a location known to the processor. When the processor detects a call to that address, it instead redirects to the target location without causing an access violation. This requires hardware support, but the hardware for it is quite common.
1415:, provided that the authors of those programs are willing to work without any hardware abstraction or operating system support. Most early computers operated this way during the 1950s and early 1960s, which were reset and reloaded between the execution of different programs. Eventually, small ancillary programs such as
118:. This separation prevents user data and kernel data from interfering with each other and causing instability and slowness, as well as preventing malfunctioning applications from affecting other applications or crashing the entire operating system. Even in systems where the kernel is included in application
2819:
Levy 84, p.1 quote: "Conventional architectures support a single privileged mode of operation. This structure leads to monolithic design; any module needing protection must be part of the single operating system kernel. If, instead, any module could execute within a protected domain, systems could be
981:
Microkernel (also abbreviated μK or uK) is the term describing an approach to operating system design by which the functionality of the system is moved out of the traditional "kernel", into a set of "servers" that communicate through a "minimal" kernel, leaving as little as possible in "system space"
920:
These types of kernels consist of the core functions of the operating system and the device drivers with the ability to load modules at runtime. They provide rich and powerful abstractions of the underlying hardware. They provide a small set of simple hardware abstractions and use applications called
904:
Most work in the monolithic kernel is done via system calls. These are interfaces, usually kept in a tabular structure, that access some subsystem within the kernel such as disk operations. Essentially calls are made within programs and a checked copy of the request is passed through the system call.
873:
Monolithic kernels, which have traditionally been used by Unix-like operating systems, contain all the operating system core functions and the device drivers. A monolithic kernel is one single program that contains all of the code necessary to perform every kernel-related task. Every part which is to
787:
In minimal microkernel just some very basic policies are included, and its mechanisms allows what is running on top of the kernel (the remaining part of the operating system and the other applications) to decide which policies to adopt (as memory management, high level process scheduling, file system
737:
or hardware abstraction layer. Frequently, applications will require access to these devices. The kernel must maintain the list of these devices by querying the system for them in some way. This can be done through the BIOS, or through one of the various system buses (such as PCI/PCIE, or USB). Using
561:
An alternative approach is to simulate capabilities using commonly supported hierarchical domains. In this approach, each protected object must reside in an address space that the application does not have access to; the kernel also maintains a list of capabilities in such memory. When an application
2939:
The tightly coupled nature of a monolithic kernel allows it to make very efficient use of the underlying hardware
Microkernels, on the other hand, run a lot more of the core processes in userland. Unfortunately, these benefits come at the cost of the microkernel having to pass a lot of information
1278:
Many traditionally monolithic kernels are now at least adding (or else using) the module capability. The most well known of these kernels is the Linux kernel. The modular kernel essentially can have parts of it that are built into the core kernel binary or binaries that load into memory on demand. A
1204:
architecture that leads to the design of a monolithic kernel has a significant performance drawback each time there's an interaction between different levels of protection (i.e., when a process has to manipulate a data structure both in "user mode" and "supervisor mode"), since this requires message
1173:
The performance of microkernels was poor in both the 1980s and early 1990s. However, studies that empirically measured the performance of these microkernels did not analyze the reasons of such inefficiency. The explanations of this data were left to "folklore", with the assumption that they were due
1603:
consists of two parts: first, the huge collection of utility programs that drive most operations; second, the kernel that runs the programs. Under Unix, from a programming standpoint, the distinction between the two is fairly thin; the kernel is a program, running in supervisor mode, that acts as a
1047:
basis with the microkernel. As an example, if a request for more memory is sent, a port is opened with the microkernel and the request sent through. Once within the microkernel, the steps are similar to system calls. The rationale was that it would bring modularity in the system architecture, which
1013:
Only parts which really require being in a privileged mode are in kernel space: IPC (Inter-Process
Communication), basic scheduler, or scheduling primitives, basic memory handling, basic I/O primitives. Many critical parts are now running in user space: The complete scheduler, memory handling, file
546:
Many kernels provide implementation of "capabilities", i.e., objects that are provided to user code which allow limited access to an underlying object managed by the kernel. A common example is file handling: a file is a representation of information stored on a permanent storage device. The kernel
869:
stated that "it is in opinion easier to implement a monolithic kernel". The main disadvantages of monolithic kernels are the dependencies between system components – a bug in a device driver might crash the entire system – and the fact that large kernels can become
612:
Typical computer systems today use hardware-enforced rules about what programs are allowed to access what data. The processor monitors the execution and stops a program that violates a rule, such as a user process that tries to write to kernel memory. In systems that lack support for capabilities,
1293:
Modules, generally, communicate with the kernel using a module interface of some sort. The interface is generalized (although particular to a given operating system) so it is not always possible to use modules. Often the device drivers may need more flexibility than the module interface affords.
1487:
project in 1965. Another ongoing issue was properly handling computing resources: users spent most of their time staring at the terminal and thinking about what to input instead of actually using the resources of the computer, and a time-sharing system should give the CPU time to an active user
1342:
Exokernels are a still-experimental approach to operating system design. They differ from other types of kernels in limiting their functionality to the protection and multiplexing of the raw hardware, providing no hardware abstractions on top of which to develop applications. This separation of
794:
presented arguments in favour of separation of mechanism and policy. The failure to properly fulfill this separation is one of the major causes of the lack of substantial innovation in existing operating systems, a problem common in computer architecture. The monolithic design is induced by the
1635:
posed another problem. Even if network communication can be compared to file access, the low-level packet-oriented architecture dealt with discrete chunks of data and not with whole files. As the capability of computers grew, Unix became increasingly cluttered with code. It is also because the
425:
In computing, a system call is how a process requests a service from an operating system's kernel that it does not normally have permission to run. System calls provide the interface between a process and the operating system. Most operations interacting with the system require permissions not
631:
No need for separate address spaces. Switching between address spaces is a slow operation that causes a great deal of overhead, and a lot of optimization work is currently performed in order to prevent unnecessary switches in current operating systems. Switching is completely unnecessary in a
732:
Similar to physical memory, allowing applications direct access to controller ports and registers can cause the controller to malfunction, or system to crash. With this, depending on the complexity of the device, some devices can get surprisingly complex to program, and use several different
982:
and as much as possible in "user space". A microkernel that is designed for a specific platform or device is only ever going to have what it needs to operate. The microkernel approach consists of defining a simple abstraction over the hardware, with a set of primitives or
738:
an example of a video driver, when an application requests an operation on a device, such as displaying a character, the kernel needs to send this request to the current active video driver. The video driver, in turn, needs to carry out this request. This is an example of
1526:, that have direct access to the hardware. There is no memory protection, and the kernel is almost always running in user mode. Only special actions are executed in kernel mode, and user-mode applications can ask the operating system to execute their code in kernel mode.
460:
The method of invoking the kernel function varies from kernel to kernel. If memory isolation is in use, it is impossible for a user process to call the kernel directly, because that would be a violation of the processor's access control rules. A few possibilities are:
1130:
have virtual memory support. To reduce the kernel's footprint, extensive editing has to be performed to carefully remove unneeded code, which can be very difficult with non-obvious interdependencies between parts of a kernel with millions of lines of code.
1098:
The disadvantages for microkernels are extremely context-based. As an example, they work well for small single-purpose (and critical) systems because if not many processes need to run, then the complications of process management are effectively mitigated.
1575:
were represented as a "file" at a known location – when data was copied to the file, it printed out. Other systems, to provide a similar functionality, tended to virtualize devices at a lower level – that is, both devices
635:
Flexibility. Any protection scheme that can be designed to be expressed via a programming language can be implemented using this method. Changes to the protection scheme (e.g. from a hierarchical system to a capability-based one) do not require new
822:
try to run most of their services in user space, aiming to improve maintainability and modularity of the codebase. Most kernels do not fit exactly into one of these categories, but are rather found in between these two designs. These are called
54:
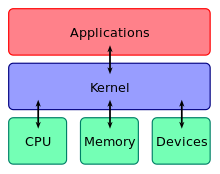
and generally has complete control over everything in the system. The kernel is also responsible for preventing and mitigating conflicts between different processes. It is the portion of the operating system code that is always resident in
375:
where the kernel will be rewritten if the available hardware changes), configured by the user (typical on older PCs and on systems that are not designed for personal use) or detected by the operating system at run time (normally called
936:
Bugs in one part of the kernel have strong side effects; since every function in the kernel has all the privileges, a bug in one function can corrupt data structure of another, totally unrelated part of the kernel, or of any running
1460:, computers had grown enormously in power – to the point where computer operators were looking for new ways to get people to use their spare time on their machines. One of the major developments during this era was
572:
An important kernel design decision is the choice of the abstraction levels where the security mechanisms and policies should be implemented. Kernel security mechanisms play a critical role in supporting security at higher levels.
367:
For example, to show the user something on the screen, an application would make a request to the kernel, which would forward the request to its display driver, which is then responsible for actually plotting the character/pixel.
190:
This central component of a computer system is responsible for executing programs. The kernel takes responsibility for deciding at any time which of the many running programs should be allocated to the processor or processors.
490:
Using a memory-based queue. An application that makes large numbers of requests but does not need to wait for the result of each may add details of requests to an area of memory that the kernel periodically scans to find
933:. Rebooting the computer is often required. This is not just a problem of convenience to the developers. When debugging is harder, and as difficulties become stronger, it becomes more likely that code will be "buggier".
1517:
was released in 1985, and was among the first – and certainly most successful – home computers to feature an advanced kernel architecture. The AmigaOS kernel's executive component,
271:
On many systems, a program's virtual address may refer to data which is not currently in memory. The layer of indirection provided by virtual addressing allows the operating system to use other data stores, like a
2185:. . . nearly all system calls invoked from C programs by calling a library procedure . . . The library procedure . . . executes a TRAP instruction to switch from user mode to kernel mode and start execution . . .
1134:
By the early 1990s, due to the various shortcomings of monolithic kernels versus microkernels, monolithic kernels were considered obsolete by virtually all operating system researchers. As a result, the design of
1814:'s kernel is considered a hybrid kernel because the kernel itself contains tasks such as the Window Manager and the IPC Managers, with a client/server layered subsystem model. It was designed as a modified
433:
instruction that causes the processor to change mode. An example would be from supervisor mode to protected mode. This is where the operating system performs actions like accessing hardware devices or the
613:
processes are isolated from each other by using separate address spaces. Calls from user processes into the kernel are regulated by requiring them to use one of the above-described system call methods.
2877:
644:
Longer application startup time. Applications must be verified when they are started to ensure they have been compiled by the correct compiler, or may need recompiling either from source code or from
1294:
Essentially, it is two system calls and often the safety checks that only have to be done once in the monolithic kernel now may be done twice. Some of the disadvantages of the modular approach are:
901:, allowing modules to be loaded into the kernel at runtime, permitting easy extension of the kernel's capabilities as required, while helping to minimize the amount of code running in kernel space.
1592:
utilities and concepts, dramatically simplifying operation. As an extension of the same paradigm, Unix allows programmers to manipulate files using a series of small programs, using the concept of
1442:
introduced the system design philosophy of a small nucleus "upon which operating systems for different purposes could be built in an orderly manner", what would be called the microkernel approach.
1106:, and the use of different operating systems on top of the same unchanged kernel. It is also possible to dynamically switch among operating systems and to have more than one active simultaneously.
218:. The kernel provides convenient methods for applications to use these devices which are typically abstracted by the kernel so that applications do not need to know their implementation details.
4209:
446:
or
Windows API. The library handles the low-level details of passing information to the kernel and switching to supervisor mode. System calls include close, open, read, wait and write.
1197:
of those concepts. Therefore it remained to be studied if the solution to build an efficient microkernel was, unlike previous attempts, to apply the correct construction techniques.
861:
In a monolithic kernel, all OS services run along with the main kernel thread, thus also residing in the same memory area. This approach provides rich and powerful hardware access.
1695:, populated by self-written hobby kernels which mostly end up sharing many features with Linux, FreeBSD, DragonflyBSD, OpenBSD or NetBSD kernels and/or being compatible with them.
2805:
Levy 84, p.1 quote: "Although the complexity of computer applications increases yearly, the underlying hardware architecture for applications has remained unchanged for decades."
697:
are sufficient primitives to express any functionality of process cooperation. However this approach is generally held to be lacking in terms of safety and efficiency, whereas a
1343:
hardware protection from hardware management enables application developers to determine how to make the most efficient use of the available hardware for each specific program.
576:
One approach is to use firmware and kernel support for fault tolerance (see above), and build the security policy for malicious behavior on top of that (adding features such as
1467:
The development of time-sharing systems led to a number of problems. One was that users, particularly at universities where the systems were being developed, seemed to want to
426:
available to a user-level process, e.g., I/O performed with a device present on the system, or any form of communication with other processes requires the use of system calls.
1022:
user sessions can be entire snapshots of the system itself or views as it is referred to. The very essence of the microkernel architecture illustrates some of its advantages:
701:
approach is more flexible. A number of other approaches (either lower- or higher-level) are available as well, with many modern kernels providing support for systems such as
659:. Such operations cannot be permitted in a language-based protection system, which means that applications may need to be rewritten and may, in some cases, lose performance.
2940:
in and out of the kernel space through a process known as a context switch. Context switches introduce considerable overhead and therefore result in a performance penalty.
449:
To actually perform useful work, a process must be able to access the services provided by the kernel. This is implemented differently by each kernel, but most provide a
565:
If the firmware does not support protection mechanisms, it is possible to simulate protection at a higher level, for example by simulating capabilities by manipulating
1048:
would entail a cleaner system, easier to debug or dynamically modify, customizable to users' needs, and more performing. They are part of the operating systems like
487:) may lack. System call instructions have been added to recent models of x86 processors, however, and some operating systems for PCs make use of them when available.
3058:
Baumann, Andrew; Barham, Paul; Dagand, Pierre-Evariste; Harris, Tim; Isaacs, Rebecca; Peter, Simon; Roscoe, Timothy; Schüpbach, Adrian; Singhania, Akhilesh (2009).
1275:) in kernel space to reduce the performance overhead of a traditional microkernel, but still running kernel code (such as device drivers) as servers in user space.
3998:
3934:
593:
The lack of many critical security mechanisms in current mainstream operating systems impedes the implementation of adequate security policies at the application
256:
The kernel has full access to the system's memory and must allow processes to safely access this memory as they require it. Often the first step in doing this is
1185:
In fact, as guessed in 1995, the reasons for the poor performance of microkernels might as well have been: (1) an actual inefficiency of the whole microkernel
2874:
3442:
717:
The idea of a kernel where I/O devices are handled uniformly with other processes, as parallel co-operating processes, was first proposed and implemented by
1464:, whereby a number of users would get small slices of computer time, at a rate at which it appeared they were each connected to their own, slower, machine.
624:. The language may then be designed such that it is impossible for the programmer to instruct it to do something that will violate a security requirement.
569:, but there are performance implications. Lack of hardware support may not be an issue, however, for systems that choose to use language-based protection.
59:
and facilitates interactions between hardware and software components. A full kernel controls all hardware resources (e.g. I/O, memory, cryptography) via
1888:, i.e. the capacity to run multiple operating systems on the same machine totally independently from each other. Hence the first such system was called
1427:. As these were developed, they formed the basis of what became early operating system kernels. The "bare metal" approach is still used today on some
597:. In fact, a common misconception in computer security is that any security policy can be implemented in an application regardless of kernel support.
106:
or other less critical parts of the operating system. The kernel performs its tasks, such as running processes, managing hardware devices such as the
2027:
The highest privilege level has various names throughout different architectures, such as supervisor mode, kernel mode, CPL0, DPL0, ring 0, etc. See
2919:
4508:
1283:
Faster development time for drivers that can operate from within modules. No reboot required for testing (provided the kernel is not destabilized).
600:
According to Mars
Research Group developers, a lack of isolation is one of the main factors undermining kernel security. They propose their driver
3272:
4225:
3174:
788:
management, etc.). A monolithic kernel instead tends to include many policies, therefore restricting the rest of the system to rely on them.
407:
or memory location. Important decisions have to be made when designing the device management system, as in some designs accesses may involve
733:
controllers. Because of this, providing a more abstract interface to manage the device is important. This interface is normally done by a
4455:
3915:
3471:
3040:
2841:
1791:, an operating system with a very similar interface, but intended for high-end and business users. This line started with the release of
3799:
2960:
943:
Even if the modules servicing these operations are separate from the whole, the code integration is tight and difficult to do correctly.
3416:
1922:(mainly the L3 and the L4 kernel) was created to demonstrate that microkernels are not necessarily slow. Newer implementations such as
763:
is the support that allows the implementation of many different policies, while a policy is a particular "mode of operation". Example:
536:); whether they are hardware supported or language based; whether they are more an open mechanism or a binding policy; and many more.
399:-specific topic, these drivers are handled differently by each kind of kernel design, but in every case, the kernel has to provide the
2478:
438:. Generally the operating system provides a library that sits between the operating system and normal user programs. Usually it is a
2326:
287:
Virtual addressing also allows creation of virtual partitions of memory in two disjointed areas, one being reserved for the kernel (
2888:
1102:
A microkernel allows the implementation of the remaining part of the operating system as a normal application program written in a
2422:
524:
The mechanisms or policies provided by the kernel can be classified according to several criteria, including: static (enforced at
2866:
2766:
Lecture Notes In
Computer Science; Vol. 563. Proceedings of the International Workshop on Operating Systems of the 90s and Beyond
2371:
Lepreau, Jay; Ford, Bryan; Hibler, Mike (1996). "The persistent relevance of the local operating system to global applications".
870:
very difficult to maintain; Thompson also stated that "It is also easier for to turn into a mess in a hurry as it is modified."
2788:
The past 25 years have shown that research on operating system architecture had a minor effect on existing main stream [
429:
A system call is a mechanism that is used by the application program to request a service from the operating system. They use a
114:. In contrast, application programs such as browsers, word processors, or audio or video players use a separate area of memory,
1969:
1768:. Because of its dependence on another operating system, initial releases of Windows, prior to Windows 95, were considered an
1220:
approach combines the speed and simpler design of a monolithic kernel with the modularity and execution safety of a microkernel
3356:
4784:
4755:
4415:
4398:
4219:
4151:
4137:
4111:
4034:
3909:
3785:
3750:
3701:
3529:
3504:
3485:
3203:
3118:
2700:
2390:
2249:
2178:
2092:
804:
514:
251:
1091:
Messaging bugs can be harder to fix due to the longer trip they have to take versus the one off copy in a monolithic kernel.
1035:
More persistence in general, if one instance goes haywire, it is often possible to substitute it with an operational mirror.
4377:
4250:
750:
The above listed tasks and features can be provided in many ways that differ from each other in design and implementation.
63:, arbitrates conflicts between processes concerning such resources, and optimizes the utilization of common resources e.g.
3327:
234:) and the protection mechanism used to mediate access to the resources within a domain. Kernels also provide methods for
584:. Approaches that delegate enforcement of security policy to the compiler and/or the application level are often called
3942:
3722:
755:
235:
2553:
Huang, Yongzhe; Narayanan, Vikram; Detweiler, David; Huang, Kaiming; Tan, Gang; Jaeger, Trent; Burtsev, Anton (2022).
1627:
could be treated as a file or a byte stream, which is printed to or read from, the same did not seem to be true for a
4970:
2781:
1918:, is the best-known general-purpose microkernel, other microkernels have been developed with more specific aims. The
1756:
1317:
529:
385:
721:(although similar ideas were suggested in 1967). In Hansen's description of this, the "common" processes are called
102:
The critical code of the kernel is usually loaded into a separate area of memory, which is protected from access by
4559:
4503:
2899:
1346:
Exokernels in themselves are extremely small. However, they are accompanied by library operating systems (see also
1298:
With more interfaces to pass through, the possibility of increased bugs exists (which implies more security holes).
3449:
3149:
2525:
2348:
Loscocco, P. A.; Smalley, S. D.; Muckelbauer, P. A.; Taylor, R. C.; Turner, S. J.; Farrell, J. F. (October 1998).
4478:
4448:
2373:
Proceedings of the 7th workshop on ACM SIGOPS European workshop
Systems support for worldwide applications - EW 7
1957:
1565:
1439:
1103:
227:
1301:
Maintaining modules can be confusing for some administrators when dealing with problems like symbol differences.
4671:
4569:
4298:
1668:
1286:
On demand capability versus spending time recompiling a whole kernel for things like new drivers or subsystems.
1071:
Other services provided by the kernel such as networking are implemented in user-space programs referred to as
672:
296:
3950:
Linden, Theodore A. (December 1976). "Operating System
Structures to Support Security and Reliable Software".
2061:
1604:
program loader and supervisor for the small utility programs making up the rest of the system, and to provide
780:
Because the mechanism and policy are separated, the policy can be easily changed to e.g. require the use of a
4949:
4498:
4483:
2530:
1927:
1148:
315:. A device driver is a computer program encapsulating, monitoring and controlling a hardware device (via its
71:
usage, file systems, and network sockets. On most systems, the kernel is one of the first programs loaded on
2205:
Swift 2005, p.29 quote: "isolation, resource control, decision verification (checking), and error recovery."
1803:
with a completely different, much more sophisticated operating system. This is the line that continues with
1289:
Faster integration of third party technology (related to development but pertinent unto itself nonetheless).
505:
An important consideration in the design of a kernel is the support it provides for protection from faults (
4544:
4529:
4488:
4129:
3059:
1651:
Modern Unix-derivatives are generally based on module-loading monolithic kernels. Examples of this are the
1402:
925:
Coding in kernel can be challenging, in part because one cannot use common libraries (like a full-featured
20:
3254:
4710:
4657:
1974:
1613:
1175:
1163:
1043:
system to handle requests from one server to another. The message passing system generally operates on a
995:
815:
800:
739:
601:
555:
292:
288:
239:
210:
I/O devices include, but are not limited to, peripherals such as keyboards, mice, disk drives, printers,
115:
111:
2349:
1316:
A nanokernel delegates virtually all services – including even the most basic ones like
1174:
to the increased frequency of switches from "kernel-mode" to "user-mode", to the increased frequency of
1006:. Microkernels are easier to maintain than monolithic kernels, but the large number of system calls and
171:
run most but not all of their services in user space, like user processes do, mainly for resilience and
4975:
4725:
4564:
4441:
4428:
1923:
1915:
1811:
1468:
1044:
404:
3291:"Windows - Official Site for Microsoft Windows 10 Home & Pro OS, laptops, PCs, tablets & more"
4760:
4539:
4534:
4493:
4049:
3632:
3298:
3243:
2927:
1732:
1692:
1029:
Patches can be tested in a separate instance, and then swapped in to take over a production instance.
3646:
2457:
1010:
might slow down the system because they typically generate more overhead than plain function calls.
483:
instruction. This technique requires special hardware support, which common architectures (notably,
4803:
4690:
4554:
4063:
3166:
1877:
1628:
1065:
439:
371:
A kernel must maintain a list of available devices. This list may be known in advance (e.g., on an
3521:
3515:
3386:
2350:"The Inevitability of Failure: The Flawed Assumption of Security in Modern Computing Environments"
966:, separate programs that assume former kernel functions, such as device drivers, GUI servers, etc.
316:
4549:
3020:
1605:
1511:
1472:
776:
Authorization server requires a password which is verified against stored passwords in a database
694:
690:
586:
411:, making the operation very CPU-intensive and easily causing a significant performance overhead.
96:
64:
4026:
4016:
3693:
3683:
2761:
1588:
the system at the file level allowed users to manipulate the entire system using their existing
4937:
4876:
4765:
4745:
4694:
4652:
4058:
4047:; Jerome H. Saltzer (March 1972). "A hardware architecture for implementing protection rings".
3641:
2452:
2015:
1843:
1581:
1115:
898:
554:(MMU) the responsibility of checking access-rights for every memory access, a mechanism called
551:
435:
184:
4268:
Gettys, James; Karlton, Philip L.; McGregor, Scott (1990). "The X window system, version 11".
4103:
4097:
3899:
3139:
3044:
2833:
550:
An efficient and simple way to provide hardware support of capabilities is to delegate to the
4720:
4686:
4588:
4524:
4022:
3952:
3765:
3544:
3477:
3007:
interactions between different levels of protection require transmission of messages by value
2762:"The Immortality of Operating Systems, or: Is Research in Operating Systems still Justified?"
2499:
2003:
1919:
1894:
1769:
1381:
1127:
991:
759:
is the substantial difference between the philosophy of micro and monolithic kernels. Here a
706:
664:
617:
532:); pre-emptive or post-detection; according to the protection principles they satisfy (e.g.,
257:
231:
3850:
3408:
2885:
1780:
series adding 32-bit addressing and pre-emptive multitasking; but ended with the release of
1636:
modularity of the Unix kernel is extensively scalable. While kernels might have had 100,000
4917:
4891:
3467:
1946:
1637:
1620:
1492:
several layers deep, and partitioning this expensive resource led to major developments in
1377:
962:
approach, the kernel itself only provides basic functionality that allows the execution of
632:
language-based protection system, as all code can safely operate in the same address space.
277:
199:
103:
31:
3806:
Härtig, Hermann; Hohmuth, Michael; Liedtke, Jochen; Schönberg, Sebastian (December 1997).
2554:
2440:
2319:
1139:
as a monolithic kernel rather than a microkernel was the topic of a famous debate between
1032:
Rapid development time and new software can be tested without having to reboot the kernel.
620:, the kernel will only allow code to execute that has been produced by a trusted language
8:
4886:
4838:
4715:
4353:
4121:
2166:
1885:
1572:
1522:, uses a microkernel message-passing design, but there are other kernel components, like
1384:. It does not assume shared memory but rather implements inter-process communications as
1359:
1144:
265:
172:
141:
134:
2237:
803:, clearly distinguishes between the two, leading naturally to a microkernel design (see
4823:
4730:
4334:
4318:
4285:
4182:
4084:
3987:
3791:
3667:
3615:
3569:
2706:
2659:
2470:
2415:
2396:
2297:
2108:
1866:
1851:
1656:
1428:
1416:
963:
926:
909:). This ability to miniaturize its kernel has also led to a rapid growth in the use of
450:
443:
3838:
2863:
2421:(Report). Vol. II. Air Force Electronic Systems Division. ESD-TR-73-51, Vol. II.
4932:
4881:
4813:
4770:
4611:
4411:
4394:
4338:
4326:
4215:
4174:
4133:
4107:
4076:
4044:
4030:
3979:
3905:
3859:
3781:
3770:
Proceedings of the sixteenth ACM symposium on
Operating systems principles - SOSP '97
3746:
3711:
3697:
3679:
3659:
3627:
3607:
3573:
3561:
3525:
3500:
3481:
3226:
2923:
2777:
2696:
2386:
2245:
2174:
2088:
1953:
1761:
1724:
1624:
1476:
1264:
1236:
1159:
1088:
More software for interfacing is required, there is a potential for performance loss.
987:
848:
811:
791:
594:
510:
473:
156:
137:
123:
68:
4289:
4088:
3991:
3772:. 16th ACM Symposium on Operating Systems Principles (SOSP'97). Saint-Malo, France.
3619:
3276:
2710:
2663:
2400:
2301:
1623:
or byte stream no longer was as universally applicable as it was before. Although a
897:
kernel, all of which fall into the category of Unix-like operating systems, support
4912:
4464:
4381:
4310:
4277:
4186:
4166:
4068:
3974:
3969:
3961:
3884:
3819:
3795:
3773:
3689:
3671:
3651:
3597:
3581:
3553:
3348:
2769:
2686:
2649:
2587:
2577:
2462:
2376:
2287:
1979:
1835:
1831:
1773:
1632:
1489:
1424:
1328:
to make the kernel memory requirement even smaller than a traditional microkernel.
1119:
1083:
999:
795:"kernel mode"/"user mode" architectural approach to protection (technically called
533:
396:
149:
51:
43:
4190:
3195:
3110:
2474:
655:. On traditional systems, applications frequently perform operations that are not
4856:
4818:
4789:
4389:
3258:
3247:
2903:
2892:
2881:
2870:
2028:
1942:
1855:
1593:
1432:
1385:
1201:
1167:
1040:
914:
796:
698:
687:
683:
558:. Most commercial computer architectures lack such MMU support for capabilities.
518:
506:
380:). In plug-and-play systems, a device manager first performs a scan on different
372:
273:
164:
107:
92:
56:
4241:
3852:
The IA-32 Architecture
Software Developer's Manual, Volume 1: Basic Architecture
1776:). This product line continued to evolve through the 1980s and 1990s, with the
1612:
services for these programs; beyond that, the kernel didn't intervene at all in
4942:
4866:
4828:
4700:
4150:; E. Cohen; W. Corwin; A. Jones; R. Levin; C. Pierson; F. Pollack (June 1974).
3930:
3761:
3319:
3170:
2678:
2264:
Silberschatz & Galvin, Operating System
Concepts, 4th ed, pp. 445 & 446
1984:
1952:, while originally created for educational purposes, is now focused on being a
1911:
1792:
1717:
1704:
1585:
1493:
1480:
1355:
1179:
1140:
1123:
1007:
894:
781:
408:
392:(USB), to detect installed devices, then searches for the appropriate drivers.
381:
215:
3026:
2952:
2526:"Automatic device driver isolation protects against bugs in operating systems"
1388:. Barrelfish was the first operating system to be described as a multikernel.
4964:
4851:
4808:
4647:
4601:
4330:
4322:
4301:(February 2005). "Improving the reliability of commodity operating systems".
4296:
4178:
4080:
3983:
3740:
3663:
3611:
3565:
3539:
1907:
1873:. In other operating systems, the supervisor is generally called the kernel.
1819:
1744:
1727:. Apple moved to a nanokernel design in Mac OS 8.6. Against this, the modern
1676:
1325:
1268:
1256:
1230:
1217:
1206:
947:
824:
734:
718:
702:
377:
312:
281:
261:
160:
119:
60:
4314:
3715:
3466:
1435:, but in general, newer computers use modern operating systems and kernels.
4735:
4281:
4147:
3889:
3872:
3868:
3843:
Proceedings of the 8th ACM International Symposium on Computer Architecture
3834:
2466:
1847:
1652:
1641:
1609:
1589:
1461:
1451:
1412:
1136:
998:. Other services, including those normally provided by the kernel, such as
930:
878:
866:
577:
539:
Support for hierarchical protection domains is typically implemented using
525:
430:
400:
180:
84:
4170:
4072:
3965:
3824:
3807:
3777:
3655:
3602:
3585:
3557:
2691:
2683:
Proceedings of the ACM symposium on Operating System Principles - SOSP '67
2654:
2637:
2591:
2381:
2292:
2275:
469:. This method is available on most hardware, and is therefore very common.
4861:
4843:
4626:
4616:
4606:
1815:
1561:
1557:
1371:
1114:
As the computer kernel grows, so grows the size and vulnerability of its
983:
976:
959:
819:
656:
652:
480:
420:
168:
145:
4408:
Computer Organisation and Architecture: An Introduction (Second edition)
2896:
2862:
Recordings of the debate between Torvalds and Tanenbaum can be found at
2578:
Jonathan S. Shapiro; Jonathan M. Smith; David J. Farber (1999). "EROS".
2354:
Proceedings of the 21st National Information Systems Security Conference
1118:; and, besides reducing security, there is the problem of enlarging the
126:
is used to prevent unauthorized applications from modifying the kernel.
3999:"Operating System Structures to Support Security and Reliable Software"
3742:
Classic operating systems: from batch processing to distributed systems
3739:
Per Brinch Hansen, ed. (2001). "1 The evolution of operating systems".
3143:
2773:
2082:
1881:
1839:
1804:
1800:
1796:
1788:
1781:
1777:
1713:
1691:. Apart from these alternatives, amateur developers maintain an active
1411:
to run a computer. Programs can be directly loaded and executed on the
1311:
1272:
1240:
828:
566:
360:
339:
Simulating work with hardware, while doing something entirely different
308:
80:
76:
1540:
322:
At the hardware level, common abstractions of device drivers include:
311:
connected to the computer, which are controlled by the kernel through
4798:
4705:
4631:
4596:
3061:
The Multikernel: a new OS architecture for scalable multicore systems
2820:
built as a collection of independent modules extensible by any user."
1721:
1545:
1347:
1337:
1235:
Hybrid kernels are used in most commercial operating systems such as
954:
832:
668:
540:
466:
4433:
1619:
Over the years the computing model changed, and Unix's treatment of
1239:
NT 3.1, NT 3.5, NT 3.51, NT 4.0, 2000, XP, Vista, 7, 8, 8.1 and 10.
513:). These two aspects are usually not clearly distinguished, and the
4927:
2053:
1420:
1407:
Strictly speaking, an operating system (and thus, a kernel) is not
1049:
1019:
645:
621:
581:
580:
mechanisms where necessary), delegating some responsibility to the
336:
Using a lower-level device driver (file drivers using disk drivers)
88:
47:
3251:
1162:
are designed to have all of their code in the same address space (
616:
An alternative approach is to use language-based protection. In a
4922:
4621:
4429:
Detailed comparison between most popular operating system kernels
2438:
2357:
1795:
in 1993, and was introduced to general users with the release of
1680:
1672:
1664:
1505:
1484:
1260:
1057:
906:
886:
882:
403:
to allow drivers to physically access their devices through some
347:
Allowing the operating system direct access to hardware resources
176:
72:
2347:
2014:
Virtual addressing is most commonly achieved through a built-in
1212:
1147:. There is merit on both sides of the argument presented in the
853:
26:
19:"Kernel (computer science)" redirects here. For other uses, see
1870:
1765:
1684:
1544:
A diagram of the predecessor/successor family relationship for
1488:
during these periods. Finally, the systems typically offered a
835:
are available, but are seldom used for production systems. The
343:
And at the software level, device driver abstractions include:
276:, to store what would otherwise have to remain in main memory (
183:
is both monolithic and modular, since it can insert and remove
4239:
3939:
Proc. 15th ACM Symposium on Operating System Principles (SOSP)
1740:
4871:
4146:
3805:
3759:
2222:
2220:
1949:
1931:
1822:
but does not meet all of the criteria of a pure microkernel.
1728:
1708:
1688:
1514:
1321:
1252:
1244:
1053:
929:), and because one needs to use a source-level debugger like
910:
890:
359:
Implementing a language (often a high-level language such as
354:
4358:
Operating Systems: Design and Implementation (Third edition)
4207:
2552:
1854:, and similar functions and regulates the flow of work in a
1553:
1535:
1457:
1380:
machine as a network of independent cores, as if it were a
862:
663:
Examples of systems with language-based protection include
330:
4043:
3764:; Schönberg, Sebastian; Wolter, Jean (October 5–8, 1997).
3630:(April 1970). "The nucleus of a Multiprogramming System".
2217:
1193:
implemented in those microkernels, and (3) the particular
1078:
Disadvantages in the microkernel exist however. Some are:
940:
Kernels often become very large and difficult to maintain.
353:
Implementing an interface for non-driver software such as
307:
To perform useful functions, processes need access to the
4907:
3240:
3078:
3057:
2790:
1938:
1862:
1736:
1660:
1645:
1351:
1248:
1061:
1015:
1002:, are implemented in user-space programs, referred to as
836:
770:
User login attempts are routed to an authorization server
607:
604:
framework for protection, primarily in the Linux kernel.
484:
454:
389:
211:
130:
4243:
Improving the reliability of commodity operating systems
4152:"HYDRA: the kernel of a multiprocessor operating system"
2828:
2826:
1861:
Historically, this term was essentially associated with
3866:
3839:"IBM System/38 support for capability-based addressing"
3378:
2815:
2813:
2811:
1934:
next to other L4 processes in separate address spaces.
3290:
2999:
2834:"Open Sources: Voices from the Open Source Revolution"
2608:. Math. Dep., Technological U., Eindhoven, Sept. 1965.
2439:
Jerry H. Saltzer; Mike D. Schroeder (September 1975).
2318:
Schneider, Fred B.; Morrissett, Greg; Harper, Robert.
1109:
1094:
Process management in general can be very complicated.
457:, which in turn invokes the related kernel functions.
4267:
3542:(December 1976). "Fault tolerant operating systems".
2823:
2679:"Dynamic Supervisors - their design and construction"
2317:
1122:. This is mitigated to some degree by perfecting the
814:
execute all of their code in the same address space (
144:
requests a service from the kernel, it must invoke a
79:). It handles the rest of startup as well as memory,
4240:
Swift, Michael M.; Brian N. Bershad; Henry M. Levy.
3520:(revisited first ed.). Addison-Wesley. p.
2808:
2276:"An implementation of capabilities on the PDP-11/45"
1876:
In the 1970s, IBM further abstracted the supervisor
3832:
3497:
Embedded Microprocessor Systems: Real World Designs
2441:"The protection of information in computer systems"
4309:(1). Association for Computing Machinery: 77–110.
4211:Architettura dei Sistemi di Elaborazione, volume 1
3710:
3738:
3538:
3067:. 22nd Symposium on Operating Systems Principles.
2913:
2911:
2856:
2370:
1818:, as the Windows NT kernel was influenced by the
1445:
1423:were left in memory between runs, or loaded from
1396:
517:in the kernel design leads to the rejection of a
155:There are different kernel architecture designs.
4962:
4386:Computer Organization and Design (Sixth edition)
3376:
3261:and other operating system enthusiast web sites.
2638:"SHARER, a time sharing system for the CDC 6600"
2635:
2273:
2235:
2229:
2199:
1556:, programmers decided to model every high-level
1391:
745:
179:is a notable example of microkernel design. The
3867:Levin, R.; Cohen, E.; Corwin, W.; Pollack, F.;
3586:"Why not innovations in computer architecture?"
3145:Introduction and Overview of the Multics System
2953:"Operating Systems/Kernel Models - Wikiversity"
2676:
2173:(3rd ed.). Prentice Hall. pp. 50–51.
30:An oversimplification of how a kernel connects
4372:Understanding the Linux Kernel (Third edition)
3897:
3094:
2908:
2083:Randal E. Bryant; David R. O'Hallaron (2016).
1941:is a microkernel which is principally used in
1901:
1224:
4449:
4208:Baiardi, F.; A. Tomasi; M. Vanneschi (1988).
3470:; James L. Peterson; Peter B. Galvin (1991).
3091:Ball: Embedded Microprocessor Designs, p. 129
2920:"What Is Darwin (and How It Powers Mac OS X)"
2343:
2341:
2339:
2242:IA-64 Linux Kernel: Design and Implementation
2152:
2150:
110:, and handling interrupts, in this protected
3745:. New York: Springer-Verlag. pp. 1–36.
3138:
2983:
2981:
2979:
2977:
2555:"KSplit: Automating Device Driver Isolation"
2313:
2311:
2236:Eranian, Stephane; Mosberger, David (2002).
2118:
2116:
2085:Computer Systems: A Programmer's Perspective
1640:in the seventies and eighties, kernels like
3808:"The performance of μ-kernel-based systems"
3766:"The performance of μ-kernel-based systems"
3377:Zoller (inaktiv), Heinz (7 December 2013).
2917:
2677:Huxtable, D. H. R.; Warwick, M. T. (1967).
2622:
2620:
2618:
2616:
2614:
2416:Computer Security Technology Planning Study
2208:
1764:was first released in 1985 as an add-on to
1698:
4456:
4442:
2737:
2735:
2598:
2336:
2267:
2238:"Virtual Memory in the IA-64 Linux Kernel"
2147:
839:hypervisor, for example, is an exokernel.
693:and unlock operations operating on binary
686:proved that from a logical point of view,
495:
4365:Modern Operating Systems (Fourth edition)
4120:
4062:
3973:
3888:
3823:
3645:
3601:
2974:
2744:
2690:
2653:
2636:Harrison, M. C.; Schwartz, J. T. (1967).
2456:
2380:
2308:
2291:
2274:Hoch, Charles; J. C. Browne (July 1980).
2165:
2113:
986:to implement minimal OS services such as
950:, a bug can bring down the entire system.
3085:
3022:WWDC 2000 Session 106 – Mac OS X: Kernel
2990:
2753:
2611:
2413:
2190:
2140:
2138:
2136:
2134:
2132:
2130:
2128:
1731:(originally named Mac OS X) is based on
1539:
1376:A multikernel operating system treats a
1211:
953:
852:
712:
25:
21:Kernel (disambiguation) § Computing
4099:The logical design of Operating systems
3929:
3580:
3224:
3161:
3159:
3148:. 1965 Fall Joint Computer Conference.
2732:
2320:"A Language-Based Approach to Security"
2087:(Third ed.). Pearson. p. 17.
2048:
2046:
1838:, that controls the execution of other
1830:Supervisory program or supervisor is a
1560:, because they believed the purpose of
877:Modern monolithic kernels, such as the
205:
194:
4963:
3949:
3873:"Policy/Mechanism separation in Hydra"
3678:
3626:
3590:ACM SIGARCH Computer Architecture News
3513:
3320:"The L4 microkernel family - Overview"
3225:Wheeler, David A. (October 12, 2004).
2759:
1970:Comparison of operating system kernels
1693:operating system development community
678:
608:Hardware- or language-based protection
291:) and the other for the applications (
221:
4463:
4437:
4014:
3270:
2125:
1739:, which was created by combining the
842:
805:Separation of protection and security
627:Advantages of this approach include:
519:hierarchical structure for protection
252:Memory management (operating systems)
4406:B.S. Chalk, A.T. Carter, R.W. Hind,
4303:ACM Transactions on Computer Systems
4297:Michael M. Swift; Brian N. Bershad;
4095:
3716:"The evolution of operating systems"
3517:An introduction to operating systems
3499:(first ed.). Elsevier Science.
3494:
3440:
3227:"Linux Kernel 2.6: It's Worth More!"
3206:from the original on 9 November 2010
3156:
2844:from the original on 1 February 2020
2064:from the original on 8 December 2006
2043:
1750:
1735:, which uses a hybrid kernel called
329:Using a high-level interface (Video
302:
245:
3877:ACM Sigops Operating Systems Review
3812:ACM SIGOPS Operating Systems Review
3760:Härtig, Hermann; Hohmuth, Michael;
3443:"Monolithic kernel vs. Microkernel"
3349:"The Fiasco microkernel - Overview"
2580:ACM Sigops Operating Systems Review
2280:ACM SIGOPS Operating Systems Review
1648:, have more than 13 million lines.
1110:Monolithic kernels vs. microkernels
725:, while the I/O devices are called
230:are defining the execution domain (
16:Core of a computer operating system
13:
4363:Andrew S. Tanenbaum, Herbert Bos,
4347:
3389:from the original on 19 April 2001
3312:
3111:"BSTJ version of C.ACM Unix paper"
2523:
2356:. pp. 303–314. Archived from
1880:from the hardware, resulting in a
1178:and to the increased frequency of
946:Since the modules run in the same
756:separation of mechanism and policy
14:
4987:
4422:
4270:Software: Practice and Experience
3901:Capability-based computer systems
3239:This community mostly gathers at
3079:"The Barrelfish operating system"
3018:
1825:
1757:Microsoft Windows version history
1644:, of modern Unix successors like
1580:files would be instances of some
1354:, for example one for high level
509:) and from malicious behaviours (
386:Peripheral Component Interconnect
317:Hardware/Software Interface (HSI)
4560:Object-oriented operating system
4126:Structured Computer Organization
3904:. Maynard, Mass: Digital Press.
3802:from the original on 2020-02-17.
3152:from the original on 2011-07-09.
3041:"KeyKOS Nanokernel Architecture"
3025:. 14 minutes in. Archived from
2606:Cooperating Sequential Processes
2428:from the original on 2011-07-21.
2332:from the original on 2018-12-22.
1869:operating systems starting with
1251:, which is based upon code from
618:language-based protection system
4370:Daniel P. Bovet, Marco Cesati,
4256:from the original on 2007-07-19
3918:from the original on 2007-07-13
3728:from the original on 2011-07-25
3480:: Addison-Wesley. p. 696.
3419:from the original on 2019-03-24
3401:
3370:
3359:from the original on 2006-06-16
3341:
3330:from the original on 2006-08-21
3301:from the original on 2011-08-20
3283:
3264:
3233:
3218:
3188:
3177:from the original on 2016-10-04
3167:"The Single Unix Specification"
3132:
3121:from the original on 2005-12-30
3103:
3071:
3051:
3033:
3012:
2963:from the original on 2014-12-18
2945:
2799:
2723:
2670:
2629:
2571:
2546:
2517:
2500:"Fine-grained kernel isolation"
2492:
2481:from the original on 2021-03-08
2432:
2407:
2364:
2258:
2021:
2008:
1440:RC 4000 Multiprogramming System
1365:
1202:hierarchical protection domains
970:
797:hierarchical protection domains
414:
395:As device management is a very
214:devices, network adapters, and
4570:Supercomputer operating system
3005:Hansen 73, section 7.3 p.233 "
2159:
2101:
2076:
2060:. Bellevue Linux Users Group.
1996:
1669:Berkeley Software Distribution
1446:Time-sharing operating systems
1397:Early operating system kernels
1305:
1154:
857:Diagram of a monolithic kernel
827:. More exotic designs such as
1:
4214:(in Italian). Franco Angeli.
3845:. ACM/IEEE. pp. 341–348.
3271:Singh, Amit (December 2003).
2531:Pennsylvania State University
2414:Anderson, J. (October 1972).
2037:
1392:History of kernel development
1331:
746:Kernel-wide design approaches
500:
34:to the hardware of a computer
4545:Just enough operating system
4530:Distributed operating system
4130:Englewood Cliffs, New Jersey
3252:The Mega-Tokyo Message Board
1772:(not to be confused with an
1483:became a major focus of the
1403:History of operating systems
1247:uses a hybrid kernel called
515:adoption of this distinction
350:Only implementing primitives
7:
4658:User space and kernel space
4025:: Addison-Wesley. pp.
3685:Operating System Principles
3514:Deitel, Harvey M. (1984) .
2626:Brinch Hansen 70 pp.238–241
1975:Inter-process communication
1963:
1902:Development of microkernels
1552:During the design phase of
1225:Hybrid (or modular) kernels
1176:inter-process communication
996:inter-process communication
801:capability-based addressing
740:inter-process communication
556:capability-based addressing
465:Using a software-simulated
240:inter-process communication
10:
4992:
4565:Real-time operating system
3935:"On µ-Kernel Construction"
3433:
3100:Hansen 2001 (os), pp.17–18
2897:Andrew Tanenbaum's website
1916:Carnegie Mellon University
1812:architecture of Windows NT
1799:in October 2001—replacing
1754:
1720:in 1984, bundled with its
1702:
1533:
1503:
1449:
1400:
1369:
1335:
1309:
1228:
974:
846:
528:) or dynamic (enforced at
418:
249:
163:with the CPU executing in
18:
4900:
4837:
4783:
4761:Multilevel feedback queue
4756:Fixed-priority preemptive
4744:
4679:
4670:
4640:
4587:
4578:
4540:Hobbyist operating system
4535:Embedded operating system
4517:
4471:
4159:Communications of the ACM
4102:. Prentice-Hall. p.
4050:Communications of the ACM
3837:; Hoffman, R. L. (1981).
3692:: Prentice Hall. p.
3633:Communications of the ACM
3495:Ball, Stuart R. (2002) .
3473:Operating system concepts
2642:Communications of the ACM
1787:Microsoft also developed
1149:Tanenbaum–Torvalds debate
299:) take other approaches.
226:Key aspects necessary in
159:run entirely in a single
4971:Operating system kernels
4804:General protection fault
4555:Network operating system
4509:User features comparison
3241:Bona Fide OS Development
2171:Modern Operating Systems
1990:
1699:Classic Mac OS and macOS
1671:variant kernels such as
1629:graphical user interface
1499:
1456:In the decade preceding
1358:development and one for
1039:Most microkernels use a
91:, translating them into
4550:Mobile operating system
4315:10.1145/1047915.1047919
3975:2027/mdp.39015086560037
3898:Levy, Henry M. (1984).
3441:Roch, Benjamin (2004).
3409:"QNX Operating Systems"
2760:Nehmer, Jürgen (1991).
2685:. pp. 11.1–11.17.
2504:mars-research.github.io
2445:Proceedings of the IEEE
1599:In the Unix model, the
1529:
1475:time. For this reason,
1471:the system to get more
899:loadable kernel modules
640:Disadvantages include:
587:language-based security
496:Kernel design decisions
185:loadable kernel modules
97:central processing unit
4653:Loadable kernel module
4410:, Palgrave Macmillan (
4356:, Albert S. Woodhull,
4282:10.1002/spe.4380201404
4096:Shaw, Alan C. (1974).
4015:Lorin, Harold (1981).
3890:10.1145/1067629.806531
2467:10.1109/PROC.1975.9939
2016:memory management unit
1549:
1324: – to
1221:
1200:On the other end, the
1128:computer architectures
1116:trusted computing base
967:
858:
707:remote procedure calls
552:memory management unit
436:memory management unit
260:, usually achieved by
35:
4721:Process control block
4687:Computer multitasking
4525:Disk operating system
4171:10.1145/355616.364017
4073:10.1145/361268.361275
4045:Schroeder, Michael D.
4023:Boston, Massachusetts
3966:10.1145/356678.356682
3953:ACM Computing Surveys
3825:10.1145/269005.266660
3778:10.1145/268998.266660
3656:10.1145/362258.362278
3603:10.1145/859504.859506
3558:10.1145/356678.356680
3545:ACM Computing Surveys
3478:Boston, Massachusetts
3468:Silberschatz, Abraham
3379:"L4Ka - L4Ka Project"
3202:. 29 September 2010.
2692:10.1145/800001.811675
2655:10.1145/363717.363778
2592:10.1145/319344.319163
2382:10.1145/504450.504477
2293:10.1145/850697.850701
2244:. Prentice Hall PTR.
2031:for more information.
2004:Computer architecture
2002:It may depend on the
1920:L4 microkernel family
1834:, usually part of an
1770:operating environment
1543:
1318:interrupt controllers
1215:
1189:, (2) the particular
957:
856:
713:I/O device management
250:Further information:
95:instructions for the
29:
4892:Virtual tape library
4484:Forensic engineering
4122:Tanenbaum, Andrew S.
3353:os.inf.tu-dresden.de
3324:os.inf.tu-dresden.de
2375:. pp. 133–140.
2167:Tanenbaum, Andrew S.
2144:Wulf 1974 pp.337–345
1947:open-source software
1621:everything as a file
1413:"bare metal" machine
1126:system, but not all
390:Universal Serial Bus
326:Interfacing directly
206:Input/output devices
200:Random-access memory
195:Random-access memory
167:, mainly for speed.
148:, usually through a
104:application software
87:(I/O) requests from
32:application software
4901:Supporting concepts
4887:Virtual file system
4354:Andrew S. Tanenbaum
3142:; Vissotsky, V. A.
1886:full virtualization
1716:first launched its
1566:data transformation
1429:video game consoles
1104:high-level language
679:Process cooperation
228:resource management
222:Resource management
4824:Segmentation fault
4672:Process management
4378:David A. Patterson
3737:included in book:
3712:Hansen, Per Brinch
3680:Hansen, Per Brinch
3628:Hansen, Per Brinch
3413:blackberry.qnx.com
3257:2022-01-25 at the
3246:2022-01-17 at the
2957:en.wikiversity.org
2902:2015-08-05 at the
2891:2014-09-21 at the
2880:2013-05-26 at the
2869:2012-10-03 at the
2774:10.1007/BFb0024528
2768:. pp. 77–83.
2533:via techxplore.com
2109:Daemon (computing)
1550:
1382:distributed system
1222:
1160:Monolithic kernels
1026:Easier to maintain
968:
859:
843:Monolithic kernels
812:monolithic kernels
727:external processes
723:internal processes
258:virtual addressing
157:Monolithic kernels
36:
4976:Operating systems
4958:
4957:
4814:Memory protection
4785:Memory management
4779:
4778:
4771:Shortest job next
4666:
4665:
4465:Operating systems
4416:978-1-4039-0164-4
4402:
4399:978-0-12-820109-1
4221:978-88-204-2746-7
4139:978-0-13-148521-1
4132:: Prentice-Hall.
4113:978-0-13-540112-5
4036:978-0-201-14464-2
4018:Operating systems
3933:(December 1995).
3911:978-0-932376-22-0
3860:Intel Corporation
3787:978-0-89791-916-6
3752:978-0-387-95113-3
3703:978-0-13-637843-3
3582:Denning, Peter J.
3540:Denning, Peter J.
3531:978-0-201-14502-1
3506:978-0-7506-7534-5
3487:978-0-201-51379-0
3273:"XNU: The Kernel"
2918:Matthew Russell.
2875:groups.google.com
2840:. 29 March 1999.
2702:978-1-4503-7370-8
2392:978-1-4503-7339-5
2251:978-0-13-061014-0
2180:978-0-13-600663-3
2156:Silberschatz 1991
2094:978-0-13-409266-9
1762:Microsoft Windows
1751:Microsoft Windows
1725:personal computer
1667:, as well as the
1265:monolithic kernel
1237:Microsoft Windows
988:memory management
849:Monolithic kernel
792:Per Brinch Hansen
753:The principle of
595:abstraction level
303:Device management
246:Memory management
138:abstraction layer
124:memory protection
46:at the core of a
4983:
4913:Computer network
4677:
4676:
4585:
4584:
4458:
4451:
4444:
4435:
4434:
4392:
4382:John L. Hennessy
4342:
4293:
4264:
4262:
4261:
4255:
4248:
4236:
4234:
4233:
4224:. Archived from
4204:
4202:
4201:
4195:
4189:. Archived from
4156:
4143:
4117:
4092:
4066:
4040:
4011:
4009:
4008:
4003:
3995:
3977:
3946:
3941:. Archived from
3926:
3924:
3923:
3894:
3892:
3863:
3857:
3846:
3829:
3827:
3803:
3756:
3736:
3734:
3733:
3727:
3720:
3707:
3690:Englewood Cliffs
3675:
3649:
3623:
3605:
3577:
3535:
3510:
3491:
3463:
3461:
3460:
3454:
3448:. Archived from
3447:
3428:
3427:
3425:
3424:
3405:
3399:
3398:
3396:
3394:
3374:
3368:
3367:
3365:
3364:
3345:
3339:
3338:
3336:
3335:
3316:
3310:
3309:
3307:
3306:
3287:
3281:
3280:
3275:. Archived from
3268:
3262:
3237:
3231:
3230:
3222:
3216:
3215:
3213:
3211:
3196:"Unix's Revenge"
3192:
3186:
3185:
3183:
3182:
3163:
3154:
3153:
3136:
3130:
3129:
3127:
3126:
3107:
3101:
3098:
3092:
3089:
3083:
3082:
3075:
3069:
3068:
3066:
3055:
3049:
3048:
3043:. Archived from
3037:
3031:
3030:
3016:
3010:
3003:
2997:
2994:
2988:
2985:
2972:
2971:
2969:
2968:
2949:
2943:
2942:
2936:
2935:
2926:. Archived from
2915:
2906:
2860:
2854:
2853:
2851:
2849:
2830:
2821:
2817:
2806:
2803:
2797:
2796:
2757:
2751:
2748:
2742:
2739:
2730:
2727:
2721:
2720:
2718:
2717:
2694:
2674:
2668:
2667:
2657:
2633:
2627:
2624:
2609:
2604:Dijkstra, E. W.
2602:
2596:
2595:
2575:
2569:
2568:
2566:
2564:
2559:
2550:
2544:
2543:
2541:
2539:
2521:
2515:
2514:
2512:
2510:
2496:
2490:
2489:
2487:
2486:
2460:
2451:(9): 1278–1308.
2436:
2430:
2429:
2427:
2420:
2411:
2405:
2404:
2384:
2368:
2362:
2361:
2345:
2334:
2333:
2331:
2324:
2315:
2306:
2305:
2295:
2271:
2265:
2262:
2256:
2255:
2233:
2227:
2224:
2215:
2212:
2206:
2203:
2197:
2194:
2188:
2187:
2163:
2157:
2154:
2145:
2142:
2123:
2120:
2111:
2105:
2099:
2098:
2080:
2074:
2073:
2071:
2069:
2050:
2032:
2025:
2019:
2012:
2006:
2000:
1980:Operating system
1960:microkernel OS.
1943:embedded systems
1930:are able to run
1836:operating system
1832:computer program
1820:Mach microkernel
1774:operating system
1601:operating system
1558:device as a file
1524:graphics.library
1490:memory hierarchy
1433:embedded systems
1259:(OSFMK 7.3) and
1180:context switches
1145:Andrew Tanenbaum
1120:memory footprint
1084:memory footprint
1008:context switches
915:embedded systems
893:kernel, and the
479:Using a special
409:context switches
382:peripheral buses
150:wrapper function
52:operating system
44:computer program
4991:
4990:
4986:
4985:
4984:
4982:
4981:
4980:
4961:
4960:
4959:
4954:
4896:
4857:Defragmentation
4842:
4833:
4819:Protection ring
4788:
4775:
4747:
4740:
4662:
4636:
4574:
4513:
4467:
4462:
4425:
4390:Morgan Kaufmann
4350:
4348:Further reading
4345:
4259:
4257:
4253:
4246:
4231:
4229:
4222:
4199:
4197:
4193:
4154:
4140:
4114:
4037:
4006:
4004:
4001:
3997:
3931:Liedtke, Jochen
3921:
3919:
3912:
3855:
3849:
3833:Houdek, M. E.;
3788:
3762:Liedtke, Jochen
3753:
3731:
3729:
3725:
3718:
3704:
3647:10.1.1.105.4204
3532:
3507:
3488:
3458:
3456:
3452:
3445:
3436:
3431:
3422:
3420:
3407:
3406:
3402:
3392:
3390:
3375:
3371:
3362:
3360:
3347:
3346:
3342:
3333:
3331:
3318:
3317:
3313:
3304:
3302:
3289:
3288:
3284:
3269:
3265:
3259:Wayback Machine
3248:Wayback Machine
3238:
3234:
3223:
3219:
3209:
3207:
3194:
3193:
3189:
3180:
3178:
3165:
3164:
3157:
3137:
3133:
3124:
3122:
3109:
3108:
3104:
3099:
3095:
3090:
3086:
3077:
3076:
3072:
3064:
3056:
3052:
3039:
3038:
3034:
3017:
3013:
3004:
3000:
2995:
2991:
2986:
2975:
2966:
2964:
2951:
2950:
2946:
2933:
2931:
2916:
2909:
2904:Wayback Machine
2893:Wayback Machine
2882:Wayback Machine
2871:Wayback Machine
2861:
2857:
2847:
2845:
2832:
2831:
2824:
2818:
2809:
2804:
2800:
2784:
2758:
2754:
2749:
2745:
2740:
2733:
2728:
2724:
2715:
2713:
2703:
2675:
2671:
2648:(10): 659–665.
2634:
2630:
2625:
2612:
2603:
2599:
2576:
2572:
2562:
2560:
2557:
2551:
2547:
2537:
2535:
2522:
2518:
2508:
2506:
2498:
2497:
2493:
2484:
2482:
2458:10.1.1.126.9257
2437:
2433:
2425:
2418:
2412:
2408:
2393:
2369:
2365:
2346:
2337:
2329:
2322:
2316:
2309:
2272:
2268:
2263:
2259:
2252:
2234:
2230:
2225:
2218:
2213:
2209:
2204:
2200:
2195:
2191:
2181:
2164:
2160:
2155:
2148:
2143:
2126:
2121:
2114:
2106:
2102:
2095:
2081:
2077:
2067:
2065:
2052:
2051:
2044:
2040:
2035:
2029:Protection ring
2026:
2022:
2013:
2009:
2001:
1997:
1993:
1966:
1954:highly reliable
1910:, developed by
1904:
1890:Virtual Machine
1856:data processing
1844:work scheduling
1828:
1759:
1753:
1743:kernel and the
1711:
1703:Main articles:
1701:
1590:file management
1538:
1532:
1508:
1502:
1454:
1448:
1417:program loaders
1405:
1399:
1394:
1386:message passing
1374:
1368:
1340:
1334:
1314:
1308:
1233:
1227:
1168:message passing
1157:
1112:
1082:Larger running
1041:message passing
979:
973:
851:
845:
748:
715:
699:message passing
684:Edsger Dijkstra
681:
610:
507:fault tolerance
503:
498:
423:
417:
373:embedded system
305:
254:
248:
236:synchronization
224:
216:display devices
208:
197:
165:supervisor mode
93:data-processing
24:
17:
12:
11:
5:
4989:
4979:
4978:
4973:
4956:
4955:
4953:
4952:
4947:
4946:
4945:
4943:User interface
4940:
4930:
4925:
4920:
4915:
4910:
4904:
4902:
4898:
4897:
4895:
4894:
4889:
4884:
4879:
4874:
4869:
4867:File attribute
4864:
4859:
4854:
4848:
4846:
4835:
4834:
4832:
4831:
4829:Virtual memory
4826:
4821:
4816:
4811:
4806:
4801:
4795:
4793:
4781:
4780:
4777:
4776:
4774:
4773:
4768:
4763:
4758:
4752:
4750:
4742:
4741:
4739:
4738:
4733:
4728:
4723:
4718:
4713:
4708:
4703:
4701:Context switch
4698:
4683:
4681:
4674:
4668:
4667:
4664:
4663:
4661:
4660:
4655:
4650:
4644:
4642:
4638:
4637:
4635:
4634:
4629:
4624:
4619:
4614:
4609:
4604:
4599:
4593:
4591:
4582:
4576:
4575:
4573:
4572:
4567:
4562:
4557:
4552:
4547:
4542:
4537:
4532:
4527:
4521:
4519:
4515:
4514:
4512:
4511:
4506:
4501:
4496:
4491:
4486:
4481:
4475:
4473:
4469:
4468:
4461:
4460:
4453:
4446:
4438:
4432:
4431:
4424:
4423:External links
4421:
4420:
4419:
4404:
4375:
4368:
4361:
4349:
4346:
4344:
4343:
4294:
4265:
4237:
4220:
4205:
4165:(6): 337–345.
4144:
4138:
4118:
4112:
4093:
4064:10.1.1.83.8304
4057:(3): 157–170.
4041:
4035:
4012:
3960:(4): 409–445.
3947:
3945:on 2007-03-13.
3927:
3910:
3895:
3883:(5): 132–140.
3864:
3847:
3830:
3786:
3757:
3751:
3708:
3702:
3676:
3640:(4): 238–241.
3624:
3584:(April 1980).
3578:
3552:(4): 359–389.
3536:
3530:
3511:
3505:
3492:
3486:
3464:
3437:
3435:
3432:
3430:
3429:
3400:
3369:
3340:
3311:
3282:
3279:on 2011-08-12.
3263:
3232:
3217:
3187:
3171:The Open Group
3155:
3140:Corbató, F. J.
3131:
3102:
3093:
3084:
3070:
3050:
3047:on 2011-06-21.
3032:
3029:on 2021-10-30.
3011:
2998:
2989:
2973:
2944:
2924:O'Reilly Media
2907:
2855:
2822:
2807:
2798:
2794:] systems.
2782:
2752:
2743:
2731:
2722:
2701:
2669:
2628:
2610:
2597:
2586:(5): 170–185.
2570:
2545:
2524:Fetzer, Mary.
2516:
2491:
2431:
2406:
2391:
2363:
2360:on 2007-06-21.
2335:
2307:
2266:
2257:
2250:
2228:
2216:
2207:
2198:
2189:
2179:
2158:
2146:
2124:
2112:
2100:
2093:
2075:
2041:
2039:
2036:
2034:
2033:
2020:
2007:
1994:
1992:
1989:
1988:
1987:
1985:Virtual memory
1982:
1977:
1972:
1965:
1962:
1937:Additionally,
1912:Richard Rashid
1903:
1900:
1842:and regulates
1827:
1826:IBM Supervisor
1824:
1793:Windows NT 3.1
1755:Main article:
1752:
1749:
1718:classic Mac OS
1705:Classic Mac OS
1700:
1697:
1571:For instance,
1534:Main article:
1531:
1528:
1504:Main article:
1501:
1498:
1494:virtual memory
1481:access control
1450:Main article:
1447:
1444:
1401:Main article:
1398:
1395:
1393:
1390:
1370:Main article:
1367:
1364:
1336:Main article:
1333:
1330:
1326:device drivers
1310:Main article:
1307:
1304:
1303:
1302:
1299:
1291:
1290:
1287:
1284:
1229:Main article:
1226:
1223:
1195:implementation
1156:
1153:
1141:Linus Torvalds
1124:virtual memory
1111:
1108:
1096:
1095:
1092:
1089:
1086:
1037:
1036:
1033:
1030:
1027:
975:Main article:
972:
969:
952:
951:
944:
941:
938:
934:
847:Main article:
844:
841:
825:hybrid kernels
782:security token
778:
777:
771:
747:
744:
714:
711:
680:
677:
661:
660:
649:
638:
637:
633:
609:
606:
502:
499:
497:
494:
493:
492:
488:
477:
470:
419:Main article:
416:
413:
365:
364:
357:
351:
348:
341:
340:
337:
334:
327:
313:device drivers
304:
301:
247:
244:
223:
220:
207:
204:
196:
193:
120:address spaces
61:device drivers
15:
9:
6:
4:
3:
2:
4988:
4977:
4974:
4972:
4969:
4968:
4966:
4951:
4948:
4944:
4941:
4939:
4936:
4935:
4934:
4931:
4929:
4926:
4924:
4921:
4919:
4916:
4914:
4911:
4909:
4906:
4905:
4903:
4899:
4893:
4890:
4888:
4885:
4883:
4880:
4878:
4875:
4873:
4870:
4868:
4865:
4863:
4860:
4858:
4855:
4853:
4850:
4849:
4847:
4845:
4840:
4836:
4830:
4827:
4825:
4822:
4820:
4817:
4815:
4812:
4810:
4809:Memory paging
4807:
4805:
4802:
4800:
4797:
4796:
4794:
4791:
4786:
4782:
4772:
4769:
4767:
4764:
4762:
4759:
4757:
4754:
4753:
4751:
4749:
4743:
4737:
4734:
4732:
4729:
4727:
4724:
4722:
4719:
4717:
4714:
4712:
4709:
4707:
4704:
4702:
4699:
4696:
4692:
4688:
4685:
4684:
4682:
4678:
4675:
4673:
4669:
4659:
4656:
4654:
4651:
4649:
4648:Device driver
4646:
4645:
4643:
4639:
4633:
4630:
4628:
4625:
4623:
4620:
4618:
4615:
4613:
4610:
4608:
4605:
4603:
4600:
4598:
4595:
4594:
4592:
4590:
4589:Architectures
4586:
4583:
4581:
4577:
4571:
4568:
4566:
4563:
4561:
4558:
4556:
4553:
4551:
4548:
4546:
4543:
4541:
4538:
4536:
4533:
4531:
4528:
4526:
4523:
4522:
4520:
4516:
4510:
4507:
4505:
4502:
4500:
4497:
4495:
4492:
4490:
4487:
4485:
4482:
4480:
4477:
4476:
4474:
4470:
4466:
4459:
4454:
4452:
4447:
4445:
4440:
4439:
4436:
4430:
4427:
4426:
4417:
4413:
4409:
4405:
4400:
4396:
4391:
4387:
4383:
4379:
4376:
4373:
4369:
4366:
4362:
4359:
4355:
4352:
4351:
4340:
4336:
4332:
4328:
4324:
4320:
4316:
4312:
4308:
4304:
4300:
4299:Henry M. Levy
4295:
4291:
4287:
4283:
4279:
4275:
4271:
4266:
4252:
4245:
4244:
4238:
4228:on 2012-06-27
4227:
4223:
4217:
4213:
4212:
4206:
4196:on 2007-09-26
4192:
4188:
4184:
4180:
4176:
4172:
4168:
4164:
4160:
4153:
4149:
4145:
4141:
4135:
4131:
4127:
4123:
4119:
4115:
4109:
4105:
4101:
4100:
4094:
4090:
4086:
4082:
4078:
4074:
4070:
4065:
4060:
4056:
4052:
4051:
4046:
4042:
4038:
4032:
4028:
4024:
4020:
4019:
4013:
4000:
3993:
3989:
3985:
3981:
3976:
3971:
3967:
3963:
3959:
3955:
3954:
3948:
3944:
3940:
3936:
3932:
3928:
3917:
3913:
3907:
3903:
3902:
3896:
3891:
3886:
3882:
3878:
3874:
3870:
3869:Wulf, William
3865:
3861:
3854:
3853:
3848:
3844:
3840:
3836:
3835:Soltis, F. G.
3831:
3826:
3821:
3817:
3813:
3809:
3801:
3797:
3793:
3789:
3783:
3779:
3775:
3771:
3767:
3763:
3758:
3754:
3748:
3744:
3743:
3724:
3717:
3713:
3709:
3705:
3699:
3695:
3691:
3687:
3686:
3681:
3677:
3673:
3669:
3665:
3661:
3657:
3653:
3648:
3643:
3639:
3635:
3634:
3629:
3625:
3621:
3617:
3613:
3609:
3604:
3599:
3595:
3591:
3587:
3583:
3579:
3575:
3571:
3567:
3563:
3559:
3555:
3551:
3547:
3546:
3541:
3537:
3533:
3527:
3523:
3519:
3518:
3512:
3508:
3502:
3498:
3493:
3489:
3483:
3479:
3475:
3474:
3469:
3465:
3455:on 2006-11-01
3451:
3444:
3439:
3438:
3418:
3414:
3410:
3404:
3388:
3384:
3380:
3373:
3358:
3354:
3350:
3344:
3329:
3325:
3321:
3315:
3300:
3296:
3292:
3286:
3278:
3274:
3267:
3260:
3256:
3253:
3249:
3245:
3242:
3236:
3228:
3221:
3205:
3201:
3197:
3191:
3176:
3172:
3168:
3162:
3160:
3151:
3147:
3146:
3141:
3135:
3120:
3116:
3115:bell-labs.com
3112:
3106:
3097:
3088:
3080:
3074:
3063:
3062:
3054:
3046:
3042:
3036:
3028:
3024:
3023:
3015:
3008:
3002:
2993:
2984:
2982:
2980:
2978:
2962:
2958:
2954:
2948:
2941:
2930:on 2007-12-08
2929:
2925:
2921:
2914:
2912:
2905:
2901:
2898:
2894:
2890:
2887:
2883:
2879:
2876:
2872:
2868:
2865:
2859:
2843:
2839:
2838:1-56592-582-3
2835:
2829:
2827:
2816:
2814:
2812:
2802:
2795:
2793:
2792:
2785:
2783:3-540-54987-0
2779:
2775:
2771:
2767:
2763:
2756:
2747:
2738:
2736:
2726:
2712:
2708:
2704:
2698:
2693:
2688:
2684:
2680:
2673:
2665:
2661:
2656:
2651:
2647:
2643:
2639:
2632:
2623:
2621:
2619:
2617:
2615:
2607:
2601:
2593:
2589:
2585:
2581:
2574:
2556:
2549:
2534:
2532:
2527:
2520:
2505:
2501:
2495:
2480:
2476:
2472:
2468:
2464:
2459:
2454:
2450:
2446:
2442:
2435:
2424:
2417:
2410:
2402:
2398:
2394:
2388:
2383:
2378:
2374:
2367:
2359:
2355:
2351:
2344:
2342:
2340:
2328:
2321:
2314:
2312:
2303:
2299:
2294:
2289:
2285:
2281:
2277:
2270:
2261:
2253:
2247:
2243:
2239:
2232:
2223:
2221:
2211:
2202:
2193:
2186:
2182:
2176:
2172:
2168:
2162:
2153:
2151:
2141:
2139:
2137:
2135:
2133:
2131:
2129:
2119:
2117:
2110:
2104:
2096:
2090:
2086:
2079:
2063:
2059:
2055:
2049:
2047:
2042:
2030:
2024:
2017:
2011:
2005:
1999:
1995:
1986:
1983:
1981:
1978:
1976:
1973:
1971:
1968:
1967:
1961:
1959:
1955:
1951:
1948:
1944:
1940:
1935:
1933:
1929:
1925:
1921:
1917:
1913:
1909:
1899:
1897:
1896:
1891:
1887:
1884:that enabled
1883:
1879:
1874:
1872:
1868:
1864:
1859:
1857:
1853:
1852:error actions
1849:
1845:
1841:
1837:
1833:
1823:
1821:
1817:
1813:
1808:
1806:
1802:
1798:
1794:
1790:
1785:
1783:
1779:
1775:
1771:
1767:
1763:
1758:
1748:
1746:
1742:
1738:
1734:
1730:
1726:
1723:
1719:
1715:
1710:
1706:
1696:
1694:
1690:
1686:
1682:
1678:
1677:DragonFly BSD
1674:
1670:
1666:
1662:
1658:
1657:distributions
1654:
1649:
1647:
1643:
1639:
1638:lines of code
1634:
1630:
1626:
1622:
1617:
1615:
1611:
1607:
1602:
1597:
1595:
1591:
1587:
1583:
1579:
1574:
1569:
1567:
1563:
1559:
1555:
1547:
1542:
1537:
1527:
1525:
1521:
1516:
1513:
1507:
1497:
1495:
1491:
1486:
1482:
1478:
1474:
1470:
1465:
1463:
1459:
1453:
1443:
1441:
1438:In 1969, the
1436:
1434:
1430:
1426:
1422:
1418:
1414:
1410:
1404:
1389:
1387:
1383:
1379:
1373:
1363:
1361:
1357:
1353:
1349:
1344:
1339:
1329:
1327:
1323:
1319:
1313:
1300:
1297:
1296:
1295:
1288:
1285:
1282:
1281:
1280:
1276:
1274:
1270:
1269:network stack
1266:
1262:
1258:
1254:
1250:
1246:
1242:
1238:
1232:
1231:Hybrid kernel
1219:
1218:hybrid kernel
1214:
1210:
1208:
1203:
1198:
1196:
1192:
1188:
1183:
1181:
1177:
1171:
1169:
1165:
1161:
1152:
1150:
1146:
1142:
1138:
1132:
1129:
1125:
1121:
1117:
1107:
1105:
1100:
1093:
1090:
1087:
1085:
1081:
1080:
1079:
1076:
1074:
1069:
1067:
1063:
1059:
1055:
1051:
1046:
1042:
1034:
1031:
1028:
1025:
1024:
1023:
1021:
1017:
1011:
1009:
1005:
1001:
997:
993:
989:
985:
978:
965:
961:
956:
949:
948:address space
945:
942:
939:
935:
932:
928:
924:
923:
922:
918:
916:
912:
908:
902:
900:
896:
892:
888:
884:
880:
875:
871:
868:
864:
855:
850:
840:
838:
834:
830:
826:
821:
817:
813:
808:
806:
802:
798:
793:
789:
785:
783:
775:
772:
769:
766:
765:
764:
762:
758:
757:
751:
743:
741:
736:
735:device driver
730:
728:
724:
720:
719:Brinch Hansen
710:
708:
704:
703:shared memory
700:
696:
692:
689:
685:
676:
674:
670:
666:
658:
654:
650:
647:
643:
642:
641:
634:
630:
629:
628:
625:
623:
619:
614:
605:
603:
598:
596:
591:
589:
588:
583:
579:
574:
570:
568:
563:
559:
557:
553:
548:
544:
542:
537:
535:
531:
527:
522:
520:
516:
512:
508:
489:
486:
482:
478:
475:
471:
468:
464:
463:
462:
458:
456:
452:
447:
445:
441:
437:
432:
427:
422:
412:
410:
406:
402:
398:
393:
391:
387:
383:
379:
378:plug and play
374:
369:
362:
358:
356:
352:
349:
346:
345:
344:
338:
335:
332:
328:
325:
324:
323:
320:
318:
314:
310:
300:
298:
294:
290:
285:
283:
282:demand paging
279:
275:
269:
267:
263:
259:
253:
243:
241:
237:
233:
232:address space
229:
219:
217:
213:
203:
201:
192:
188:
186:
182:
178:
174:
170:
166:
162:
161:address space
158:
153:
151:
147:
143:
139:
136:
132:
129:The kernel's
127:
125:
121:
117:
113:
109:
105:
100:
98:
94:
90:
86:
82:
78:
74:
70:
66:
62:
58:
53:
49:
45:
41:
33:
28:
22:
4844:file systems
4736:Time-sharing
4579:
4407:
4385:
4371:
4364:
4357:
4306:
4302:
4273:
4269:
4258:. Retrieved
4242:
4230:. Retrieved
4226:the original
4210:
4198:. Retrieved
4191:the original
4162:
4158:
4125:
4098:
4054:
4048:
4017:
4005:. Retrieved
3957:
3951:
3943:the original
3938:
3920:. Retrieved
3900:
3880:
3876:
3851:
3842:
3818:(5): 66–77.
3815:
3811:
3769:
3741:
3730:. Retrieved
3684:
3637:
3631:
3593:
3589:
3549:
3543:
3516:
3496:
3472:
3457:. Retrieved
3450:the original
3421:. Retrieved
3412:
3403:
3391:. Retrieved
3383:www.l4ka.org
3382:
3372:
3361:. Retrieved
3352:
3343:
3332:. Retrieved
3323:
3314:
3303:. Retrieved
3294:
3285:
3277:the original
3266:
3235:
3220:
3208:. Retrieved
3199:
3190:
3179:. Retrieved
3144:
3134:
3123:. Retrieved
3114:
3105:
3096:
3087:
3073:
3060:
3053:
3045:the original
3035:
3027:the original
3021:
3019:Magee, Jim.
3014:
3006:
3001:
2992:
2965:. Retrieved
2956:
2947:
2938:
2932:. Retrieved
2928:the original
2858:
2846:. Retrieved
2837:
2801:
2789:
2787:
2765:
2755:
2750:Denning 1980
2746:
2729:Baiardi 1988
2725:
2714:. Retrieved
2682:
2672:
2645:
2641:
2631:
2605:
2600:
2583:
2579:
2573:
2561:. Retrieved
2548:
2538:15 September
2536:. Retrieved
2529:
2519:
2509:15 September
2507:. Retrieved
2503:
2494:
2483:. Retrieved
2448:
2444:
2434:
2409:
2372:
2366:
2358:the original
2353:
2286:(3): 22–32.
2283:
2279:
2269:
2260:
2241:
2231:
2214:Schroeder 72
2210:
2201:
2196:Denning 1976
2192:
2184:
2170:
2161:
2103:
2084:
2078:
2068:15 September
2066:. Retrieved
2057:
2023:
2010:
1998:
1958:self-healing
1936:
1905:
1893:
1889:
1875:
1860:
1850:operations,
1848:input/output
1829:
1809:
1786:
1760:
1712:
1655:in the many
1653:Linux kernel
1650:
1618:
1600:
1598:
1586:Virtualizing
1577:
1570:
1551:
1523:
1520:exec.library
1519:
1509:
1466:
1462:time-sharing
1455:
1452:Time-sharing
1437:
1408:
1406:
1375:
1366:Multikernels
1345:
1341:
1315:
1292:
1277:
1234:
1199:
1194:
1190:
1186:
1184:
1172:
1164:kernel space
1158:
1133:
1113:
1101:
1097:
1077:
1072:
1070:
1038:
1012:
1003:
992:multitasking
984:system calls
980:
971:Microkernels
919:
903:
889:kernel, the
885:kernel, the
879:Linux kernel
876:
872:
867:Ken Thompson
860:
820:microkernels
816:kernel space
809:
790:
786:
779:
773:
767:
760:
754:
752:
749:
731:
726:
722:
716:
682:
662:
653:type systems
639:
626:
615:
611:
599:
592:
585:
578:cryptography
575:
571:
564:
560:
549:
545:
538:
526:compile time
523:
504:
459:
448:
431:machine-code
428:
424:
415:System calls
394:
370:
366:
342:
321:
306:
289:kernel space
286:
270:
266:segmentation
255:
225:
209:
198:
189:
187:at runtime.
181:Linux kernel
169:Microkernels
154:
128:
112:kernel space
101:
85:input/output
39:
37:
4862:Device file
4852:Boot loader
4766:Round-robin
4691:Cooperative
4627:Rump kernel
4617:Multikernel
4607:Microkernel
4504:Usage share
4276:: S35–S67.
3295:windows.com
2886:oreilly.com
2563:20 December
1865:'s line of
1816:microkernel
1745:Mach kernel
1582:lower level
1562:computation
1372:Multikernel
1306:Nanokernels
1257:Mach kernel
1155:Performance
977:Microkernel
960:microkernel
829:nanokernels
673:Singularity
651:Inflexible
567:page tables
481:system call
421:System call
309:peripherals
297:Singularity
146:system call
81:peripherals
75:(after the
4965:Categories
4792:protection
4748:algorithms
4746:Scheduling
4695:Preemptive
4641:Components
4612:Monolithic
4479:Comparison
4260:2007-07-16
4232:2006-10-10
4200:2007-07-18
4007:2023-12-20
3922:2007-07-18
3732:2006-10-24
3596:(2): 4–7.
3459:2006-10-12
3423:2019-03-24
3363:2006-07-10
3334:2006-08-11
3305:2019-03-24
3200:asymco.com
3181:2016-09-29
3125:2006-08-17
2987:Liedtke 95
2967:2014-12-18
2934:2008-12-09
2716:2023-12-20
2485:2007-07-15
2038:References
1945:, and the
1882:hypervisor
1805:Windows 11
1801:Windows 9x
1797:Windows XP
1789:Windows NT
1782:Windows Me
1778:Windows 9x
1633:Networking
1614:user space
1378:multi-core
1332:Exokernels
1312:Nanokernel
1273:filesystem
1000:networking
865:developer
833:exokernels
768:Mechanism:
695:semaphores
501:Protection
384:, such as
361:PostScript
293:user space
274:hard drive
173:modularity
116:user space
77:bootloader
4882:Partition
4799:Bus error
4726:Real-time
4706:Interrupt
4632:Unikernel
4597:Exokernel
4339:208013080
4331:0734-2071
4323:1557-7333
4179:0001-0782
4081:0001-0782
4059:CiteSeerX
3984:0360-0300
3664:0001-0782
3642:CiteSeerX
3612:0163-5964
3574:207736773
3566:0360-0300
3210:2 October
2996:Härtig 97
2453:CiteSeerX
2226:Linden 76
2122:Roch 2004
1928:Pistachio
1906:Although
1867:mainframe
1784:in 2000.
1722:Macintosh
1584:concept.
1546:Unix-like
1512:Commodore
1496:systems.
1421:debuggers
1362:control.
1360:real-time
1348:unikernel
1338:Exokernel
761:mechanism
669:Microsoft
657:type safe
636:hardware.
602:isolation
541:CPU modes
491:requests.
474:call gate
467:interrupt
451:C library
440:C library
388:(PCI) or
140:. When a
135:low-level
131:interface
108:hard disk
4928:Live USB
4790:resource
4680:Concepts
4518:Variants
4499:Timeline
4290:26329062
4251:Archived
4148:Wulf, W.
4124:(1979).
4089:14422402
3992:16720589
3916:Archived
3871:(1975).
3800:Archived
3723:Archived
3714:(2001).
3682:(1973).
3620:14065743
3417:Archived
3393:24 March
3387:Archived
3357:Archived
3328:Archived
3299:Archived
3255:Archived
3244:Archived
3204:Archived
3175:Archived
3150:Archived
3119:Archived
2961:Archived
2900:Archived
2889:Archived
2878:Archived
2867:Archived
2848:24 March
2842:Archived
2741:Levin 75
2711:17709902
2664:14550794
2479:Archived
2423:Archived
2401:10027108
2327:Archived
2302:17487360
2169:(2008).
2062:Archived
2054:"Kernel"
1964:See also
1858:system.
1840:routines
1625:terminal
1573:printers
1477:security
1409:required
1207:by value
1205:copying
1191:concepts
1187:approach
1066:Redox OS
1050:GNU Hurd
937:program.
646:bytecode
622:compiler
582:compiler
530:run time
511:security
472:Using a
442:such as
89:software
48:computer
4923:Live CD
4877:Journal
4841:access,
4839:Storage
4716:Process
4622:vkernel
4489:History
4472:General
4187:8011765
4027:161–186
3862:. 2002.
3796:1706253
3672:9414037
3434:Sources
2864:dina.dk
1681:OpenBSD
1673:FreeBSD
1665:IBM AIX
1606:locking
1548:systems
1506:AmigaOS
1485:Multics
1320:or the
1271:or the
1261:FreeBSD
1243:'s own
1073:servers
1058:MkLinux
1004:servers
964:servers
958:In the
907:muLinux
895:Solaris
883:FreeBSD
774:Policy:
742:(IPC).
534:Denning
264:and/or
177:MINIX 3
142:process
73:startup
4731:Thread
4602:Hybrid
4580:Kernel
4414:
4397:
4337:
4329:
4321:
4288:
4218:
4185:
4177:
4136:
4110:
4087:
4079:
4061:
4033:
3990:
3982:
3908:
3794:
3784:
3749:
3700:
3670:
3662:
3644:
3618:
3610:
3572:
3564:
3528:
3503:
3484:
2780:
2709:
2699:
2662:
2475:269166
2473:
2455:
2399:
2389:
2300:
2248:
2177:
2091:
1924:Fiasco
1871:OS/360
1766:MS-DOS
1741:4.3BSD
1733:Darwin
1687:, and
1685:NetBSD
994:, and
881:, the
810:While
688:atomic
453:or an
262:paging
83:, and
67:&
57:memory
40:kernel
4933:Shell
4872:Inode
4335:S2CID
4319:eISSN
4286:S2CID
4254:(PDF)
4247:(PDF)
4194:(PDF)
4183:S2CID
4155:(PDF)
4085:S2CID
4002:(PDF)
3988:S2CID
3856:(PDF)
3792:S2CID
3726:(PDF)
3719:(PDF)
3668:S2CID
3616:S2CID
3570:S2CID
3453:(PDF)
3446:(PDF)
3065:(PDF)
2707:S2CID
2660:S2CID
2558:(PDF)
2471:S2CID
2426:(PDF)
2419:(PDF)
2397:S2CID
2330:(PDF)
2323:(PDF)
2298:S2CID
2058:Linfo
1991:Notes
1950:MINIX
1932:Linux
1878:state
1729:macOS
1714:Apple
1709:macOS
1689:macOS
1642:Linux
1594:pipes
1515:Amiga
1500:Amiga
1322:timer
1253:OSF/1
1245:macOS
1241:Apple
1137:Linux
1054:MINIX
911:Linux
891:HP-UX
444:Glibc
355:TWAIN
133:is a
69:cache
42:is a
4494:List
4412:ISBN
4395:ISBN
4327:ISSN
4216:ISBN
4175:ISSN
4134:ISBN
4108:ISBN
4077:ISSN
4031:ISBN
3980:ISSN
3906:ISBN
3782:ISBN
3747:ISBN
3698:ISBN
3660:ISSN
3608:ISSN
3562:ISSN
3526:ISBN
3501:ISBN
3482:ISBN
3395:2019
3212:2010
2895:and
2850:2019
2778:ISBN
2697:ISBN
2565:2023
2540:2022
2511:2022
2387:ISBN
2246:ISBN
2175:ISBN
2107:cf.
2089:ISBN
2070:2016
1956:and
1926:and
1908:Mach
1810:The
1707:and
1608:and
1564:was
1554:Unix
1536:Unix
1530:Unix
1510:The
1479:and
1469:hack
1458:Unix
1431:and
1419:and
1216:The
1143:and
1064:and
1045:port
1020:Hurd
1018:and
927:libc
863:UNIX
831:and
705:and
691:lock
667:and
405:port
331:BIOS
238:and
38:The
4950:PXE
4938:CLI
4918:HAL
4908:API
4711:IPC
4311:doi
4278:doi
4167:doi
4104:304
4069:doi
3970:hdl
3962:doi
3885:doi
3820:doi
3774:doi
3694:496
3652:doi
3598:doi
3554:doi
3522:673
3250:,
2791:sic
2770:doi
2687:doi
2650:doi
2588:doi
2463:doi
2377:doi
2288:doi
1939:QNX
1914:at
1892:or
1863:IBM
1737:XNU
1661:GNU
1659:of
1646:GNU
1610:I/O
1578:and
1473:CPU
1425:ROM
1352:API
1263:'s
1255:'s
1249:XNU
1182:.
1062:QNX
1016:QNX
931:gdb
913:in
887:AIX
837:Xen
818:),
807:).
671:'s
485:x86
455:API
401:I/O
278:RAM
212:USB
65:CPU
50:'s
4967::
4693:,
4418:).
4388:,
4384:,
4380:,
4333:.
4325:.
4317:.
4307:23
4305:.
4284:.
4274:20
4272:.
4249:.
4181:.
4173:.
4163:17
4161:.
4157:.
4128:.
4106:.
4083:.
4075:.
4067:.
4055:15
4053:.
4029:.
4021:.
3996:,
3986:.
3978:.
3968:.
3956:.
3937:.
3914:.
3879:.
3875:.
3858:.
3841:.
3816:31
3814:.
3810:.
3804:,
3798:.
3790:.
3780:.
3768:.
3721:.
3696:.
3688:.
3666:.
3658:.
3650:.
3638:13
3636:.
3614:.
3606:.
3592:.
3588:.
3568:.
3560:.
3548:.
3524:.
3476:.
3415:.
3411:.
3385:.
3381:.
3355:.
3351:.
3326:.
3322:.
3297:.
3293:.
3198:.
3173:.
3169:.
3158:^
3117:.
3113:.
2976:^
2959:.
2955:.
2937:.
2922:.
2910:^
2884:,
2873:,
2836:.
2825:^
2810:^
2786:.
2776:.
2764:.
2734:^
2705:.
2695:.
2681:.
2658:.
2646:10
2644:.
2640:.
2613:^
2584:33
2582:.
2528:.
2502:.
2477:.
2469:.
2461:.
2449:63
2447:.
2443:.
2395:.
2385:.
2352:.
2338:^
2325:.
2310:^
2296:.
2284:14
2282:.
2278:.
2240:.
2219:^
2183:.
2149:^
2127:^
2115:^
2056:.
2045:^
1898:.
1895:VM
1846:,
1807:.
1747:.
1683:,
1679:,
1675:,
1663:,
1631:.
1616:.
1568:.
1356:UI
1209:.
1170:.
1151:.
1060:,
1056:,
1052:,
990:,
917:.
784:.
729:.
709:.
675:.
665:JX
590:.
543:.
521:.
397:OS
284:.
175:.
152:.
122:,
99:.
4787:,
4697:)
4689:(
4457:e
4450:t
4443:v
4403:;
4401:)
4393:(
4374:;
4367:;
4360:;
4341:.
4313::
4292:.
4280::
4263:.
4235:.
4203:.
4169::
4142:.
4116:.
4091:.
4071::
4039:.
4010:.
3994:.
3972::
3964::
3958:8
3925:.
3893:.
3887::
3881:9
3828:.
3822::
3776::
3755:.
3735:.
3706:.
3674:.
3654::
3622:.
3600::
3594:8
3576:.
3556::
3550:8
3534:.
3509:.
3490:.
3462:.
3426:.
3397:.
3366:.
3337:.
3308:.
3229:.
3214:.
3184:.
3128:.
3081:.
3009:"
2970:.
2852:.
2772::
2719:.
2689::
2666:.
2652::
2594:.
2590::
2567:.
2542:.
2513:.
2488:.
2465::
2403:.
2379::
2304:.
2290::
2254:.
2097:.
2072:.
2018:.
648:.
363:)
333:)
23:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.