2297:
2069:
2636:
2890:(SAN) is a dedicated network that provides access to consolidated, block-level data storage. SANs are primarily used to make storage devices, such as disk arrays, tape libraries, and optical jukeboxes, accessible to servers so that the storage appears as locally attached devices to the operating system. A SAN typically has its own network of storage devices that are generally not accessible through the local area network by other devices. The cost and complexity of SANs dropped in the early 2000s to levels allowing wider adoption across both enterprise and small to medium-sized business environments.
822:
1858:
5168:"Many of the theoretical studies of the performance and design of the ARPA Network were developments of earlier work by Kleinrock ... Although these works concerned message switching networks, they were the basis for a lot of the ARPA network investigations ... The intention of the work of Kleinrock was to analyse the performance of store and forward networks, using as the primary performance measure the average message delay. ... Kleinrock extended the theoretical approaches of to the early ARPA network."
2289:
1625:
174:
8363:
1788:
1902:
1512:
8373:
3074:
50:
2203:
8383:
2804:(PAN) is a computer network used for communication among computers and different information technological devices close to one person. Some examples of devices that are used in a PAN are personal computers, printers, fax machines, telephones, PDAs, scanners, and video game consoles. A PAN may include wired and wireless devices. The reach of a PAN typically extends to 10 meters. A wired PAN is usually constructed with
1433:
2568:
6759:
2327:, often constructed per the OSI model, communications functions are divided up into protocol layers, where each layer leverages the services of the layer below it until the lowest layer controls the hardware that sends information across the media. The use of protocol layering is ubiquitous across the field of computer networking. An important example of a protocol stack is
5025:
Distributed
Communications" in the early 1960's. Also of note was work done by Donald Davies and others at the National Physical Laboratory in England in the mid-1960's. ... Another early major network development which affected development of the ARPANET was undertaken at the National Physical Laboratory in Middlesex, England, under the leadership of D. W. Davies.
1616:, the network topology is a ring, but the physical topology is often a star, because all neighboring connections can be routed via a central physical location. Physical layout is not completely irrelevant, however, as common ducting and equipment locations can represent single points of failure due to issues like fires, power failures and flooding.
2369:, also called TCP/IP, is the foundation of all modern networking. It offers connection-less and connection-oriented services over an inherently unreliable network traversed by datagram transmission using Internet protocol (IP). At its core, the protocol suite defines the addressing, identification, and routing specifications for
1486:. When one user is not sending packets, the link can be filled with packets from other users, and so the cost can be shared, with relatively little interference, provided the link is not overused. Often the route a packet needs to take through a network is not immediately available. In that case, the packet is
3817:. Netscape created a standard called secure socket layer (SSL). SSL requires a server with a certificate. When a client requests access to an SSL-secured server, the server sends a copy of the certificate to the client. The SSL client checks this certificate (all web browsers come with an exhaustive list of
2970:(WAN) is a computer network that covers a large geographic area such as a city, country, or spans even intercontinental distances. A WAN uses a communications channel that combines many types of media such as telephone lines, cables, and airwaves. A WAN often makes use of transmission facilities provided by
2870:(HAN) is a residential LAN used for communication between digital devices typically deployed in the home, usually a small number of personal computers and accessories, such as printers and mobile computing devices. An important function is the sharing of Internet access, often a broadband service through a
3026:(GAN) is a network used for supporting mobile users across an arbitrary number of wireless LANs, satellite coverage areas, etc. The key challenge in mobile communications is handing off communications from one local coverage area to the next. In IEEE Project 802, this involves a succession of terrestrial
5124:
Although there was considerable technical interchange between the NPL group and those who designed and implemented the ARPANET, the NPL Data
Network effort appears to have had little fundamental impact on the design of ARPANET. Such major aspects of the NPL Data Network design as the standard network
2126:
at a higher power level, or to the other side of obstruction so that the signal can cover longer distances without degradation. In most twisted-pair
Ethernet configurations, repeaters are required for cable that runs longer than 100 meters. With fiber optics, repeaters can be tens or even hundreds of
5509:
The authors wish to thank a number of colleagues for helpful comments during early discussions of international network protocols, especially R. Metcalfe, R. Scantlebury, D. Walden, and H. Zimmerman; D. Davies and L. Pouzin who constructively commented on the fragmentation and accounting issues; and
3064:
is a network that is under the administrative control of a single organization but supports a limited connection to a specific external network. For example, an organization may provide access to some aspects of its intranet to share data with its business partners or customers. These other entities
3051:
is a set of networks that are under the control of a single administrative entity. An intranet typically uses the
Internet Protocol and IP-based tools such as web browsers and file transfer applications. The administrative entity limits the use of the intranet to its authorized users. Most commonly,
1419:
Computer networks enhance how users communicate with each other by using various electronic methods like email, instant messaging, online chat, voice and video calls, and video conferencing. Networks also enable the sharing of computing resources. For example, a user can print a document on a shared
5278:
The hierarchical approach is further motivated by theoretical results (e.g., ) which show that, by optimally placing separators, i.e., elements that connect levels in the hierarchy, tremendous gain can be achieved in terms of both routing table size and update message churn. ... KLEINROCK, L., AND
4670:
As Kahn recalls: ... Paul Baran's contributions ... I also think Paul was motivated almost entirely by voice considerations. If you look at what he wrote, he was talking about switches that were low-cost electronics. The idea of putting powerful computers in these locations hadn't quite occurred to
2183:
based on the destination MAC address in each frame. They learn the association of physical ports to MAC addresses by examining the source addresses of received frames and only forward the frame when necessary. If an unknown destination MAC is targeted, the device broadcasts the request to all ports
1636:
is a virtual network that is built on top of another network. Nodes in the overlay network are connected by virtual or logical links. Each link corresponds to a path, perhaps through many physical links, in the underlying network. The topology of the overlay network may (and often does) differ from
1519:
The physical or geographic locations of network nodes and links generally have relatively little effect on a network, but the topology of interconnections of a network can significantly affect its throughput and reliability. With many technologies, such as bus or star networks, a single failure can
5196:
In mathematical modelling use is made of the theories of queueing processes and of flows in networks, describing the performance of the network in a set of equations. ... The analytic method has been used with success by
Kleinrock and others, but only if important simplifying assumptions are made.
3510:
priority schemes allowing selected traffic to bypass congestion. Priority schemes do not solve network congestion by themselves, but they help to alleviate the effects of congestion for critical services. A third method to avoid network congestion is the explicit allocation of network resources to
5024:
Aside from the technical problems of interconnecting computers with communications circuits, the notion of computer networks had been considered in a number of places from a theoretical point of view. Of particular note was work done by Paul Baran and others at the Rand
Corporation in a study "On
3461:
that use aggressive retransmissions to compensate for packet loss tend to keep systems in a state of network congestion even after the initial load is reduced to a level that would not normally induce network congestion. Thus, networks using these protocols can exhibit two stable states under the
3010:
in which some of the links between nodes are carried by open connections or virtual circuits in some larger network (e.g., the
Internet) instead of by physical wires. The data link layer protocols of the virtual network are said to be tunneled through the larger network. One common application is
2791:
has key components implemented at the nanoscale, including message carriers, and leverages physical principles that differ from macroscale communication mechanisms. Nanoscale communication extends communication to very small sensors and actuators such as those found in biological systems and also
3603:
is the monitoring of data being transferred over computer networks such as the
Internet. The monitoring is often done surreptitiously and may be done by or at the behest of governments, by corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require
4647:
Paul Baran ... focused on the routing procedures and on the survivability of distributed communication systems in a hostile environment, but did not concentrate on the need for resource sharing in its form as we now understand it; indeed, the concept of a software switch was not present in his
2275:
A firewall is a network device or software for controlling network security and access rules. Firewalls are inserted in connections between secure internal networks and potentially insecure external networks such as the
Internet. Firewalls are typically configured to reject access requests from
2163:
Network bridges and network switches are distinct from a hub in that they only forward frames to the ports involved in the communication whereas a hub forwards to all ports. Bridges only have two ports but a switch can be thought of as a multi-port bridge. Switches normally have numerous ports,
1409:
In 1995, the transmission speed capacity for
Ethernet increased from 10 Mbit/s to 100 Mbit/s. By 1998, Ethernet supported transmission speeds of 1 Gbit/s. Subsequently, higher speeds of up to 400 Gbit/s were added (as of 2018). The scaling of Ethernet has been a contributing
2612:
are structured and that similar addresses imply proximity within the network. Structured addresses allow a single routing table entry to represent the route to a group of devices. In large networks, the structured addressing used by routers outperforms unstructured addressing used by bridging.
4806:
the first occurrence in print of the term protocol in a data communications context ... the next hardware tasks were the detailed design of the interface between the terminal devices and the switching computer, and the arrangements to secure reliable transmission of packets of data over the
3011:
secure communications through the public Internet, but a VPN need not have explicit security features, such as authentication or content encryption. VPNs, for example, can be used to separate the traffic of different user communities over an underlying network with strong security features.
2921:
is part of a computer network infrastructure that provides a path for the exchange of information between different LANs or subnetworks. A backbone can tie together diverse networks within the same building, across different buildings, or over a wide area. When designing a network backbone,
1880:, optical fibers can simultaneously carry multiple streams of data on different wavelengths of light, which greatly increases the rate that data can be sent to up to trillions of bits per second. Optic fibers can be used for long runs of cable carrying very high data rates, and are used for
3591:
access, misuse, modification, or denial of the computer network and its network-accessible resources. Network security is used on a variety of computer networks, both public and private, to secure daily transactions and communications among businesses, government agencies, and individuals.
1925: – Terrestrial microwave communication uses Earth-based transmitters and receivers resembling satellite dishes. Terrestrial microwaves are in the low gigahertz range, which limits all communications to line-of-sight. Relay stations are spaced approximately 40 miles (64 km) apart.
1136:
proposed to the Central Committee of the Communist Party of the Soviet Union a detailed plan for the re-organization of the control of the Soviet armed forces and of the Soviet economy on the basis of a network of computing centers. Kitov's proposal was rejected, as later was the 1962
2388:
is a family of IEEE standards dealing with local area networks and metropolitan area networks. The complete IEEE 802 protocol suite provides a diverse set of networking capabilities. The protocols have a flat addressing scheme. They operate mostly at layers 1 and 2 of the OSI model.
1892:(MMF). Single-mode fiber has the advantage of being able to sustain a coherent signal for dozens or even a hundred kilometers. Multimode fiber is cheaper to terminate but is limited to a few hundred or even only a few dozens of meters, depending on the data rate and cable grade.
3038:
Networks are typically managed by the organizations that own them. Private enterprise networks may use a combination of intranets and extranets. They may also provide network access to the Internet, which has no single owner and permits virtually unlimited global connectivity.
5125:
interface, the routing algorithm, and the software structure of the switching node were largely ignored by the ARPANET designers. There is no doubt, however, that in many less fundamental ways the NPL Data Network had and effect on the design and evolution of the ARPANET.
1933: – Satellites also communicate via microwave. The satellites are stationed in space, typically in geosynchronous orbit 35,400 km (22,000 mi) above the equator. These Earth-orbiting systems are capable of receiving and relaying voice, data, and TV signals.
2832:(LAN) is a network that connects computers and devices in a limited geographical area such as a home, school, office building, or closely positioned group of buildings. Wired LANs are most commonly based on Ethernet technology. Other networking technologies such as
3872:
Unofficially, the Internet is the set of users, enterprises, and content providers that are interconnected by Internet Service Providers (ISP). From an engineering viewpoint, the Internet is the set of subnets, and aggregates of subnets, that share the registered
3327:
to another. Delay may differ slightly, depending on the location of the specific pair of communicating endpoints. Engineers usually report both the maximum and average delay, and they divide the delay into several components, the sum of which is the total delay:
2933:
For example, a large company might implement a backbone network to connect departments that are located around the world. The equipment that ties together the departmental networks constitutes the network backbone. Another example of a backbone network is the
6027:"IEEE Standard for Information Technology--Telecommunications and Information Exchange between Systems - Local and Metropolitan Area Networks--Specific Requirements - Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications"
3426:
occurs when a link or node is subjected to a greater data load than it is rated for, resulting in a deterioration of its quality of service. When networks are congested and queues become too full, packets have to be discarded, and participants must rely on
3096:
is the largest example of internetwork. It is a global system of interconnected governmental, academic, corporate, public, and private computer networks. It is based on the networking technologies of the Internet protocol suite. It is the successor of the
2187:
Bridges and switches divide the network's collision domain but maintain a single broadcast domain. Network segmentation through bridging and switching helps break down a large, congested network into an aggregation of smaller, more efficient networks.
2778:
Networks may be characterized by many properties or features, such as physical capacity, organizational purpose, user authorization, access rights, and others. Another distinct classification method is that of the physical extent or geographic scale.
4135:
Shortly after the first paper on time-shared computers by C. Strachey at the June 1959 UNESCO Information Processing conference, H. M. Teager and J. McCarthy at MIT delivered an unpublished paper "Time-shared Program Testing" at the August 1959 ACM
1189:
between computers over a network. Baran's work addressed adaptive routing of message blocks across a distributed network, but did not include routers with software switches, nor the idea that users, rather than the network itself, would provide the
3864:
is a community of interest under private administration usually by an enterprise, and is only accessible by authorized users (e.g. employees). Intranets do not have to be connected to the Internet, but generally have a limited connection. An
1705:. The overlay network has no control over how packets are routed in the underlying network between two overlay nodes, but it can control, for example, the sequence of overlay nodes that a message traverses before it reaches its destination.
5093:
Significant aspects of the network's internal operation, such as routing, flow control, software design, and network control were developed by a BBN team consisting of Frank Heart, Robert Kahn, Severo Omstein, William Crowther, and David
2145:. In addition to reconditioning and distributing network signals, a repeater hub assists with collision detection and fault isolation for the network. Hubs and repeaters in LANs have been largely obsoleted by modern network switches.
5601:
Council, National Research; Sciences, Division on Engineering and Physical; Board, Computer Science and Telecommunications; Applications, Commission on Physical Sciences, Mathematics, and; Committee, NII 2000 Steering (1998-02-05).
2463:
protocols that transfer multiple digital bit streams over optical fiber using lasers. They were originally designed to transport circuit mode communications from a variety of different sources, primarily to support circuit-switched
2104:. The three most significant octets are reserved to identify NIC manufacturers. These manufacturers, using only their assigned prefixes, uniquely assign the three least-significant octets of every Ethernet interface they produce.
1225:
were connected using 50 kbit/s circuits between the University of California at Los Angeles, the Stanford Research Institute, the University of California at Santa Barbara, and the University of Utah. Designed principally by
2218:
A router is an internetworking device that forwards packets between networks by processing the addressing or routing information included in the packet. The routing information is often processed in conjunction with the
3149:
is an overlay network, typically running on the Internet, that is only accessible through specialized software. It is an anonymizing network where connections are made only between trusted peers — sometimes called
3124:
Participants on the Internet use a diverse array of methods of several hundred documented, and often standardized, protocols compatible with the Internet protocol suite and the IP addressing system administered by the
4671:
him as being cost effective. So the idea of computer switches was missing. The whole notion of protocols didn't exist at that time. And the idea of computer-to-computer communications was really a secondary concern.
3414:
are often used to model queuing performance in a circuit-switched network. The network planner uses these diagrams to analyze how the network performs in each state, ensuring that the network is optimally designed.
2088:
and has the ability to process low-level network information. For example, the NIC may have a connector for plugging in a cable, or an aerial for wireless transmission and reception, and the associated circuitry.
1520:
cause the network to fail entirely. In general, the more interconnections there are, the more robust the network is; but the more expensive it is to install. Therefore, most network diagrams are arranged by their
3848:
Network administrators can see networks from both physical and logical perspectives. The physical perspective involves geographic locations, physical cabling, and the network elements (e.g., routers, bridges and
2571:
Routing calculates good paths through a network for information to take. For example, from node 1 to node 6 the best routes are likely to be 1-8-7-6, 1-8-10-6 or 1-9-10-6, as these are the shortest routes.
2300:
Message flows between two devices (A-B) at the four layers of the TCP/IP model in the presence of a router (R). Red flows are effective communication paths, black paths are across the actual network links.
984:. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the
1955: – Wireless LANs use a high-frequency radio technology similar to digital cellular. Wireless LANs use spread spectrum technology to enable communication between multiple devices in a limited area.
1807:
is widely used for cable television systems, office buildings, and other work-sites for local area networks. Transmission speed ranges from 200 million bits per second to more than 500 million bits per
1218:, pioneered the implementation of the concept in 1968-69 using 768 kbit/s links. Both Baran's and Davies' inventions were seminal contributions that influenced the development of computer networks.
2420:
protocol, which forms the basis for the authentication mechanisms used in VLANs (but it is also found in WLANs) – it is what the home user sees when the user has to enter a "wireless access key".
1849:. The transmission speed ranges from 2 Mbit/s to 10 Gbit/s. Twisted pair cabling comes in two forms: unshielded twisted pair (UTP) and shielded twisted-pair (STP). Each form comes in several
1455:
Packets consist of two types of data: control information and user data (payload). The control information provides data the network needs to deliver the user data, for example, source and destination
1066:, since it relies on the theoretical and practical application of the related disciplines. Computer networking was influenced by a wide array of technological developments and historical milestones.
6763:
2496:. ATM has similarities with both circuit and packet switched networking. This makes it a good choice for a network that must handle both traditional high-throughput data traffic, and real-time,
5307:
The Spanish, dark horses, were the first people to have a public network. They'd got a bank network which they craftily turned into a public network overnight, and beat everybody to the post.
3857:, map onto one or more transmission media. For example, a common practice in a campus of buildings is to make a set of LAN cables in each building appear to be a common subnet, using VLANs.
3483:
techniques where endpoints typically slow down or sometimes even stop transmission entirely when the network is congested to try to avoid congestive collapse. Specific techniques include:
3400:. The number of rejected calls is a measure of how well the network is performing under heavy traffic loads. Other types of performance measures can include the level of noise and echo.
1841:
and other standards. It typically consists of 4 pairs of copper cabling that can be utilized for both voice and data transmission. The use of two wires twisted together helps to reduce
2994:
is a network that a single organization builds to interconnect its office locations (e.g., production sites, head offices, remote offices, shops) so they can share computer resources.
2578:
is the process of selecting network paths to carry network traffic. Routing is performed for many kinds of networks, including circuit switching networks and packet switched networks.
5227:
Hierarchical addressing systems for network routing have been proposed by Fultz and, in greater detail, by McQuillan. A recent very full analysis may be found in Kleinrock and Kamoun.
3407:(ATM) network, performance can be measured by line rate, quality of service (QoS), data throughput, connect time, stability, technology, modulation technique, and modem enhancements.
6659:
3089:
is the connection of multiple different types of computer networks to form a single computer network using higher-layer network protocols and connecting them together using routers.
1582:: each node is connected to its left and right neighbor node, such that all nodes are connected and that each node can reach each other node by traversing nodes left- or rightwards.
2593:
can also forward packets and perform routing, though because they lack specialized hardware, may offer limited performance. The routing process directs forwarding on the basis of
1648:
Overlay networks have been used since the early days of networking, back when computers were connected via telephone lines using modems, even before data networks were developed.
3837:, which usually means they are in the same geographic location and are on the same LAN, whereas a network administrator is responsible for keeping that network up and running. A
3410:
There are many ways to measure the performance of a network, as each network is different in nature and design. Performance can also be modeled instead of measured. For example,
3908:
mechanism. Intranets and extranets can be securely superimposed onto the Internet, without any access by general Internet users and administrators, using secure VPN technology.
2909:
For example, a university campus network is likely to link a variety of campus buildings to connect academic colleges or departments, the library, and student residence halls.
1420:
printer or use shared storage devices. Additionally, networks allow for the sharing of files and information, giving authorized users access to data stored on other computers.
4214:
3841:
has less of a connection of being in a local area and should be thought of as a set of arbitrarily located users who share a set of servers, and possibly also communicate via
3694:
data so only the intended recipient can decrypt it, with no dependency on third parties. End-to-end encryption prevents intermediaries, such as Internet service providers or
4829:
2134:
that affects network performance and may affect proper function. As a result, many network architectures limit the number of repeaters used in a network, e.g., the Ethernet
4890:
2902:(CAN) is made up of an interconnection of LANs within a limited geographical area. The networking equipment (switches, routers) and transmission media (optical fiber,
2237:
Modems (modulator-demodulator) are used to connect network nodes via wire not originally designed for digital network traffic, or for wireless. To do this one or more
1759:(LAN) technology are collectively known as Ethernet. The media and protocol standards that enable communication between networked devices over Ethernet are defined by
1655:. Even today, each Internet node can communicate with virtually any other through an underlying mesh of sub-networks of wildly different topologies and technologies.
3607:
Computer and network surveillance programs are widespread today, and almost all Internet traffic is or could potentially be monitored for clues to illegal activity.
5019:
2276:
unrecognized sources while allowing actions from recognized ones. The vital role firewalls play in network security grows in parallel with the constant increase in
3809:
The introduction and rapid growth of e-commerce on the World Wide Web in the mid-1990s made it obvious that some form of authentication and encryption was needed.
2589:
through intermediate nodes. Intermediate nodes are typically network hardware devices such as routers, bridges, gateways, firewalls, or switches. General-purpose
6178:
2377:, the next generation of the protocol with a much enlarged addressing capability. The Internet protocol suite is the defining set of protocols for the Internet.
1701:
in the network. On the other hand, an overlay network can be incrementally deployed on end-hosts running the overlay protocol software, without cooperation from
1114:
4947:
6157:
3492:
3173:
is anonymous (that is, IP addresses are not publicly shared), and therefore users can communicate with little fear of governmental or corporate interference.
2223:. A router uses its routing table to determine where to forward packets and does not require broadcasting packets which is inefficient for very big networks.
1242:
carried out mathematical work to model the performance of packet-switched networks, which underpinned the development of the ARPANET. His theoretical work on
3052:
an intranet is the internal LAN of an organization. A large intranet typically has at least one web server to provide users with organizational information.
6701:
4914:
4363:
Essentially all the work was defined by 1961, and fleshed out and put into formal written form in 1962. The idea of hot potato routing dates from late 1960.
3860:
Users and administrators are aware, to varying extents, of a network's trust and scope characteristics. Again using TCP/IP architectural terminology, an
1368:
published their paper "Ethernet: Distributed Packet Switching for Local Computer Networks" and collaborated on several patents received in 1977 and 1978.
6634:
4731:
Davies's invention of packet switching and design of computer communication networks ... were a cornerstone of the development which led to the Internet
3065:
are not necessarily trusted from a security standpoint. The network connection to an extranet is often, but not always, implemented via WAN technology.
1941:
use several radio communications technologies. The systems divide the region covered into multiple geographic areas. Each area is served by a low-power
1497:(MTU). A longer message may be fragmented before it is transferred and once the packets arrive, they are reassembled to construct the original message.
690:
2930:
are critical factors to take into account. Normally, the backbone network's capacity is greater than that of the individual networks connected to it.
3631:
2097:
1608:: nodes are arranged hierarchically. This is the natural topology for a larger Ethernet network with multiple switches and without redundant meshing.
5906:
6925:
5640:
4501:
5698:
1268:
was the first to make the hosts responsible for the reliable delivery of data, rather than this being a centralized service of the network itself.
6475:
5644:
5197:... It is heartening in Kleinrock's work to see the good correspondence achieved between the results of analytic methods and those of simulation.
1670:, which maps keys to nodes in the network. In this case, the underlying network is an IP network, and the overlay network is a table (actually a
3014:
VPN may have best-effort performance or may have a defined service level agreement (SLA) between the VPN customer and the VPN service provider.
2613:
Structured IP addresses are used on the Internet. Unstructured MAC addresses are used for bridging on Ethernet and similar local area networks.
4001:
4036:
3748:-based communications systems do not include end-to-end encryption. These systems can only guarantee the protection of communications between
4120:
1215:
6667:
2548:
1596:: each node is connected to an arbitrary number of neighbors in such a way that there is at least one traversal from any node to any other.
1145:
4277:
2130:
Repeaters work on the physical layer of the OSI model but still require a small amount of time to regenerate the signal. This can cause a
6872:
6449:
5619:
5138:
4445:
1876:. Some advantages of optical fibers over metal wires are very low transmission loss and immunity to electrical interference. Using dense
6605:
4177:
7399:
5038:
3869:
is an extension of an intranet that allows secure communications to users outside of the intranet (e.g. business partners, customers).
2974:, such as telephone companies. WAN technologies generally function at the lower three layers of the OSI model: the physical layer, the
2544:
2597:, which maintain a record of the routes to various network destinations. Most routing algorithms use only one network path at a time.
3102:
2854:
to provide connectivity. Current Ethernet or other IEEE 802.3 LAN technologies operate at data transfer rates up to and in excess of
1651:
The most striking example of an overlay network is the Internet itself. The Internet itself was initially built as an overlay on the
797:
6074:
5353:
5210:
3833:
Users and network administrators typically have different views of their networks. Users can share printers and some servers from a
4820:
3901:
3270:, i.e., the average rate of successful data transfer through a communication path. The throughput is affected by processes such as
5109:
The Froehlich/Kent Encyclopedia of Telecommunications: Volume 1 - Access Charges in the U.S.A. to Basics of Digital Communications
4557:
2468:. However, due to its protocol neutrality and transport-oriented features, SONET/SDH also was the obvious choice for transporting
1402:
In 1980, Ethernet was upgraded from the original 2.94 Mbit/s protocol to the 10 Mbit/s protocol, which was developed by
4156:
3775:
The end-to-end encryption paradigm does not directly address risks at the endpoints of the communication themselves, such as the
2765:
2520:
6536:
5179:
4974:
In nearly all respects, Davies' original proposal, developed in late 1965, was similar to the actual networks being built today.
8116:
8088:
4874:
4661:
4355:
3918:
2308:
is a set of rules for exchanging information over a network. Communication protocols have various characteristics. They may be
114:
6768:
827:
8141:
7201:
7172:
6574:
6432:
6132:
6107:
6046:
5999:
5762:
5613:
5263:
5220:
5189:
4995:
4724:
4694:
4252:
4114:
4081:
4015:
3904:
communications. When money or sensitive information is exchanged, the communications are apt to be protected by some form of
2540:
2350:
86:
6507:
5848:
3690:
paradigm of uninterrupted protection of data traveling between two communicating parties. It involves the originating party
2054:. Any particular piece of equipment will frequently contain multiple building blocks and so may perform multiple functions.
7992:
5455:
2954:(MAN) is a large computer network that interconnects users with computer resources in a geographic region of the size of a
6798:
Kurose James F and Keith W. Ross: Computer Networking: A Top-Down Approach Featuring the Internet, Pearson Education 2005.
6329:
6052:
6005:
4416:
Almost immediately after the 1965 meeting, Davies conceived of the details of a store-and-forward packet switching system.
3795:, which relates to things such as the identities of the endpoints and the times and quantities of messages that are sent.
3133:. Service providers and large enterprises exchange information about the reachability of their address spaces through the
2839:
also provide a way to create a wired LAN using existing wiring, such as coaxial cables, telephone lines, and power lines.
8146:
7418:
5936:
5758:
4990:. Johns Hopkins studies in the history of technology New series. Baltimore: Johns Hopkins Univ. Press. pp. 153–196.
4532:
4067:
3232:
3126:
3106:
2556:
1555:
17:
5158:
3825:
for use in the session. The session is now in a very secure encrypted tunnel between the SSL server and the SSL client.
93:
7651:
5984:
IEEE STD 802.1X-2020 (Revision of IEEE STD 802.1X-2010 Incorporating IEEE STD 802.1Xbx-2014 and IEEE STD 802.1Xck-2018)
4307:
4050:
1284:
1106:
826:
680:
409:
6190:
6149:
5279:
KAMOUN, F. Hierarchical routing for large networks: Performance evaluation and optimization. Computer Networks (1977).
2906:
cabling, etc.) are almost entirely owned by the campus tenant or owner (an enterprise, university, government, etc.).
8298:
8126:
7656:
5823:
5674:
5323:
5166:(PhD thesis). Department of Electrical Engineering, Imperial College of Science and Technology, University of London.
4958:
4757:
4439:
2309:
2026:
Apart from any physical transmission media, networks are built from additional basic system building blocks, such as
1191:
1071:
133:
67:
2938:, which is a massive, global system of fiber-optic cable and optical networking that carry the bulk of data between
1716:). Academic research includes end system multicast, resilient routing and quality of service studies, among others.
1612:
The physical layout of the nodes in a network may not necessarily reflect the network topology. As an example, with
8386:
7480:
6976:
6920:
1967:
1877:
1587:
1334:
1227:
754:
337:
100:
7774:
6895:
6865:
6774:
6693:
5529:
4922:
3834:
1117:
in Paris that year. McCarthy was instrumental in the creation of three of the earliest time-sharing systems (the
1109:
initiated the first project to implement time-sharing of user programs at MIT. Strachey passed the concept on to
650:
4777:
8065:
8027:
7684:
7392:
7088:
6986:
5880:
5477:
5117:
3654:
3650:
3541:
3428:
3185:
2923:
2508:
2480:
Asynchronous Transfer Mode (ATM) is a switching technique for telecommunication networks. It uses asynchronous
2456:
2428:
Ethernet is a family of technologies used in wired LANs. It is described by a set of standards together called
2123:
1915:
Network connections can be established wirelessly using radio or other electromagnetic means of communication.
1881:
1641:
networks are overlay networks. They are organized as nodes of a virtual system of links that run on top of the
1156:
1118:
844:
828:
640:
71:
6627:
3511:
specific flows. One example of this is the use of Contention-Free Transmission Opportunities (CFTXOPs) in the
2096:—usually stored in the controller's permanent memory. To avoid address conflicts between network devices, the
1748:, the software to handle the media is defined at layers 1 and 2 — the physical layer and the data link layer.
635:
8207:
8184:
7914:
7904:
7366:
6915:
6900:
5018:(Report). Bolt, Beranek & Newman Inc. 1 April 1981. pp. 13, 53 of 183 (III-11 on the printed copy).
3838:
3291:
2332:
1346:
1126:
790:
749:
266:
82:
8288:
7876:
7784:
7689:
7465:
7450:
6961:
6946:
6905:
3885:
names of servers are translated to IP addresses, transparently to users, via the directory function of the
3695:
3295:
2524:
2313:
2063:
2027:
905:
595:
439:
386:
201:
6219:
630:
8376:
8111:
7609:
7127:
7074:
6795:
Wendell Odom, Rus Healy, Denise Donohue. (2010) CCIE Routing and Switching. Indianapolis, IN: Cisco Press
6489:
5914:
4747:
3964:
3776:
3623:
2758:
2119:
1656:
1534:: all nodes are connected to a common medium along this medium. This was the layout used in the original
1231:
6264:
4470:
3242:
that defines the format and sequencing of messages between clients and servers of that network service.
8407:
8348:
7997:
7142:
6981:
6858:
5720:
5690:
5061:
4934:
Historians credit seminal insights to Welsh scientist Donald W. Davies and American engineer Paul Baran
4376:
3821:
preloaded), and if the certificate checks out, the server is authenticated and the client negotiates a
3661:
society, with limited political and personal freedoms. Fears such as this have led to lawsuits such as
3404:
3316:
3159:
3130:
3077:
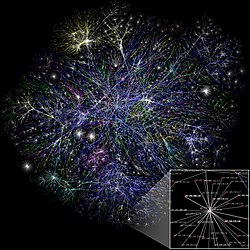
Partial map of the Internet based on 2005 data. Each line is drawn between two nodes, representing two
2991:
2717:
2481:
2469:
2253:
sent over a standard voice telephone line. Modems are still commonly used for telephone lines, using a
2073:
1094:
to be transmitted over regular unconditioned telephone lines at a speed of 110 bits per second (bit/s).
759:
665:
660:
625:
424:
322:
261:
3853:) that interconnect via the transmission media. Logical networks, called, in the TCP/IP architecture,
8366:
8293:
8268:
8131:
7779:
7385:
7177:
6996:
6956:
6951:
6910:
5782:
4714:
3850:
3738:
3646:
3170:
2951:
2712:
1972:
1885:
1846:
1702:
1494:
1280:
942:
347:
2100:(IEEE) maintains and administers MAC address uniqueness. The size of an Ethernet MAC address is six
1663:
are the means that allow mapping of a fully connected IP overlay network to its underlying network.
8217:
8050:
7636:
7505:
7220:
7107:
6971:
4902:
This was the first digital local network in the world to use packet switching and high-speed links.
3804:
3722:
3569:
2650:
2536:
2180:
1929:
1889:
1826:
1772:
1493:
The physical link technologies of packet networks typically limit the size of packets to a certain
1235:
825:
783:
685:
645:
152:
38:
31:
4101:
3568:
on devices connected to the network, or to prevent these devices from accessing the network via a
2846:(WAN) using a router. The defining characteristics of a LAN, in contrast to a WAN, include higher
1155:
In 1963, J. C. R. Licklider sent a memorandum to office colleagues discussing the concept of the "
543:
8278:
8212:
8103:
7919:
7579:
6966:
6689:
3969:
3928:
3905:
3878:
3784:
3480:
3432:
3204:
3134:
3003:
2875:
2739:
2366:
2254:
1979:
1842:
1599:
1564:: all nodes are connected to a special central node. This is the typical layout found in a small
1449:
1230:, the network's routing, flow control, software design and network control were developed by the
1122:
1008:
1000:
766:
585:
352:
286:
241:
60:
6100:
The evolution of mobile communications in the US and Europe: Regulation, technology, and markets
5384:
Kirstein, P.T. (1999). "Early experiences with the Arpanet and Internet in the United Kingdom".
2635:
8343:
8174:
8055:
7822:
7812:
7807:
7354:
7293:
7182:
7162:
7111:
7069:
5354:"Designed for Change: End-to-End Arguments, Internet Innovation, and the Net Neutrality Debate"
4269:
3949:
3938:
3698:, from reading or tampering with communications. End-to-end encryption generally protects both
3687:
3324:
2817:
2751:
2417:
2401:
2305:
1985:
1677:
Overlay networks have also been proposed as a way to improve Internet routing, such as through
1667:
1424:
leverages resources from multiple computers across a network to perform tasks collaboratively.
1199:
931:
670:
655:
570:
6422:
5603:
5107:
4684:
4429:
4185:
4097:
3675:
has hacked into government websites in protest of what it considers "draconian surveillance".
2448:
protocol family for home users today. IEEE 802.11 shares many properties with wired Ethernet.
2249:
that can be tailored to give the required properties for transmission. Early modems modulated
107:
8313:
8283:
8273:
8169:
8083:
7959:
7899:
7866:
7856:
7739:
7704:
7694:
7631:
7500:
7475:
7470:
7435:
7137:
7103:
7005:
6941:
6601:
6557:
Simmonds, A; Sandilands, P; van Ekert, L (2004). "An Ontology for Network Security Attacks".
4244:
3683:
3584:
3255:
2871:
2801:
2792:
tends to operate in environments that would be too harsh for other communication techniques.
2729:
2697:
2660:
2605:
2393:
2076:
network interface in the form of an accessory card. A lot of network interfaces are built-in.
2009:
2005:
1573:
1479:
1421:
1396:
In 1977, the first long-distance fiber network was deployed by GTE in Long Beach, California.
1386:
1323:
996:
771:
590:
560:
449:
404:
5046:
4701:
Baran had put more emphasis on digital voice communications than on computer communications.
4235:
Gillies, James M.; Gillies, James; Gillies, James and Cailliau Robert; Cailliau, R. (2000).
2444:
standards, also widely known as WLAN or WiFi, is probably the most well-known member of the
2068:
8073:
8045:
8017:
8012:
7841:
7817:
7769:
7752:
7747:
7729:
7719:
7714:
7676:
7626:
7621:
7538:
7484:
7334:
7308:
6742:
6458:
6404:
6370:
5980:"IEEE Standard for Local and Metropolitan Area Networks--Port-Based Network Access Control"
5748:
5543:
4516:
Both Paul Baran and Donald Davies in their original papers anticipated the use of T1 trunks
3897:
3893:
3822:
3810:
3600:
3476:
3444:
3287:
3279:
3275:
3239:
2887:
2855:
2675:
2665:
2292:
The TCP/IP model and its relation to common protocols used at different layers of the model
2270:
2051:
2012:
but does not prevent sending large amounts of information (they can have high throughput).
1989:
1978:
Extending the Internet to interplanetary dimensions via radio waves and optical means, the
1403:
1243:
1203:
1098:
1059:
1015:
538:
419:
5725:
Entrepreneurial Capitalism and Innovation: A History of Computer Communications, 1968-1988
5360:
4431:
The Innovators: How a Group of Hackers, Geniuses, and Geeks Created the Digital Revolution
3634:, governments now possess an unprecedented ability to monitor the activities of citizens.
8:
8338:
8263:
8179:
8164:
7929:
7709:
7666:
7661:
7558:
7548:
7520:
7303:
7255:
7132:
6811:
Network Communication Architecture and Protocols: OSI Network Architecture 7 Layers Model
6081:
5957:
5239:
Feldmann, Anja; Cittadini, Luca; Mühlbauer, Wolfgang; Bush, Randy; Maennel, Olaf (2009).
4666:
Entrepreneurial Capitalism and Innovation: A History of Computer Communications 1968–1988
3714:
3484:
3464:
3023:
2899:
1732:
1712:
manages an overlay network that provides reliable, efficient content delivery (a kind of
1709:
1472:
1468:
1371:
1254:
1087:
1039:
992:
969:
575:
444:
434:
429:
281:
226:
216:
5039:"Internet Began 35 Years Ago at UCLA with First Message Ever Sent Between Two Computers"
8303:
8202:
8078:
8035:
7944:
7886:
7871:
7861:
7646:
7445:
7240:
7147:
6580:
6469:
5663:
5634:
5583:
5436:
5401:
5269:
5084:
4822:
A Digital Communication Network for Computers Giving Rapid Response at remote Terminals
4797:
4553:
4493:
4407:
3959:
3886:
3814:
3780:
3753:
3749:
3745:
3663:
3545:
3537:
3507:
3472:
3447:
of new connections. A consequence of these latter two is that incremental increases in
3423:
3366:
3357:
A certain minimum level of delay is experienced by signals due to the time it takes to
3344:
3208:
3118:
3110:
2927:
2847:
2829:
2670:
2197:
2176:
2047:
1822:
1756:
1698:
1678:
1464:
1211:
1195:
1186:
1149:
1110:
1063:
965:
414:
367:
342:
231:
221:
6299:
5250:. ReArch '09. New York, NY, USA: Association for Computing Machinery. pp. 43–48.
4819:
Davies, Donald; Bartlett, Keith; Scantlebury, Roger; Wilkinson, Peter (October 1967).
4148:
3877:
space and exchange information about the reachability of those IP addresses using the
8323:
8253:
8232:
8194:
8002:
7969:
7949:
7641:
7553:
7427:
7349:
7298:
7230:
7187:
7028:
6814:
6801:
6570:
6532:
6428:
6128:
6103:
6042:
5995:
5856:, Third Annual International Symposium on Advanced Radio Technologies, archived from
5829:
5819:
5670:
5609:
5500:
5319:
5259:
5216:
5185:
5113:
4991:
4882:
4753:
4720:
4716:
Turing's Legacy: A History of Computing at the National Physical Laboratory 1945-1995
4690:
4638:
4599:
4435:
4399:
4347:
4324:
4303:
4248:
4237:
4110:
4077:
4046:
4011:
3979:
3769:
3756:, not between the communicating parties themselves. Examples of non-E2EE systems are
3726:
3672:
3658:
3627:
3358:
3350:
3271:
2967:
2955:
2939:
2935:
2867:
2843:
2788:
2724:
2655:
2598:
2586:
2465:
2131:
2101:
2081:
2021:
1873:
1791:
1725:
1671:
1652:
1565:
1483:
1482:
of the transmission medium can be better shared among users than if the network were
1382:. This underlying infrastructure was used for expanding TCP/IP networks in the 1980s.
1272:
1239:
985:
961:
927:
874:
854:
711:
377:
327:
236:
211:
6831:
5440:
5088:
4988:
Transforming computer technology: information processing for the Pentagon, 1962-1986
4497:
4411:
1159:", a computer network intended to allow general communications among computer users.
8156:
8040:
8007:
7802:
7724:
7613:
7599:
7594:
7543:
7455:
7408:
6881:
6778:
6732:
6584:
6562:
6394:
6360:
6295:
6034:
5987:
5573:
5533:
5492:
5428:
5405:
5393:
5324:"RCP, the Experimental Packet-Switched Data Transmission Service of the French PTT"
5273:
5251:
5076:
4855:
4801:
4789:
4630:
4591:
4485:
4391:
4339:
3818:
3792:
3580:
3522:
3506:
Another method to avoid the negative effects of network congestion is implementing
3458:
3397:
3332:
3155:
2918:
2903:
2707:
2582:
1993:
1937:
1910:
1737:
1521:
1506:
1350:
1182:
1167:
1163:
1055:
954:
898:
813:
470:
459:
357:
301:
5752:
5587:
4844:"all users of the network will provide themselves with some kind of error control"
2511:, which is the connection between an Internet service provider and the home user.
2504:
must be established between two endpoints before the actual data exchange begins.
2320:
or packet switching, and they may use hierarchical addressing or flat addressing.
1959:
defines a common flavor of open-standards wireless radio-wave technology known as
1861:
2007 map showing submarine optical fiber telecommunication cables around the world
8227:
8121:
8093:
7987:
7939:
7924:
7909:
7764:
7759:
7699:
7589:
7563:
7515:
7460:
7273:
7235:
7206:
6818:
6566:
6511:
6038:
5991:
5857:
4206:
4032:
3974:
3954:
3933:
3813:
took the first shot at a new standard. At the time, the dominant web browser was
3761:
3699:
3611:
3557:
3320:
3181:
3007:
2975:
2609:
2501:
2500:
content such as voice and video. ATM uses a connection-oriented model in which a
2497:
2340:
2172:
2168:
2164:
facilitating a star topology for devices, and for cascading additional switches.
1950:
1682:
1633:
1547:
1460:
1456:
1440:
Most modern computer networks use protocols based on packet-mode transmission. A
1307:
1291:
1276:
1019:
1004:
977:
950:
938:
706:
487:
362:
271:
206:
160:
6845:
6745:
6726:
6407:
6388:
6373:
6354:
6314:
5240:
3526:
1997:
1872:
is a glass fiber. It carries pulses of light that represent data via lasers and
1857:
1568:
LAN, where each client connects to a central network switch, and logically in a
27:
Network that allows computers to share resources and communicate with each other
8333:
8237:
8136:
7982:
7954:
7359:
7283:
7245:
7117:
6628:"Bigger Monster, Weaker Chains: The Growth of an American Surveillance Society"
6026:
5979:
5928:
5546:
5523:
5012:
4618:
4579:
3882:
3703:
3657:—have expressed concern that increasing surveillance of citizens may lead to a
3615:
3561:
3496:
3436:
3390:
3373:
delays can range from less than a microsecond to several hundred milliseconds.
3192:
3188:
for members or users of the network, or to help the network itself to operate.
3114:
2971:
2702:
2493:
2324:
2238:
2158:
2154:
2043:
2039:
1850:
1697:
have not seen wide acceptance largely because they require modification of all
1551:
1441:
1354:
1319:
1079:
1023:
973:
935:
716:
522:
497:
492:
466:
455:
332:
296:
291:
251:
189:
5746:
5496:
5432:
5419:
Kirstein, Peter T. (2009). "The early history of packet switching in the UK".
5359:. Information Technology and Innovation Foundation. p. 11. Archived from
5292:
4595:
4528:
4343:
1463:
codes, and sequencing information. Typically, control information is found in
8401:
8222:
7510:
7268:
7225:
7064:
7018:
6840:
5965:
5833:
5504:
4886:
4743:
4642:
4603:
4403:
4351:
3943:
3565:
3500:
3411:
3338:
3307:
3283:
2979:
2594:
2246:
2220:
2085:
1868:
1803:
1798:
The following classes of wired technologies are used in computer networking.
1776:
1741:
1487:
1247:
1178:
1133:
1031:
1027:
946:
864:
675:
580:
565:
507:
256:
246:
5255:
5080:
4793:
4634:
4489:
4395:
2346:
There are many communication protocols, a few of which are described below.
2296:
8318:
7977:
7152:
3842:
3638:
3588:
3448:
3235:(DHCP) to ensure that the equipment on the network has a valid IP address.
3166:
3086:
3027:
2690:
2680:
2552:
2488:. This differs from other protocols such as the Internet protocol suite or
2460:
2317:
2250:
2142:
2035:
1833:
1694:
1638:
1605:
1593:
1579:
1569:
1561:
1265:
1102:
1091:
879:
620:
517:
372:
6240:
5578:
5561:
5331:
1070:
In the late 1950s, a network of computers was built for the U.S. military
8308:
7934:
7846:
7278:
7260:
7043:
7033:
7023:
5510:
S. Crocker who commented on the creation and destruction of associations.
3757:
3440:
3396:
In circuit-switched networks, network performance is synonymous with the
3216:
2851:
2645:
2441:
2413:
2405:
2397:
2336:
2277:
2093:
1956:
1942:
1818:
1764:
1624:
1531:
1365:
1342:
1315:
1207:
1035:
891:
859:
3347: – time it takes to push the packet's bits onto the link
2343:
and the home user's personal computer when the user is surfing the web.
1975:
is used, which limits the physical positioning of communicating devices.
8328:
8258:
7851:
7584:
7440:
6561:. Lecture Notes in Computer Science. Vol. 3285. pp. 317–323.
5137:
Heart, F.; McKenzie, A.; McQuillian, J.; Walden, D. (January 4, 1978).
4073:
3923:
3874:
3788:
3691:
3668:
3452:
3382:
3370:
3263:
3212:
3078:
2567:
2519:
There are a number of different digital cellular standards, including:
2485:
2429:
2242:
2135:
1884:
to interconnect continents. There are two basic types of fiber optics,
1760:
1583:
1311:
1295:
1174:
555:
512:
502:
5397:
5184:. Internet Archive. Wiley. pp. See page refs highlighted at url.
4300:
How Not to Network a Nation: The Uneasy History of the Soviet Internet
3335: – time it takes a router to process the packet header
3207:
are examples of well-known network services. Network services such as
3081:. The length of the lines indicates the delay between those two nodes.
941:
to communicate with each other. These interconnections are made up of
7833:
7794:
7215:
7122:
7048:
7013:
6737:
6399:
6365:
5538:
4778:"Data Communications at the National Physical Laboratory (1965-1975)"
4042:
3734:
3462:
same level of load. The stable state with low throughput is known as
3362:
2813:
1921:
1794:
are used to transmit light from one computer/network node to another.
1745:
1713:
1330:
849:
720:
276:
6850:
5884:
5562:"Ethernet: Distributed Packet Switching for Local Computer Networks"
3626:
program, technologies such as high-speed surveillance computers and
3073:
2432:
published by the Institute of Electrical and Electronics Engineers.
2288:
1905:
Computers are very often connected to networks using wireless links.
1511:
991:
Computer networks may be classified by many criteria, including the
173:
49:
7894:
7377:
7344:
6660:"Anonymous hacks UK government sites over 'draconian surveillance'"
6493:
4007:
3866:
3861:
3765:
3619:
3353: – time for a signal to propagate through the media
3200:
3093:
3061:
3048:
2809:
2734:
2590:
2532:
2489:
2445:
2385:
2211:
2202:
2122:, cleans it of unnecessary noise and regenerates it. The signal is
2113:
2031:
1971:
uses visible or invisible light for communications. In most cases,
1901:
1838:
1730:
The transmission media (often referred to in the literature as the
1690:
1642:
1535:
1303:
1299:
1261:
981:
923:
5377:
4818:
2171:(layer 2) of the OSI model and bridge traffic between two or more
1399:
In 1979, Robert Metcalfe pursued making Ethernet an open standard.
7339:
7038:
6556:
3642:
3365:. This delay is extended by more variable levels of delay due to
3267:
3146:
3137:(BGP), forming a redundant worldwide mesh of transmission paths.
3098:
2575:
2528:
2459:(SONET) and Synchronous Digital Hierarchy (SDH) are standardized
1686:
1660:
1543:
1539:
1432:
1253:
In 1972, commercial services were first deployed on experimental
1222:
6211:
5986:. 7.1.3 Connectivity to unauthenticated systems. February 2020.
5600:
5559:
5248:
Proceedings of the 2009 workshop on Re-architecting the internet
3946: – International standard for electrical and optical cables
6835:
6033:. 4.2.5 Interaction with other IEEE 802 layers. February 2021.
4003:
Military Communications: From Ancient Times to the 21st Century
3854:
3540:
is "the ability to provide and maintain an acceptable level of
3488:
3386:
3196:
2258:
1524:
which is the map of logical interconnections of network hosts.
1390:
5238:
4856:"The National Physical Laboratory Data Communications Network"
4325:"The beginnings of packet switching: some underlying concepts"
2184:
except the source, and discovers the location from the reply.
2175:
to form a single local network. Both are devices that forward
1393:, a token-passing network first used to share storage devices.
7288:
6272:
5146:(Technical report). Burlington, MA: Bolt, Beranek and Newman.
5136:
5002:
Prominently cites Baran and Davies as sources of inspiration.
4234:
3718:
3710:
3512:
3381:
The parameters that affect performance typically can include
3259:
3184:
are applications hosted by servers on a computer network, to
3121:, video transfer, and a broad range of information services.
2942:(WANs), metro, regional, national and transoceanic networks.
2833:
2232:
1960:
1811:
1787:
1083:
1075:
5522:
Cerf, Vinton; dalal, Yogen; Sunshine, Carl (December 1974).
4554:"NIHF Inductee Donald Davies, Who Invented Packet Switching"
4103:
The Compatible Time-Sharing System A Programmer's Guide]
3618:, recognize and monitor threats, and prevent or investigate
1602:: each node is connected to every other node in the network.
6625:
5042:
4719:. National Museum of Science and Industry. pp. 132–4.
4270:"Kitov Anatoliy Ivanovich. Russian Virtual Computer Museum"
3730:
3515:
3341: – time the packet spends in routing queues
3262:
may refer to consumed bandwidth, corresponding to achieved
2836:
2685:
2409:
2374:
2370:
2328:
2207:
2118:
A repeater is an electronic device that receives a network
1814:
1768:
1613:
1445:
1379:
1375:
1310:
and colleagues at the University of Hawaii. Metcalfe, with
1138:
6806:
Computer Networking with Internet Protocols and Technology
6792:
Shelly, Gary, et al. "Discovering Computers" 2003 Edition.
5790:
4853:
1736:) used to link devices to form a computer network include
1194:. Davies' hierarchical network design included high-speed
1170:
that implemented computer control in the switching fabric.
7324:
6186:
4915:"The real story of how the Internet became so vulnerable"
4529:"NIHF Inductee Paul Baran, Who Invented Packet Switching"
2805:
2601:
techniques enable the use of multiple alternative paths.
1572:, where each wireless client associates with the central
1287:, the first international heterogeneous computer network.
1043:
5099:
3604:
authorization from a court or other independent agency.
3323:
for a bit of data to travel across the network from one
2141:
An Ethernet repeater with multiple ports is known as an
1250:
remains critical to the operation of the Internet today.
6031:
IEEE STD 802.11-2020 (Revision of IEEE STD 802.11-2016)
5525:
Specification of Internet Transmission Control Protocol
5105:
3529:
addresses the subject of congestion control in detail.
1337:
published their seminal 1974 paper on internetworking,
1046:, and use of email and instant messaging applications.
6694:"Hacktivists in the frontline battle for the internet"
6596:
6594:
6212:"IEEE P802.3ba 40Gb/s and 100Gb/s Ethernet Task Force"
5241:"HAIR: Hierarchical architecture for internet routing"
6286:
Mansfield-Devine, Steve (December 2009). "Darknets".
6245:
IEEE 802.20 — Mobile Broadband Wireless Access (MBWA)
4239:
How the Web was Born: The Story of the World Wide Web
3109:. The Internet utilizes copper communications and an
2400:) deals with the routing of Ethernet packets using a
2339:(the Wi-Fi protocol). This stack is used between the
3451:
lead either to only a small increase in the network
2850:, limited geographic range, and lack of reliance on
6591:
6447:
3583:consists of provisions and policies adopted by the
3455:or to a potential reduction in network throughput.
1144:In 1960, the commercial airline reservation system
74:. Unsourced material may be challenged and removed.
6602:"Is the U.S. Turning Into a Surveillance Society?"
6075:"Design Principles for DSL-Based Access Solutions"
5662:
5478:"A Protocol for Packet Network Intercommunication"
4985:
4236:
3622:activity. With the advent of programs such as the
2206:A typical home or small office router showing the
1054:Computer networking may be considered a branch of
5816:CompTIA Network+ exam guide : (Exam N10-005)
5521:
4828:. ACM Symposium on Operating Systems Principles.
4619:"Principles and lessons in packet communications"
3632:Communications Assistance For Law Enforcement Act
2098:Institute of Electrical and Electronics Engineers
1339:A Protocol for Packet Network Intercommunication.
8399:
6657:
6285:
5656:
5654:
5560:Robert M. Metcalfe; David R. Boggs (July 1976).
3315:is a design and performance characteristic of a
6390:Domain names – Implementation and Specification
5881:"Bergen Linux User Group's CPIP Implementation"
4069:AN/FSQ-7: the computer that shaped the Cold War
3610:Surveillance is very useful to governments and
1374:in Europe, North America and Japan began using
824:
6626:Jay Stanley; Barry Steinhardt (January 2003).
6619:
6179:"New global standard for fully networked home"
5898:
4872:
4775:
2257:technology and cable television systems using
1637:that of the underlying one. For example, many
30:"Datacom" redirects here. For other uses, see
7417:Note: This template roughly follows the 2012
7393:
6866:
6420:
6315:"The Darknet: A Digital Copyright Revolution"
5809:
5807:
5651:
5215:. Internet Archive. Wiley. pp. 110–111.
4986:Norberg, Arthur L.; O'Neill, Judy E. (1996).
4178:"Reminiscences on the Theory of Time-Sharing"
3165:Darknets are distinct from other distributed
2985:
2759:
2475:
1216:National Physical Laboratory (United Kingdom)
953:methods that may be arranged in a variety of
899:
791:
6724:
5904:
5789:. Carnegie Mellon University. Archived from
5712:
5639:: CS1 maint: multiple names: authors list (
4854:Scantlebury, R. A.; Wilkinson, P.T. (1974).
4030:
2945:
2549:Digital Enhanced Cordless Telecommunications
2092:In Ethernet networks, each NIC has a unique
1829:) to create a high-speed local area network.
1302:, a networking system that was based on the
1146:semi-automatic business research environment
960:The nodes of a computer network can include
926:sharing resources located on or provided by
6715:
6474:: CS1 maint: numeric names: authors list (
6386:
5747:D. Andersen; H. Balakrishnan; M. Kaashoek;
4875:"Internet pioneers airbrushed from history"
4207:"Computer - Time-sharing and minicomputers"
2331:(the World Wide Web protocol) running over
1666:Another example of an overlay network is a
7400:
7386:
6873:
6859:
6720:
6718:
6688:
6147:
5804:
5643:) CS1 maint: numeric names: authors list (
5013:A History of the ARPANET: The First Decade
4653:
4149:"Computer Pioneers - Christopher Strachey"
3709:Examples of end-to-end encryption include
3158:) — using non-standard protocols and
2997:
2766:
2752:
2545:Universal Mobile Telecommunications System
2360:
2283:
2000:. It was implemented in real life in 2001.
1378:in the late 1970s and interconnected with
972:, or other specialized or general-purpose
906:
892:
798:
784:
6736:
6398:
6364:
5956:
5950:
5605:The Unpredictable Certainty: White Papers
5577:
5537:
5160:Packet and circuit-switched data networks
4662:"6.1 The Communications Subnet: BBN 1969"
4616:
3099:Advanced Research Projects Agency Network
2484:and encodes data into small, fixed-sized
1546:. This is still a common topology on the
134:Learn how and when to remove this message
5846:
5660:
5475:
5456:"Oral History of Robert (Bob) W. Taylor"
5418:
5383:
5290:
5036:
4742:
4580:"On Distributed Communications Networks"
4434:. Simon and Schuster. pp. 237–246.
4427:
3999:
3678:
3435:. Typical effects of congestion include
3072:
2795:
2566:
2295:
2287:
2201:
2080:A network interface controller (NIC) is
2067:
1900:
1856:
1853:, designed for use in various scenarios.
1786:
1623:
1558:links instead, forming a star or a tree.
1510:
1431:
1406:, Bob Garner, Roy Ogus, and Yogen Dalal.
1115:UNESCO Information Processing Conference
945:technologies based on physically wired,
6821:, "Data Networks," Prentice Hall, 1992.
6427:(5th ed.). Elsevier. p. 372.
6380:
6352:
6241:"IEEE 802.20 Mission and Project Scope"
6097:
5818:(5th ed.). New York: McGraw-Hill.
5742:
5740:
5691:"Introduction to Ethernet Technologies"
5386:IEEE Annals of the History of Computing
5351:
5318:
5059:
4945:
4682:
4468:
4464:
4462:
4374:
4096:
3595:
3033:
2881:
2812:connections while technologies such as
2521:Global System for Mobile Communications
2148:
1148:(SABRE) went online with two connected
1011:mechanisms, and organizational intent.
14:
8400:
8117:Knowledge representation and reasoning
6841:IEEE Ethernet manufacturer information
6322:Richmond Journal of Law and Technology
5813:
5718:
5465:, CHM Reference number: X5059.2009: 28
5453:
5208:
5177:
5156:
5060:Roberts, Lawrence G. (November 1978).
5022:from the original on 1 December 2012.
4946:Roberts, Lawrence G. (November 1978).
4469:Roberts, Lawrence G. (November 1978).
4375:Roberts, Lawrence G. (November 1978).
4297:
4090:
4065:
4000:Sterling, Christopher H., ed. (2008).
3919:Comparison of network diagram software
3376:
3245:
3017:
2893:
2335:over IP (the Internet protocols) over
1181:independently invented the concept of
8142:Philosophy of artificial intelligence
7381:
6880:
6854:
6725:Rosen, E.; Rekhter, Y. (March 1999).
6424:Computer Networks: A Systems Approach
5212:Computer networks and their protocols
5181:Computer networks and their protocols
5053:
4771:
4769:
4712:
4577:
4322:
3548:and challenges to normal operation."
3532:
3418:
2823:
2541:Enhanced Data Rates for GSM Evolution
2514:
2351:Rate Based Satellite Control Protocol
2107:
2057:
1221:In 1969, the first four nodes of the
7461:Energy consumption (Green computing)
7407:
6490:"Telecommunications Magazine Online"
6421:Peterson, L.L.; Davie, B.S. (2011).
6312:
6306:
6122:
5737:
4459:
4243:. Oxford University Press. pp.
3828:
2961:
2861:
2782:
2245:by the digital signal to produce an
2167:Bridges and switches operate at the
1755:that uses copper and fiber media in
1590:(FDDI), made use of such a topology.
1345:, and Carl Sunshine wrote the first
72:adding citations to reliable sources
43:
8147:Distributed artificial intelligence
7419:ACM Computing Classification System
6846:A computer networking acronym guide
5759:Association for Computing Machinery
5485:IEEE Transactions on Communications
5352:Bennett, Richard (September 2009).
5202:
5062:"The evolution of packet switching"
4979:
4948:"The Evolution of Packet Switching"
4939:
4907:
4676:
4584:IEEE Transactions on Communications
4556:. National Inventors Hall of Fame.
4531:. National Inventors Hall of Fame.
4471:"The evolution of packet switching"
4377:"The evolution of packet switching"
4368:
4316:
4276:. Translated by Alexander Nitusov.
3575:
3556:Computer networks are also used by
3233:Dynamic Host Configuration Protocol
3127:Internet Assigned Numbers Authority
3107:United States Department of Defense
2912:
2616:
2557:Integrated Digital Enhanced Network
2492:that use variable-sized packets or
2355:
1500:
1361:as a shorthand for internetworking.
1141:economy management network project.
24:
7652:Integrated development environment
6786:
6633:. American Civil Liberties Union.
6604:. American Civil Liberties Union.
6535:. ResiliNets Research Initiative.
6072:
5469:
5447:
5330:. pp. 171–185. Archived from
5171:
5150:
4812:
4782:Annals of the History of Computing
4766:
4706:
4659:
4298:Peters, Benjamin (25 March 2016).
4267:
3176:
2094:Media Access Control (MAC) address
2084:that connects the computer to the
1771:signals as a transmission medium.
1681:guarantees achieve higher-quality
1619:
1364:In July 1976, Robert Metcalfe and
1007:, the network size, the topology,
820:
25:
8419:
8127:Automated planning and scheduling
7657:Software configuration management
6825:
6448:ITU-D Study Group 2 (June 2006).
6387:Mockapetris, P. (November 1987).
6216:IEEE 802.3 ETHERNET WORKING GROUP
5293:"The Origins of Packet Switching"
4361:from the original on 2022-10-10.
4066:Ulmann, Bernd (August 19, 2014).
4038:A New History of Modern Computing
1427:
1283:(UCL), connecting the ARPANET to
1166:introduced the first widely used
1072:Semi-Automatic Ground Environment
8381:
8371:
8362:
8361:
6977:Object-oriented operating system
6762: This article incorporates
6757:
6451:Teletraffic Engineering Handbook
6125:Nanoscale Communication Networks
6102:. Boston, London: Artech House.
5454:Taylor, Bob (October 11, 2008),
5106:F.E. Froehlich, A. Kent (1990).
3892:Over the Internet, there can be
3301:
3238:Services are usually based on a
2858:, standardized by IEEE in 2010.
2634:
2015:
2004:The last two cases have a large
1968:Free-space optical communication
1719:
1588:Fiber Distributed Data Interface
1490:and waits until a link is free.
172:
48:
8372:
7775:Computational complexity theory
6775:General Services Administration
6704:from the original on 2018-03-14
6682:
6658:Emil Protalinski (2012-04-07).
6651:
6640:from the original on 2022-10-09
6608:from the original on 2017-03-14
6550:
6539:from the original on 2020-11-06
6525:
6500:
6482:
6441:
6414:
6346:
6335:from the original on 2012-04-15
6279:
6257:
6233:
6222:from the original on 2011-11-20
6204:
6171:
6160:from the original on 2023-02-04
6141:
6116:
6091:
6066:
6055:from the original on 2022-05-17
6019:
6008:from the original on 2023-02-04
5972:
5939:from the original on 2008-04-08
5921:
5883:. Blug.linux.no. Archived from
5873:
5840:
5775:
5765:from the original on 2011-11-24
5701:from the original on 2018-04-10
5683:
5622:from the original on 2023-02-04
5594:
5553:
5515:
5463:Computer History Museum Archive
5412:
5345:
5312:
5284:
5232:
5130:
5030:
5005:
4893:from the original on 2020-01-01
4866:
4847:
4835:from the original on 2022-10-10
4776:Campbell-Kelly, Martin (1987).
4736:
4610:
4571:
4560:from the original on 2022-02-12
4546:
4535:from the original on 2022-02-12
4521:
4507:from the original on 2023-02-04
4448:from the original on 2023-02-04
4421:
4291:
4280:from the original on 2023-02-04
4217:from the original on 2015-01-02
4159:from the original on 2019-05-15
4126:from the original on 2012-05-27
3630:software, and laws such as the
2820:typically form a wireless PAN.
2604:Routing can be contrasted with
2435:
1246:in the late 1970s with student
1101:filed a patent application for
1036:application and storage servers
1014:Computer networks support many
59:needs additional citations for
7559:Network performance evaluation
6987:Supercomputer operating system
6492:. January 2003. Archived from
4860:Proceedings of the 2nd ICCC 74
4261:
4228:
4199:
4170:
4141:
4059:
4024:
3993:
3655:American Civil Liberties Union
3651:Electronic Frontier Foundation
2507:ATM still plays a role in the
2457:Synchronous optical networking
1882:undersea communications cables
1157:Intergalactic Computer Network
1119:Compatible Time-Sharing System
1082:. It was the first commercial
13:
1:
7930:Multimedia information system
7915:Geographic information system
7905:Enterprise information system
7494:Computer systems organization
6356:Simple Mail Transfer Protocol
6300:10.1016/S1361-3723(09)70150-2
6288:Computer Fraud & Security
6150:"personal area network (PAN)"
5669:. O'Reilly & Associates.
5665:Ethernet The Definitive Guide
5661:Spurgeon, Charles E. (2000).
5297:Computer Resurrection Issue 5
5209:Davies, Donald Watts (1979).
5178:Davies, Donald Watts (1979).
4873:Guardian Staff (2013-06-25).
4749:A Brief History of the Future
4689:. Stripe Press. p. 286.
4683:Waldrop, M. Mitchell (2018).
3986:
3791:. E2EE also does not address
3696:application service providers
3292:bandwidth allocation protocol
2581:In packet-switched networks,
2028:network interface controllers
1763:. Wireless LAN standards use
1685:. Previous proposals such as
1347:Transmission Control Protocol
1127:Dartmouth Time Sharing System
8289:Computational social science
7877:Theoretical computer science
7690:Software development process
7466:Electronic design automation
7451:Very Large Scale Integration
6962:Just enough operating system
6947:Distributed operating system
6567:10.1007/978-3-540-30176-9_41
6353:Klensin, J. (October 2008).
6189:. 2008-12-12. Archived from
6039:10.1109/IEEESTD.2021.9363693
5992:10.1109/IEEESTD.2020.9018454
5608:. National Academies Press.
5421:IEEE Communications Magazine
4332:IEEE Communications Magazine
3503:in devices such as routers.
3361:a packet serially through a
3296:dynamic bandwidth allocation
3250:
3219:(people remember names like
2842:A LAN can be connected to a
2525:General Packet Radio Service
2451:
2264:
2064:Network interface controller
1988:was a humorous April fool's
1410:factor to its continued use.
1306:, developed in the 1960s by
7:
8112:Natural language processing
7900:Information storage systems
7075:User space and kernel space
6508:"State Transition Diagrams"
5847:A. Hooke (September 2000),
5476:Cerf, V.; Kahn, R. (1974).
3965:Network planning and design
3911:
3624:Total Information Awareness
3551:
3495:and the original Ethernet,
3068:
3055:
3042:
2423:
2380:
2371:Internet Protocol Version 4
1896:
1090:in 1958. The modem allowed
1086:for computers, released by
10:
8424:
8028:Human–computer interaction
7998:Intrusion detection system
7910:Social information systems
7895:Database management system
6982:Real-time operating system
5907:"bridge – network bridges"
5754:Resilient Overlay Networks
5112:. CRC Press. p. 344.
3851:application-layer gateways
3802:
3798:
3518:home networking standard.
3405:Asynchronous Transfer Mode
3317:telecommunications network
3305:
3186:provide some functionality
3140:
2992:enterprise private network
2986:Enterprise private network
2562:
2482:time-division multiplexing
2476:Asynchronous Transfer Mode
2470:Asynchronous Transfer Mode
2440:Wireless LAN based on the
2348:
2268:
2230:
2195:
2191:
2152:
2111:
2061:
2019:
1908:
1878:wave division multiplexing
1837:cabling is used for wired
1723:
1703:Internet service providers
1504:
1105:in the United Kingdom and
1049:
36:
29:
8357:
8294:Computational engineering
8269:Computational mathematics
8246:
8193:
8155:
8102:
8064:
8026:
7968:
7885:
7831:
7793:
7738:
7675:
7608:
7572:
7529:
7493:
7426:
7415:
7317:
7254:
7200:
7178:Multilevel feedback queue
7173:Fixed-priority preemptive
7161:
7096:
7087:
7057:
7004:
6995:
6957:Hobbyist operating system
6952:Embedded operating system
6934:
6888:
6808:, Pearson Education 2004.
6533:"Definitions: Resilience"
6098:Paetsch, Michael (1993).
5719:Pelkey, James L. (2007).
5566:Communications of the ACM
5497:10.1109/TCOM.1974.1092259
5433:10.1109/MCOM.2009.4785372
5140:Arpanet Completion Report
4596:10.1109/TCOM.1964.1088883
4428:Isaacson, Walter (2014).
4344:10.1109/MCOM.2002.1018006
3647:Reporters Without Borders
3412:state transition diagrams
3223:better than numbers like
2952:metropolitan area network
2946:Metropolitan area network
2226:
2214:network cable connections
1973:line-of-sight propagation
1930:Communications satellites
1886:single-mode optical fiber
1847:electromagnetic induction
1817:technology uses existing
1744:, and free space. In the
1515:Common network topologies
1495:maximum transmission unit
1285:British academic networks
1281:University College London
1236:Bolt Beranek & Newman
976:. They are identified by
943:telecommunication network
651:Exponential random (ERGM)
318:Informational (computing)
8304:Computational healthcare
8299:Differentiable computing
8218:Graphics processing unit
7637:Domain-specific language
7506:Computational complexity
7221:General protection fault
6972:Network operating system
6926:User features comparison
4752:. Phoenix. p. 292.
4713:Yates, David M. (1997).
3805:Transport Layer Security
3785:random number generators
3570:denial-of-service attack
2718:Municipal wireless (MWN)
2537:Evolution-Data Optimized
1890:multi-mode optical fiber
1782:
1773:Power line communication
1628:A sample overlay network
1385:In 1976, John Murphy of
1022:, such as access to the
1001:communications protocols
338:Scientific collaboration
32:Datacom (disambiguation)
8279:Computational chemistry
8213:Photograph manipulation
8104:Artificial intelligence
7920:Decision support system
6967:Mobile operating system
5850:Interplanetary Internet
5256:10.1145/1658978.1658990
5081:10.1109/PROC.1978.11141
5069:Proceedings of the IEEE
4794:10.1109/MAHC.1987.10023
4635:10.1109/PROC.1978.11143
4623:Proceedings of the IEEE
4490:10.1109/PROC.1978.11141
4478:Proceedings of the IEEE
4396:10.1109/PROC.1978.11141
4384:Proceedings of the IEEE
4211:Encyclopedia Britannica
3970:Network traffic control
3929:History of the Internet
3906:communications security
3879:Border Gateway Protocol
3587:to prevent and monitor
3433:reliable communications
3135:Border Gateway Protocol
3113:backbone to enable the
3101:(ARPANET) developed by
3004:virtual private network
2998:Virtual private network
2876:digital subscriber line
2740:Interplanetary Internet
2608:in its assumption that
2367:Internet protocol suite
2361:Internet protocol suite
2284:Communication protocols
2255:digital subscriber line
1980:Interplanetary Internet
1600:Fully connected network
1527:Common topologies are:
1450:packet-switched network
1444:is a formatted unit of
1341:Later that year, Cerf,
1294:wrote a formal memo at
1202:and the essence of the
1200:communication protocols
1123:BBN Time-Sharing System
995:used to carry signals,
932:communication protocols
930:. Computers use common
767:Category:Network theory
287:Preferential attachment
8344:Educational technology
8175:Reinforcement learning
7925:Process control system
7823:Computational geometry
7813:Algorithmic efficiency
7808:Analysis of algorithms
7456:Systems on Chip (SoCs)
7070:Loadable kernel module
6770:Federal Standard 1037C
6764:public domain material
6313:Wood, Jessica (2010).
5783:"End System Multicast"
5328:Proceedings of ICCC 74
5157:Clarke, Peter (1982).
4617:Kleinrock, L. (1978).
4100:; et al. (1963).
3950:Minimum-Pairs Protocol
3939:Information revolution
3777:technical exploitation
3688:digital communications
3499:reduction in TCP, and
3325:communication endpoint
3082:
2818:infrared communication
2572:
2418:Network Access Control
2402:Spanning Tree Protocol
2306:communication protocol
2301:
2293:
2215:
2077:
1986:IP over Avian Carriers
1906:
1862:
1795:
1668:distributed hash table
1629:
1516:
1437:
1414:
1238:. In the early 1970s,
1173:Throughout the 1960s,
831:
656:Random geometric (RGG)
8314:Electronic publishing
8284:Computational biology
8274:Computational physics
8170:Unsupervised learning
8084:Distributed computing
7960:Information retrieval
7867:Mathematical analysis
7857:Mathematical software
7740:Theory of computation
7705:Software construction
7695:Requirements analysis
7573:Software organization
7501:Computer architecture
7471:Hardware acceleration
7436:Printed circuit board
7138:Process control block
7104:Computer multitasking
6942:Disk operating system
5814:Meyers, Mike (2012).
5697:. WideBand Products.
5579:10.1145/360248.360253
4035:(14 September 2021).
3839:community of interest
3684:End-to-end encryption
3679:End to end encryption
3585:network administrator
3487:in protocols such as
3290:(using, for example,
3211:(DNS) give names for
3076:
2872:cable Internet access
2802:personal area network
2796:Personal area network
2570:
2416:defines a port-based
2349:Further information:
2299:
2291:
2205:
2071:
2010:two-way communication
2006:round-trip delay time
1904:
1860:
1790:
1724:Further information:
1627:
1574:wireless access point
1514:
1505:Further information:
1435:
1422:Distributed computing
1387:Datapoint Corporation
1349:(TCP) specification,
1324:PARC Universal Packet
1264:network, directed by
830:
772:Category:Graph theory
8074:Concurrent computing
8046:Ubiquitous computing
8018:Application security
8013:Information security
7842:Discrete mathematics
7818:Randomized algorithm
7770:Computability theory
7748:Model of computation
7720:Software maintenance
7715:Software engineering
7677:Software development
7627:Programming language
7622:Programming paradigm
7539:Network architecture
7309:Virtual tape library
6901:Forensic engineering
6123:Bush, S. F. (2010).
5958:Tanenbaum, Andrew S.
4323:Baran, Paul (2002).
4153:history.computer.org
3902:consumer-to-consumer
3898:business-to-consumer
3894:business-to-business
3823:symmetric-key cipher
3601:Network surveillance
3596:Network surveillance
3477:congestion avoidance
3471:Modern networks use
3288:bandwidth allocation
3280:bandwidth throttling
3276:bandwidth management
3205:network file sharing
3034:Organizational scope
2888:storage area network
2882:Storage area network
2271:Firewall (computing)
2149:Bridges and switches
1990:Request for Comments
1372:Public data networks
1326:for internetworking.
1260:In 1973, the French
1255:public data networks
1244:hierarchical routing
1204:end-to-end principle
1099:Christopher Strachey
1088:AT&T Corporation
1060:computer engineering
68:improve this article
37:For other uses, see
8349:Document management
8339:Operations research
8264:Enterprise software
8180:Multi-task learning
8165:Supervised learning
7887:Information systems
7710:Software deployment
7667:Software repository
7521:Real-time computing
7318:Supporting concepts
7304:Virtual file system
4964:on 31 December 2018
4862:. pp. 223–228.
3664:Hepting v. AT&T
3485:exponential backoff
3465:congestive collapse
3377:Performance metrics
3319:. It specifies the
3246:Network performance
3024:global area network
3018:Global area network
2924:network performance
2900:campus area network
2894:Campus area network
2848:data transfer rates
2555:(IS-136/TDMA), and
2310:connection-oriented
2210:telephone line and
2008:, which gives slow
1710:Akamai Technologies
1674:) indexed by keys.
1357:, coining the term
1322:also developed the
993:transmission medium
970:networking hardware
576:Degree distribution
227:Community structure
18:Computer Networking
8132:Search methodology
8079:Parallel computing
8036:Interaction design
7945:Computing platform
7872:Numerical analysis
7862:Information theory
7647:Software framework
7610:Software notations
7549:Network components
7446:Integrated circuit
7241:Segmentation fault
7089:Process management
5935:. September 1996.
5905:Bradley Mitchell.
4955:IEEE Invited Paper
4578:Baran, P. (1964).
4274:computer-museum.ru
4045:. pp. 87–89.
3960:Network simulation
3887:Domain Name System
3815:Netscape Navigator
3538:Network resilience
3533:Network resilience
3521:For the Internet,
3508:quality of service
3473:congestion control
3424:Network congestion
3419:Network congestion
3367:network congestion
3345:Transmission delay
3209:Domain Name System
3131:address registries
3119:Internet of things
3111:optical networking
3083:
2940:wide area networks
2928:network congestion
2830:local area network
2824:Local area network
2713:Metropolitan (MAN)
2573:
2515:Cellular standards
2302:
2294:
2216:
2198:Router (computing)
2127:kilometers apart.
2108:Repeaters and hubs
2078:
2058:Network interfaces
1907:
1874:optical amplifiers
1863:
1825:, phone lines and
1796:
1792:Fiber-optic cables
1779:to transmit data.
1775:uses a building's
1757:local area network
1679:quality of service
1657:Address resolution
1630:
1586:networks, and the
1550:, although modern
1517:
1478:With packets, the
1438:
1212:local area network
1187:data communication
1111:J. C. R. Licklider
1064:telecommunications
962:personal computers
955:network topologies
845:Process management
832:
760:Network scientists
686:Soft configuration
83:"Computer network"
8408:Computer networks
8395:
8394:
8324:Electronic voting
8254:Quantum Computing
8247:Applied computing
8233:Image compression
8003:Hardware security
7993:Security services
7950:Digital marketing
7730:Open-source model
7642:Modeling language
7554:Network scheduler
7375:
7374:
7231:Memory protection
7202:Memory management
7196:
7195:
7188:Shortest job next
7083:
7082:
6882:Operating systems
6815:Dimitri Bertsekas
6802:William Stallings
6576:978-3-540-23659-7
6559:Applied Computing
6434:978-0-1238-5060-7
6134:978-1-60807-003-9
6109:978-0-8900-6688-1
6048:978-1-5044-7283-8
6001:978-1-5044-6440-6
5962:Computer Networks
5615:978-0-309-17414-5
5398:10.1109/85.759368
5265:978-1-60558-749-3
5222:978-0-471-99750-4
5191:978-0-471-99750-4
4997:978-0-8018-5152-0
4726:978-0-901805-94-2
4696:978-1-953953-36-0
4686:The Dream Machine
4660:Pelkey, James L.
4629:(11): 1320–1329.
4254:978-0-19-286207-5
4116:978-0-262-03008-3
4083:978-3-486-85670-5
4017:978-1-85109-737-1
3980:Network on a chip
3881:. Typically, the
3829:Views of networks
3819:root certificates
3727:instant messaging
3713:for web traffic,
3659:mass surveillance
3459:Network protocols
3351:Propagation delay
3272:bandwidth shaping
2968:wide area network
2962:Wide area network
2956:metropolitan area
2936:Internet backbone
2868:home area network
2862:Home area network
2844:wide area network
2789:nanoscale network
2783:Nanoscale network
2776:
2775:
2610:network addresses
2599:Multipath routing
2587:packet forwarding
2583:routing protocols
2466:digital telephony
2132:propagation delay
2082:computer hardware
2022:Node (networking)
1938:Cellular networks
1751:A widely adopted
1726:Data transmission
1653:telephone network
1566:switched Ethernet
1457:network addresses
1279:into practice at
1240:Leonard Kleinrock
1234:team working for
1125:in 1962, and the
1113:at the inaugural
1078:system using the
986:Internet Protocol
978:network addresses
916:
915:
855:Memory management
814:Operating systems
808:
807:
728:
727:
636:Bianconi–Barabási
530:
529:
348:Artificial neural
323:Telecommunication
144:
143:
136:
118:
16:(Redirected from
8415:
8385:
8384:
8375:
8374:
8365:
8364:
8185:Cross-validation
8157:Machine learning
8041:Social computing
8008:Network security
7803:Algorithm design
7725:Programming team
7685:Control variable
7662:Software library
7600:Software quality
7595:Operating system
7544:Network protocol
7409:Computer science
7402:
7395:
7388:
7379:
7378:
7330:Computer network
7094:
7093:
7002:
7001:
6875:
6868:
6861:
6852:
6851:
6783:
6782:
6777:. Archived from
6761:
6760:
6750:
6749:
6740:
6738:10.17487/RFC2547
6722:
6713:
6712:
6710:
6709:
6686:
6680:
6679:
6677:
6675:
6666:. Archived from
6655:
6649:
6648:
6646:
6645:
6639:
6632:
6623:
6617:
6616:
6614:
6613:
6598:
6589:
6588:
6554:
6548:
6547:
6545:
6544:
6529:
6523:
6522:
6520:
6519:
6510:. Archived from
6504:
6498:
6497:
6486:
6480:
6479:
6473:
6465:
6463:
6457:. Archived from
6456:
6445:
6439:
6438:
6418:
6412:
6411:
6402:
6400:10.17487/RFC1035
6384:
6378:
6377:
6368:
6366:10.17487/RFC5321
6350:
6344:
6343:
6341:
6340:
6334:
6319:
6310:
6304:
6303:
6283:
6277:
6276:
6271:. Archived from
6269:The Opto Project
6261:
6255:
6254:
6252:
6251:
6237:
6231:
6230:
6228:
6227:
6208:
6202:
6201:
6199:
6198:
6175:
6169:
6168:
6166:
6165:
6148:Margaret Rouse.
6145:
6139:
6138:
6127:. Artech House.
6120:
6114:
6113:
6095:
6089:
6088:
6086:
6080:. Archived from
6079:
6073:Martin, Thomas.
6070:
6064:
6063:
6061:
6060:
6023:
6017:
6016:
6014:
6013:
5976:
5970:
5969:
5964:(4th ed.).
5954:
5948:
5947:
5945:
5944:
5925:
5919:
5918:
5913:. Archived from
5902:
5896:
5895:
5893:
5892:
5877:
5871:
5870:
5869:
5868:
5862:
5855:
5844:
5838:
5837:
5811:
5802:
5801:
5799:
5798:
5787:project web site
5779:
5773:
5772:
5771:
5770:
5751:(October 2001),
5744:
5735:
5734:
5732:
5731:
5716:
5710:
5709:
5707:
5706:
5687:
5681:
5680:
5668:
5658:
5649:
5648:
5638:
5630:
5628:
5627:
5598:
5592:
5591:
5581:
5557:
5551:
5550:
5541:
5539:10.17487/RFC0675
5519:
5513:
5512:
5482:
5473:
5467:
5466:
5460:
5451:
5445:
5444:
5416:
5410:
5409:
5381:
5375:
5374:
5372:
5371:
5365:
5358:
5349:
5343:
5342:
5340:
5339:
5316:
5310:
5309:
5304:
5303:
5288:
5282:
5281:
5245:
5236:
5230:
5229:
5206:
5200:
5199:
5175:
5169:
5167:
5165:
5154:
5148:
5147:
5145:
5134:
5128:
5127:
5103:
5097:
5096:
5066:
5057:
5051:
5050:
5045:. Archived from
5034:
5028:
5027:
5017:
5009:
5003:
5001:
4983:
4977:
4976:
4971:
4969:
4963:
4957:. Archived from
4952:
4943:
4937:
4936:
4931:
4930:
4921:. Archived from
4911:
4905:
4904:
4899:
4898:
4870:
4864:
4863:
4851:
4845:
4843:
4841:
4840:
4834:
4827:
4816:
4810:
4809:
4807:high-speed lines
4788:(3/4): 221–247.
4773:
4764:
4763:
4740:
4734:
4733:
4710:
4704:
4703:
4680:
4674:
4673:
4657:
4651:
4650:
4614:
4608:
4607:
4575:
4569:
4568:
4566:
4565:
4550:
4544:
4543:
4541:
4540:
4525:
4519:
4518:
4513:
4512:
4506:
4475:
4466:
4457:
4456:
4454:
4453:
4425:
4419:
4418:
4381:
4372:
4366:
4365:
4360:
4329:
4320:
4314:
4313:
4295:
4289:
4288:
4286:
4285:
4265:
4259:
4258:
4242:
4232:
4226:
4225:
4223:
4222:
4203:
4197:
4196:
4194:
4193:
4184:. Archived from
4182:jmc.stanford.edu
4174:
4168:
4167:
4165:
4164:
4145:
4139:
4138:
4132:
4131:
4125:
4108:
4094:
4088:
4087:
4063:
4057:
4056:
4033:Ceruzzi, Paul E.
4028:
4022:
4021:
3997:
3793:traffic analysis
3581:Network Security
3576:Network security
3562:computer viruses
3558:security hackers
3398:grade of service
3333:Processing delay
3240:service protocol
3229:
3228:
3182:Network services
2919:backbone network
2913:Backbone network
2878:(DSL) provider.
2768:
2761:
2754:
2651:Near-field (NFC)
2638:
2625:Computer network
2621:
2620:
2617:Geographic scale
2356:Common protocols
2179:of data between
2173:network segments
1911:Wireless network
1851:category ratings
1738:electrical cable
1522:network topology
1507:Network topology
1501:Network topology
1484:circuit switched
1183:packet switching
1168:telephone switch
1164:Western Electric
1056:computer science
1034:, shared use of
939:interconnections
920:computer network
908:
901:
894:
823:
810:
809:
800:
793:
786:
671:Stochastic block
661:Hyperbolic (HGN)
610:
609:
473:
462:
394:
393:
302:Social influence
176:
148:
147:
139:
132:
128:
125:
119:
117:
76:
52:
44:
21:
8423:
8422:
8418:
8417:
8416:
8414:
8413:
8412:
8398:
8397:
8396:
8391:
8382:
8353:
8334:Word processing
8242:
8228:Virtual reality
8189:
8151:
8122:Computer vision
8098:
8094:Multiprocessing
8060:
8022:
7988:Security hacker
7964:
7940:Digital library
7881:
7832:Mathematics of
7827:
7789:
7765:Automata theory
7760:Formal language
7734:
7700:Software design
7671:
7604:
7590:Virtual machine
7568:
7564:Network service
7525:
7516:Embedded system
7489:
7422:
7411:
7406:
7376:
7371:
7313:
7274:Defragmentation
7259:
7250:
7236:Protection ring
7205:
7192:
7164:
7157:
7079:
7053:
6991:
6930:
6884:
6879:
6828:
6819:Robert Gallager
6789:
6787:Further reading
6767:
6758:
6756:
6754:
6753:
6723:
6716:
6707:
6705:
6687:
6683:
6673:
6671:
6656:
6652:
6643:
6641:
6637:
6630:
6624:
6620:
6611:
6609:
6600:
6599:
6592:
6577:
6555:
6551:
6542:
6540:
6531:
6530:
6526:
6517:
6515:
6506:
6505:
6501:
6488:
6487:
6483:
6467:
6466:
6461:
6454:
6446:
6442:
6435:
6419:
6415:
6385:
6381:
6351:
6347:
6338:
6336:
6332:
6317:
6311:
6307:
6284:
6280:
6263:
6262:
6258:
6249:
6247:
6239:
6238:
6234:
6225:
6223:
6210:
6209:
6205:
6196:
6194:
6177:
6176:
6172:
6163:
6161:
6146:
6142:
6135:
6121:
6117:
6110:
6096:
6092:
6084:
6077:
6071:
6067:
6058:
6056:
6049:
6025:
6024:
6020:
6011:
6009:
6002:
5978:
5977:
5973:
5955:
5951:
5942:
5940:
5929:"Define switch"
5927:
5926:
5922:
5903:
5899:
5890:
5888:
5879:
5878:
5874:
5866:
5864:
5860:
5853:
5845:
5841:
5826:
5812:
5805:
5796:
5794:
5781:
5780:
5776:
5768:
5766:
5745:
5738:
5729:
5727:
5717:
5713:
5704:
5702:
5689:
5688:
5684:
5677:
5659:
5652:
5632:
5631:
5625:
5623:
5616:
5599:
5595:
5558:
5554:
5520:
5516:
5480:
5474:
5470:
5458:
5452:
5448:
5417:
5413:
5382:
5378:
5369:
5367:
5363:
5356:
5350:
5346:
5337:
5335:
5317:
5313:
5301:
5299:
5289:
5285:
5266:
5243:
5237:
5233:
5223:
5207:
5203:
5192:
5176:
5172:
5163:
5155:
5151:
5143:
5135:
5131:
5120:
5104:
5100:
5075:(11): 1307–13.
5064:
5058:
5054:
5035:
5031:
5015:
5011:
5010:
5006:
4998:
4984:
4980:
4967:
4965:
4961:
4950:
4944:
4940:
4928:
4926:
4919:Washington Post
4913:
4912:
4908:
4896:
4894:
4871:
4867:
4852:
4848:
4838:
4836:
4832:
4825:
4817:
4813:
4774:
4767:
4760:
4741:
4737:
4727:
4711:
4707:
4697:
4681:
4677:
4658:
4654:
4615:
4611:
4576:
4572:
4563:
4561:
4552:
4551:
4547:
4538:
4536:
4527:
4526:
4522:
4510:
4508:
4504:
4484:(11): 1307–13.
4473:
4467:
4460:
4451:
4449:
4442:
4426:
4422:
4390:(11): 1307–13.
4379:
4373:
4369:
4358:
4327:
4321:
4317:
4310:
4296:
4292:
4283:
4281:
4266:
4262:
4255:
4233:
4229:
4220:
4218:
4205:
4204:
4200:
4191:
4189:
4176:
4175:
4171:
4162:
4160:
4147:
4146:
4142:
4129:
4127:
4123:
4117:
4106:
4095:
4091:
4084:
4064:
4060:
4053:
4031:Haigh, Thomas;
4029:
4025:
4018:
4010:. p. 399.
3998:
3994:
3989:
3984:
3955:Network mapping
3934:Information Age
3914:
3831:
3807:
3801:
3783:, poor quality
3762:Yahoo Messenger
3700:confidentiality
3681:
3645:groups—such as
3612:law enforcement
3598:
3578:
3554:
3544:in the face of
3535:
3481:traffic control
3421:
3379:
3310:
3304:
3253:
3248:
3226:
3225:
3179:
3177:Network service
3143:
3071:
3058:
3045:
3036:
3020:
3008:overlay network
3000:
2988:
2976:data link layer
2972:common carriers
2964:
2948:
2915:
2896:
2884:
2864:
2856:100 Gbit/s
2826:
2798:
2785:
2772:
2681:Wireless (WLAN)
2628:
2619:
2565:
2517:
2502:virtual circuit
2478:
2454:
2438:
2426:
2383:
2373:(IPv4) and for
2363:
2358:
2353:
2341:wireless router
2316:, they may use
2286:
2273:
2267:
2239:carrier signals
2235:
2229:
2200:
2194:
2169:data link layer
2161:
2153:Main articles:
2151:
2116:
2110:
2066:
2060:
2024:
2018:
1951:spread spectrum
1913:
1899:
1785:
1733:physical medium
1728:
1722:
1683:streaming media
1634:overlay network
1622:
1620:Overlay network
1548:data link layer
1509:
1503:
1461:error detection
1430:
1417:
1318:, Ed Taft, and
1308:Norman Abramson
1292:Robert Metcalfe
1277:internetworking
1052:
1009:traffic control
1005:network traffic
951:radio-frequency
949:, and wireless
912:
837:Common features
829:
821:
804:
742:
707:Boolean network
681:Maximum entropy
631:Barabási–Albert
548:
465:
454:
242:Controllability
207:Complex network
194:
181:
180:
179:
178:
177:
161:Network science
140:
129:
123:
120:
77:
75:
65:
53:
42:
35:
28:
23:
22:
15:
12:
11:
5:
8421:
8411:
8410:
8393:
8392:
8390:
8389:
8379:
8369:
8358:
8355:
8354:
8352:
8351:
8346:
8341:
8336:
8331:
8326:
8321:
8316:
8311:
8306:
8301:
8296:
8291:
8286:
8281:
8276:
8271:
8266:
8261:
8256:
8250:
8248:
8244:
8243:
8241:
8240:
8238:Solid modeling
8235:
8230:
8225:
8220:
8215:
8210:
8205:
8199:
8197:
8191:
8190:
8188:
8187:
8182:
8177:
8172:
8167:
8161:
8159:
8153:
8152:
8150:
8149:
8144:
8139:
8137:Control method
8134:
8129:
8124:
8119:
8114:
8108:
8106:
8100:
8099:
8097:
8096:
8091:
8089:Multithreading
8086:
8081:
8076:
8070:
8068:
8062:
8061:
8059:
8058:
8053:
8048:
8043:
8038:
8032:
8030:
8024:
8023:
8021:
8020:
8015:
8010:
8005:
8000:
7995:
7990:
7985:
7983:Formal methods
7980:
7974:
7972:
7966:
7965:
7963:
7962:
7957:
7955:World Wide Web
7952:
7947:
7942:
7937:
7932:
7927:
7922:
7917:
7912:
7907:
7902:
7897:
7891:
7889:
7883:
7882:
7880:
7879:
7874:
7869:
7864:
7859:
7854:
7849:
7844:
7838:
7836:
7829:
7828:
7826:
7825:
7820:
7815:
7810:
7805:
7799:
7797:
7791:
7790:
7788:
7787:
7782:
7777:
7772:
7767:
7762:
7757:
7756:
7755:
7744:
7742:
7736:
7735:
7733:
7732:
7727:
7722:
7717:
7712:
7707:
7702:
7697:
7692:
7687:
7681:
7679:
7673:
7672:
7670:
7669:
7664:
7659:
7654:
7649:
7644:
7639:
7634:
7629:
7624:
7618:
7616:
7606:
7605:
7603:
7602:
7597:
7592:
7587:
7582:
7576:
7574:
7570:
7569:
7567:
7566:
7561:
7556:
7551:
7546:
7541:
7535:
7533:
7527:
7526:
7524:
7523:
7518:
7513:
7508:
7503:
7497:
7495:
7491:
7490:
7488:
7487:
7478:
7473:
7468:
7463:
7458:
7453:
7448:
7443:
7438:
7432:
7430:
7424:
7423:
7416:
7413:
7412:
7405:
7404:
7397:
7390:
7382:
7373:
7372:
7370:
7369:
7364:
7363:
7362:
7360:User interface
7357:
7347:
7342:
7337:
7332:
7327:
7321:
7319:
7315:
7314:
7312:
7311:
7306:
7301:
7296:
7291:
7286:
7284:File attribute
7281:
7276:
7271:
7265:
7263:
7252:
7251:
7249:
7248:
7246:Virtual memory
7243:
7238:
7233:
7228:
7223:
7218:
7212:
7210:
7198:
7197:
7194:
7193:
7191:
7190:
7185:
7180:
7175:
7169:
7167:
7159:
7158:
7156:
7155:
7150:
7145:
7140:
7135:
7130:
7125:
7120:
7118:Context switch
7115:
7100:
7098:
7091:
7085:
7084:
7081:
7080:
7078:
7077:
7072:
7067:
7061:
7059:
7055:
7054:
7052:
7051:
7046:
7041:
7036:
7031:
7026:
7021:
7016:
7010:
7008:
6999:
6993:
6992:
6990:
6989:
6984:
6979:
6974:
6969:
6964:
6959:
6954:
6949:
6944:
6938:
6936:
6932:
6931:
6929:
6928:
6923:
6918:
6913:
6908:
6903:
6898:
6892:
6890:
6886:
6885:
6878:
6877:
6870:
6863:
6855:
6849:
6848:
6843:
6838:
6827:
6826:External links
6824:
6823:
6822:
6812:
6809:
6799:
6796:
6793:
6788:
6785:
6781:on 2022-01-22.
6752:
6751:
6714:
6692:(2012-04-20).
6681:
6650:
6618:
6590:
6575:
6549:
6524:
6499:
6496:on 2011-02-08.
6481:
6464:on 2007-01-11.
6440:
6433:
6413:
6379:
6345:
6305:
6278:
6275:on 2005-01-15.
6256:
6232:
6203:
6170:
6140:
6133:
6115:
6108:
6090:
6087:on 2011-07-22.
6065:
6047:
6018:
6000:
5971:
5949:
5920:
5917:on 2008-03-28.
5897:
5872:
5839:
5824:
5803:
5774:
5736:
5711:
5682:
5675:
5650:
5614:
5593:
5572:(5): 395–404.
5552:
5514:
5491:(5): 637–648.
5468:
5446:
5411:
5376:
5344:
5311:
5291:Derek Barber.
5283:
5264:
5231:
5221:
5201:
5190:
5170:
5149:
5129:
5118:
5098:
5052:
5049:on 2008-03-08.
5037:Chris Sutton.
5029:
5004:
4996:
4978:
4938:
4906:
4865:
4846:
4811:
4765:
4758:
4744:Naughton, John
4735:
4725:
4705:
4695:
4675:
4652:
4609:
4570:
4545:
4520:
4458:
4440:
4420:
4367:
4315:
4309:978-0262034180
4308:
4290:
4260:
4253:
4227:
4198:
4169:
4140:
4115:
4098:Corbató, F. J.
4089:
4082:
4058:
4052:978-0262542906
4051:
4023:
4016:
3991:
3990:
3988:
3985:
3983:
3982:
3977:
3972:
3967:
3962:
3957:
3952:
3947:
3941:
3936:
3931:
3926:
3921:
3915:
3913:
3910:
3883:human-readable
3845:technologies.
3830:
3827:
3803:Main article:
3800:
3797:
3680:
3677:
3637:However, many
3616:social control
3597:
3594:
3577:
3574:
3566:computer worms
3553:
3550:
3534:
3531:
3437:queueing delay
3429:retransmission
3420:
3417:
3391:bit error rate
3378:
3375:
3355:
3354:
3348:
3342:
3336:
3306:Main article:
3303:
3300:
3252:
3249:
3247:
3244:
3193:World Wide Web
3178:
3175:
3142:
3139:
3115:World Wide Web
3070:
3067:
3057:
3054:
3044:
3041:
3035:
3032:
3019:
3016:
2999:
2996:
2987:
2984:
2963:
2960:
2947:
2944:
2914:
2911:
2895:
2892:
2883:
2880:
2863:
2860:
2825:
2822:
2797:
2794:
2784:
2781:
2774:
2773:
2771:
2770:
2763:
2756:
2748:
2745:
2744:
2743:
2742:
2737:
2732:
2727:
2722:
2721:
2720:
2710:
2705:
2700:
2695:
2694:
2693:
2688:
2686:Virtual (VLAN)
2683:
2678:
2668:
2663:
2661:Personal (PAN)
2658:
2653:
2648:
2640:
2639:
2631:
2630:
2618:
2615:
2595:routing tables
2564:
2561:
2516:
2513:
2477:
2474:
2472:(ATM) frames.
2453:
2450:
2437:
2434:
2425:
2422:
2382:
2379:
2362:
2359:
2357:
2354:
2325:protocol stack
2314:connectionless
2285:
2282:
2269:Main article:
2266:
2263:
2231:Main article:
2228:
2225:
2196:Main article:
2193:
2190:
2159:Network switch
2155:Network bridge
2150:
2147:
2112:Main article:
2109:
2106:
2062:Main article:
2059:
2056:
2050:, modems, and
2020:Main article:
2017:
2014:
2002:
2001:
1983:
1976:
1964:
1946:
1934:
1926:
1909:Main article:
1898:
1895:
1894:
1893:
1855:
1854:
1830:
1809:
1784:
1781:
1721:
1718:
1621:
1618:
1610:
1609:
1603:
1597:
1591:
1577:
1559:
1556:point-to-point
1552:physical layer
1502:
1499:
1465:packet headers
1442:network packet
1436:Network Packet
1429:
1428:Network packet
1426:
1416:
1413:
1412:
1411:
1407:
1400:
1397:
1394:
1383:
1369:
1362:
1327:
1320:Butler Lampson
1288:
1273:Peter Kirstein
1269:
1258:
1251:
1219:
1171:
1160:
1153:
1142:
1130:
1095:
1080:Bell 101 modem
1051:
1048:
1024:World Wide Web
914:
913:
911:
910:
903:
896:
888:
885:
884:
883:
882:
877:
872:
867:
865:Device drivers
862:
857:
852:
847:
839:
838:
834:
833:
817:
816:
806:
805:
803:
802:
795:
788:
780:
777:
776:
775:
774:
769:
763:
762:
757:
752:
744:
743:
741:
740:
737:
733:
730:
729:
726:
725:
724:
723:
714:
709:
701:
700:
696:
695:
694:
693:
688:
683:
678:
673:
668:
663:
658:
653:
648:
646:Watts–Strogatz
643:
638:
633:
628:
623:
615:
614:
606:
605:
601:
600:
599:
598:
593:
588:
583:
578:
573:
568:
563:
558:
550:
549:
547:
546:
541:
535:
532:
531:
528:
527:
526:
525:
520:
515:
510:
505:
500:
495:
490:
482:
481:
477:
476:
475:
474:
467:Incidence list
463:
456:Adjacency list
452:
447:
442:
437:
432:
427:
425:Data structure
422:
417:
412:
407:
399:
398:
390:
389:
383:
382:
381:
380:
375:
370:
365:
360:
355:
353:Interdependent
350:
345:
340:
335:
330:
325:
320:
312:
311:
307:
306:
305:
304:
299:
297:Network effect
294:
292:Balance theory
289:
284:
279:
274:
269:
264:
259:
254:
252:Social capital
249:
244:
239:
234:
229:
224:
219:
214:
209:
204:
196:
195:
193:
192:
186:
183:
182:
171:
170:
169:
168:
167:
164:
163:
157:
156:
142:
141:
56:
54:
47:
26:
9:
6:
4:
3:
2:
8420:
8409:
8406:
8405:
8403:
8388:
8380:
8378:
8370:
8368:
8360:
8359:
8356:
8350:
8347:
8345:
8342:
8340:
8337:
8335:
8332:
8330:
8327:
8325:
8322:
8320:
8317:
8315:
8312:
8310:
8307:
8305:
8302:
8300:
8297:
8295:
8292:
8290:
8287:
8285:
8282:
8280:
8277:
8275:
8272:
8270:
8267:
8265:
8262:
8260:
8257:
8255:
8252:
8251:
8249:
8245:
8239:
8236:
8234:
8231:
8229:
8226:
8224:
8223:Mixed reality
8221:
8219:
8216:
8214:
8211:
8209:
8206:
8204:
8201:
8200:
8198:
8196:
8192:
8186:
8183:
8181:
8178:
8176:
8173:
8171:
8168:
8166:
8163:
8162:
8160:
8158:
8154:
8148:
8145:
8143:
8140:
8138:
8135:
8133:
8130:
8128:
8125:
8123:
8120:
8118:
8115:
8113:
8110:
8109:
8107:
8105:
8101:
8095:
8092:
8090:
8087:
8085:
8082:
8080:
8077:
8075:
8072:
8071:
8069:
8067:
8063:
8057:
8056:Accessibility
8054:
8052:
8051:Visualization
8049:
8047:
8044:
8042:
8039:
8037:
8034:
8033:
8031:
8029:
8025:
8019:
8016:
8014:
8011:
8009:
8006:
8004:
8001:
7999:
7996:
7994:
7991:
7989:
7986:
7984:
7981:
7979:
7976:
7975:
7973:
7971:
7967:
7961:
7958:
7956:
7953:
7951:
7948:
7946:
7943:
7941:
7938:
7936:
7933:
7931:
7928:
7926:
7923:
7921:
7918:
7916:
7913:
7911:
7908:
7906:
7903:
7901:
7898:
7896:
7893:
7892:
7890:
7888:
7884:
7878:
7875:
7873:
7870:
7868:
7865:
7863:
7860:
7858:
7855:
7853:
7850:
7848:
7845:
7843:
7840:
7839:
7837:
7835:
7830:
7824:
7821:
7819:
7816:
7814:
7811:
7809:
7806:
7804:
7801:
7800:
7798:
7796:
7792:
7786:
7783:
7781:
7778:
7776:
7773:
7771:
7768:
7766:
7763:
7761:
7758:
7754:
7751:
7750:
7749:
7746:
7745:
7743:
7741:
7737:
7731:
7728:
7726:
7723:
7721:
7718:
7716:
7713:
7711:
7708:
7706:
7703:
7701:
7698:
7696:
7693:
7691:
7688:
7686:
7683:
7682:
7680:
7678:
7674:
7668:
7665:
7663:
7660:
7658:
7655:
7653:
7650:
7648:
7645:
7643:
7640:
7638:
7635:
7633:
7630:
7628:
7625:
7623:
7620:
7619:
7617:
7615:
7611:
7607:
7601:
7598:
7596:
7593:
7591:
7588:
7586:
7583:
7581:
7578:
7577:
7575:
7571:
7565:
7562:
7560:
7557:
7555:
7552:
7550:
7547:
7545:
7542:
7540:
7537:
7536:
7534:
7532:
7528:
7522:
7519:
7517:
7514:
7512:
7511:Dependability
7509:
7507:
7504:
7502:
7499:
7498:
7496:
7492:
7486:
7482:
7479:
7477:
7474:
7472:
7469:
7467:
7464:
7462:
7459:
7457:
7454:
7452:
7449:
7447:
7444:
7442:
7439:
7437:
7434:
7433:
7431:
7429:
7425:
7420:
7414:
7410:
7403:
7398:
7396:
7391:
7389:
7384:
7383:
7380:
7368:
7365:
7361:
7358:
7356:
7353:
7352:
7351:
7348:
7346:
7343:
7341:
7338:
7336:
7333:
7331:
7328:
7326:
7323:
7322:
7320:
7316:
7310:
7307:
7305:
7302:
7300:
7297:
7295:
7292:
7290:
7287:
7285:
7282:
7280:
7277:
7275:
7272:
7270:
7267:
7266:
7264:
7262:
7257:
7253:
7247:
7244:
7242:
7239:
7237:
7234:
7232:
7229:
7227:
7226:Memory paging
7224:
7222:
7219:
7217:
7214:
7213:
7211:
7208:
7203:
7199:
7189:
7186:
7184:
7181:
7179:
7176:
7174:
7171:
7170:
7168:
7166:
7160:
7154:
7151:
7149:
7146:
7144:
7141:
7139:
7136:
7134:
7131:
7129:
7126:
7124:
7121:
7119:
7116:
7113:
7109:
7105:
7102:
7101:
7099:
7095:
7092:
7090:
7086:
7076:
7073:
7071:
7068:
7066:
7065:Device driver
7063:
7062:
7060:
7056:
7050:
7047:
7045:
7042:
7040:
7037:
7035:
7032:
7030:
7027:
7025:
7022:
7020:
7017:
7015:
7012:
7011:
7009:
7007:
7006:Architectures
7003:
7000:
6998:
6994:
6988:
6985:
6983:
6980:
6978:
6975:
6973:
6970:
6968:
6965:
6963:
6960:
6958:
6955:
6953:
6950:
6948:
6945:
6943:
6940:
6939:
6937:
6933:
6927:
6924:
6922:
6919:
6917:
6914:
6912:
6909:
6907:
6904:
6902:
6899:
6897:
6894:
6893:
6891:
6887:
6883:
6876:
6871:
6869:
6864:
6862:
6857:
6856:
6853:
6847:
6844:
6842:
6839:
6837:
6833:
6830:
6829:
6820:
6816:
6813:
6810:
6807:
6803:
6800:
6797:
6794:
6791:
6790:
6784:
6780:
6776:
6772:
6771:
6765:
6747:
6744:
6739:
6734:
6730:
6729:
6728:BGP/MPLS VPNs
6721:
6719:
6703:
6699:
6695:
6691:
6685:
6670:on 2013-04-03
6669:
6665:
6661:
6654:
6636:
6629:
6622:
6607:
6603:
6597:
6595:
6586:
6582:
6578:
6572:
6568:
6564:
6560:
6553:
6538:
6534:
6528:
6514:on 2003-10-15
6513:
6509:
6503:
6495:
6491:
6485:
6477:
6471:
6460:
6453:
6452:
6444:
6436:
6430:
6426:
6425:
6417:
6409:
6406:
6401:
6396:
6392:
6391:
6383:
6375:
6372:
6367:
6362:
6358:
6357:
6349:
6331:
6327:
6323:
6316:
6309:
6301:
6297:
6293:
6289:
6282:
6274:
6270:
6266:
6260:
6246:
6242:
6236:
6221:
6217:
6213:
6207:
6193:on 2009-02-21
6192:
6188:
6184:
6183:ITU-T Newslog
6180:
6174:
6159:
6155:
6151:
6144:
6136:
6130:
6126:
6119:
6111:
6105:
6101:
6094:
6083:
6076:
6069:
6054:
6050:
6044:
6040:
6036:
6032:
6028:
6022:
6007:
6003:
5997:
5993:
5989:
5985:
5981:
5975:
5967:
5966:Prentice Hall
5963:
5959:
5953:
5938:
5934:
5930:
5924:
5916:
5912:
5908:
5901:
5887:on 2014-02-15
5886:
5882:
5876:
5863:on 2012-01-13
5859:
5852:
5851:
5843:
5835:
5831:
5827:
5825:9780071789226
5821:
5817:
5810:
5808:
5793:on 2005-02-21
5792:
5788:
5784:
5778:
5764:
5760:
5756:
5755:
5750:
5743:
5741:
5726:
5722:
5721:"Yogen Dalal"
5715:
5700:
5696:
5695:www.wband.com
5692:
5686:
5678:
5676:1-56592-660-9
5672:
5667:
5666:
5657:
5655:
5646:
5642:
5636:
5621:
5617:
5611:
5607:
5606:
5597:
5589:
5585:
5580:
5575:
5571:
5567:
5563:
5556:
5548:
5545:
5540:
5535:
5531:
5527:
5526:
5518:
5511:
5506:
5502:
5498:
5494:
5490:
5486:
5479:
5472:
5464:
5457:
5450:
5442:
5438:
5434:
5430:
5426:
5422:
5415:
5407:
5403:
5399:
5395:
5391:
5387:
5380:
5366:on 2019-08-29
5362:
5355:
5348:
5334:on 2013-10-20
5333:
5329:
5325:
5321:
5315:
5308:
5298:
5294:
5287:
5280:
5275:
5271:
5267:
5261:
5257:
5253:
5249:
5242:
5235:
5228:
5224:
5218:
5214:
5213:
5205:
5198:
5193:
5187:
5183:
5182:
5174:
5162:
5161:
5153:
5142:
5141:
5133:
5126:
5121:
5115:
5111:
5110:
5102:
5095:
5090:
5086:
5082:
5078:
5074:
5070:
5063:
5056:
5048:
5044:
5040:
5033:
5026:
5021:
5014:
5008:
4999:
4993:
4989:
4982:
4975:
4968:September 10,
4960:
4956:
4949:
4942:
4935:
4925:on 2015-05-30
4924:
4920:
4916:
4910:
4903:
4892:
4888:
4884:
4880:
4876:
4869:
4861:
4857:
4850:
4831:
4824:
4823:
4815:
4808:
4803:
4799:
4795:
4791:
4787:
4783:
4779:
4772:
4770:
4761:
4759:9780753810934
4755:
4751:
4750:
4745:
4739:
4732:
4728:
4722:
4718:
4717:
4709:
4702:
4698:
4692:
4688:
4687:
4679:
4672:
4667:
4663:
4656:
4649:
4644:
4640:
4636:
4632:
4628:
4624:
4620:
4613:
4605:
4601:
4597:
4593:
4589:
4585:
4581:
4574:
4559:
4555:
4549:
4534:
4530:
4524:
4517:
4503:
4499:
4495:
4491:
4487:
4483:
4479:
4472:
4465:
4463:
4447:
4443:
4441:9781476708690
4437:
4433:
4432:
4424:
4417:
4413:
4409:
4405:
4401:
4397:
4393:
4389:
4385:
4378:
4371:
4364:
4357:
4353:
4349:
4345:
4341:
4337:
4333:
4326:
4319:
4311:
4305:
4302:. MIT Press.
4301:
4294:
4279:
4275:
4271:
4264:
4256:
4250:
4246:
4241:
4240:
4231:
4216:
4212:
4208:
4202:
4188:on 2020-04-28
4187:
4183:
4179:
4173:
4158:
4154:
4150:
4144:
4137:
4122:
4118:
4112:
4109:. MIT Press.
4105:
4104:
4099:
4093:
4085:
4079:
4075:
4071:
4070:
4062:
4054:
4048:
4044:
4040:
4039:
4034:
4027:
4019:
4013:
4009:
4005:
4004:
3996:
3992:
3981:
3978:
3976:
3973:
3971:
3968:
3966:
3963:
3961:
3958:
3956:
3953:
3951:
3948:
3945:
3944:ISO/IEC 11801
3942:
3940:
3937:
3935:
3932:
3930:
3927:
3925:
3922:
3920:
3917:
3916:
3909:
3907:
3903:
3899:
3895:
3890:
3888:
3884:
3880:
3876:
3870:
3868:
3863:
3858:
3856:
3852:
3846:
3844:
3840:
3836:
3826:
3824:
3820:
3816:
3812:
3806:
3796:
3794:
3790:
3786:
3782:
3778:
3773:
3771:
3767:
3763:
3759:
3755:
3751:
3747:
3742:
3740:
3736:
3732:
3728:
3724:
3720:
3716:
3712:
3707:
3705:
3701:
3697:
3693:
3689:
3685:
3676:
3674:
3670:
3666:
3665:
3660:
3656:
3652:
3648:
3644:
3640:
3635:
3633:
3629:
3625:
3621:
3617:
3613:
3608:
3605:
3602:
3593:
3590:
3586:
3582:
3573:
3571:
3567:
3563:
3559:
3549:
3547:
3543:
3539:
3530:
3528:
3524:
3519:
3517:
3514:
3509:
3504:
3502:
3501:fair queueing
3498:
3494:
3490:
3486:
3482:
3478:
3474:
3469:
3467:
3466:
3460:
3456:
3454:
3450:
3446:
3442:
3438:
3434:
3430:
3425:
3416:
3413:
3408:
3406:
3401:
3399:
3394:
3393:and latency.
3392:
3388:
3384:
3374:
3372:
3368:
3364:
3360:
3352:
3349:
3346:
3343:
3340:
3339:Queuing delay
3337:
3334:
3331:
3330:
3329:
3326:
3322:
3318:
3314:
3313:Network delay
3309:
3308:Network delay
3302:Network delay
3299:
3297:
3293:
3289:
3285:
3284:bandwidth cap
3281:
3277:
3273:
3269:
3265:
3261:
3257:
3243:
3241:
3236:
3234:
3230:
3227:210.121.67.18
3222:
3218:
3217:MAC addresses
3214:
3210:
3206:
3202:
3198:
3194:
3189:
3187:
3183:
3174:
3172:
3168:
3163:
3161:
3157:
3153:
3148:
3138:
3136:
3132:
3128:
3122:
3120:
3116:
3112:
3108:
3104:
3100:
3095:
3090:
3088:
3080:
3075:
3066:
3063:
3053:
3050:
3040:
3031:
3029:
3028:wireless LANs
3025:
3015:
3012:
3009:
3005:
2995:
2993:
2983:
2981:
2980:network layer
2977:
2973:
2969:
2959:
2957:
2953:
2943:
2941:
2937:
2931:
2929:
2925:
2920:
2910:
2907:
2905:
2901:
2891:
2889:
2879:
2877:
2873:
2869:
2859:
2857:
2853:
2849:
2845:
2840:
2838:
2835:
2831:
2821:
2819:
2815:
2811:
2807:
2803:
2793:
2790:
2780:
2769:
2764:
2762:
2757:
2755:
2750:
2749:
2747:
2746:
2741:
2738:
2736:
2733:
2731:
2728:
2726:
2723:
2719:
2716:
2715:
2714:
2711:
2709:
2706:
2704:
2701:
2699:
2696:
2692:
2689:
2687:
2684:
2682:
2679:
2677:
2676:Storage (SAN)
2674:
2673:
2672:
2669:
2667:
2664:
2662:
2659:
2657:
2654:
2652:
2649:
2647:
2644:
2643:
2642:
2641:
2637:
2633:
2632:
2626:
2623:
2622:
2614:
2611:
2607:
2602:
2600:
2596:
2592:
2588:
2584:
2579:
2577:
2569:
2560:
2558:
2554:
2550:
2546:
2542:
2538:
2534:
2530:
2526:
2522:
2512:
2510:
2505:
2503:
2499:
2495:
2491:
2487:
2483:
2473:
2471:
2467:
2462:
2458:
2449:
2447:
2443:
2433:
2431:
2421:
2419:
2415:
2411:
2407:
2403:
2399:
2395:
2392:For example,
2390:
2387:
2378:
2376:
2372:
2368:
2352:
2347:
2344:
2342:
2338:
2334:
2330:
2326:
2321:
2319:
2315:
2311:
2307:
2298:
2290:
2281:
2279:
2278:cyber attacks
2272:
2262:
2260:
2256:
2252:
2251:audio signals
2248:
2247:analog signal
2244:
2240:
2234:
2224:
2222:
2221:routing table
2213:
2209:
2204:
2199:
2189:
2185:
2182:
2178:
2174:
2170:
2165:
2160:
2156:
2146:
2144:
2139:
2137:
2133:
2128:
2125:
2124:retransmitted
2121:
2115:
2105:
2103:
2099:
2095:
2090:
2087:
2086:network media
2083:
2075:
2070:
2065:
2055:
2053:
2049:
2045:
2041:
2037:
2033:
2029:
2023:
2016:Network nodes
2013:
2011:
2007:
1999:
1995:
1991:
1987:
1984:
1981:
1977:
1974:
1970:
1969:
1965:
1962:
1958:
1954:
1952:
1947:
1944:
1940:
1939:
1935:
1932:
1931:
1927:
1924:
1923:
1918:
1917:
1916:
1912:
1903:
1891:
1887:
1883:
1879:
1875:
1871:
1870:
1869:optical fiber
1865:
1864:
1859:
1852:
1848:
1844:
1840:
1836:
1835:
1831:
1828:
1824:
1823:coaxial cable
1820:
1816:
1813:
1810:
1806:
1805:
1804:Coaxial cable
1801:
1800:
1799:
1793:
1789:
1780:
1778:
1777:power cabling
1774:
1770:
1767:, others use
1766:
1762:
1758:
1754:
1749:
1747:
1743:
1742:optical fiber
1739:
1735:
1734:
1727:
1720:Network links
1717:
1715:
1711:
1708:For example,
1706:
1704:
1700:
1696:
1692:
1688:
1684:
1680:
1675:
1673:
1669:
1664:
1662:
1658:
1654:
1649:
1646:
1644:
1640:
1635:
1626:
1617:
1615:
1607:
1604:
1601:
1598:
1595:
1592:
1589:
1585:
1581:
1578:
1575:
1571:
1567:
1563:
1560:
1557:
1554:variants use
1553:
1549:
1545:
1541:
1537:
1533:
1530:
1529:
1528:
1525:
1523:
1513:
1508:
1498:
1496:
1491:
1489:
1485:
1481:
1476:
1474:
1470:
1466:
1462:
1458:
1453:
1451:
1448:carried by a
1447:
1443:
1434:
1425:
1423:
1408:
1405:
1401:
1398:
1395:
1392:
1388:
1384:
1381:
1377:
1373:
1370:
1367:
1363:
1360:
1356:
1352:
1348:
1344:
1340:
1336:
1332:
1328:
1325:
1321:
1317:
1313:
1309:
1305:
1304:Aloha network
1301:
1297:
1293:
1289:
1286:
1282:
1278:
1274:
1270:
1267:
1263:
1259:
1256:
1252:
1249:
1248:Farouk Kamoun
1245:
1241:
1237:
1233:
1229:
1224:
1220:
1217:
1213:
1209:
1205:
1201:
1197:
1193:
1188:
1184:
1180:
1179:Donald Davies
1176:
1172:
1169:
1165:
1161:
1158:
1154:
1151:
1147:
1143:
1140:
1135:
1134:Anatoly Kitov
1131:
1128:
1124:
1121:in 1961, the
1120:
1116:
1112:
1108:
1107:John McCarthy
1104:
1100:
1096:
1093:
1089:
1085:
1081:
1077:
1073:
1069:
1068:
1067:
1065:
1061:
1057:
1047:
1045:
1041:
1037:
1033:
1029:
1028:digital video
1025:
1021:
1017:
1012:
1010:
1006:
1002:
998:
994:
989:
987:
983:
980:and may have
979:
975:
971:
967:
963:
958:
956:
952:
948:
944:
940:
937:
933:
929:
928:network nodes
925:
921:
909:
904:
902:
897:
895:
890:
889:
887:
886:
881:
878:
876:
873:
871:
868:
866:
863:
861:
858:
856:
853:
851:
848:
846:
843:
842:
841:
840:
836:
835:
819:
818:
815:
812:
811:
801:
796:
794:
789:
787:
782:
781:
779:
778:
773:
770:
768:
765:
764:
761:
758:
756:
753:
751:
748:
747:
746:
745:
738:
735:
734:
732:
731:
722:
718:
715:
713:
710:
708:
705:
704:
703:
702:
698:
697:
692:
691:LFR Benchmark
689:
687:
684:
682:
679:
677:
676:Blockmodeling
674:
672:
669:
667:
664:
662:
659:
657:
654:
652:
649:
647:
644:
642:
641:Fitness model
639:
637:
634:
632:
629:
627:
624:
622:
619:
618:
617:
616:
612:
611:
608:
607:
603:
602:
597:
594:
592:
589:
587:
584:
582:
581:Assortativity
579:
577:
574:
572:
569:
567:
564:
562:
559:
557:
554:
553:
552:
551:
545:
542:
540:
537:
536:
534:
533:
524:
521:
519:
516:
514:
511:
509:
506:
504:
501:
499:
496:
494:
491:
489:
486:
485:
484:
483:
479:
478:
472:
468:
464:
461:
457:
453:
451:
448:
446:
443:
441:
438:
436:
433:
431:
428:
426:
423:
421:
418:
416:
413:
411:
408:
406:
403:
402:
401:
400:
396:
395:
392:
391:
388:
385:
384:
379:
376:
374:
371:
369:
366:
364:
361:
359:
356:
354:
351:
349:
346:
344:
341:
339:
336:
334:
331:
329:
326:
324:
321:
319:
316:
315:
314:
313:
310:Network types
309:
308:
303:
300:
298:
295:
293:
290:
288:
285:
283:
280:
278:
275:
273:
270:
268:
265:
263:
260:
258:
257:Link analysis
255:
253:
250:
248:
247:Graph drawing
245:
243:
240:
238:
235:
233:
230:
228:
225:
223:
220:
218:
215:
213:
210:
208:
205:
203:
200:
199:
198:
197:
191:
188:
187:
185:
184:
175:
166:
165:
162:
159:
158:
154:
150:
149:
146:
138:
135:
127:
116:
113:
109:
106:
102:
99:
95:
92:
88:
85: –
84:
80:
79:Find sources:
73:
69:
63:
62:
57:This article
55:
51:
46:
45:
40:
33:
19:
8319:Cyberwarfare
7978:Cryptography
7530:
7329:
7261:file systems
7153:Time-sharing
6805:
6779:the original
6769:
6755:
6727:
6706:. Retrieved
6698:The Guardian
6697:
6684:
6672:. Retrieved
6668:the original
6663:
6653:
6642:. Retrieved
6621:
6610:. Retrieved
6558:
6552:
6541:. Retrieved
6527:
6516:. Retrieved
6512:the original
6502:
6494:the original
6484:
6459:the original
6450:
6443:
6423:
6416:
6389:
6382:
6355:
6348:
6337:. Retrieved
6325:
6321:
6308:
6291:
6287:
6281:
6273:the original
6268:
6259:
6248:. Retrieved
6244:
6235:
6224:. Retrieved
6215:
6206:
6195:. Retrieved
6191:the original
6182:
6173:
6162:. Retrieved
6153:
6143:
6124:
6118:
6099:
6093:
6082:the original
6068:
6057:. Retrieved
6030:
6021:
6010:. Retrieved
5983:
5974:
5961:
5952:
5941:. Retrieved
5932:
5923:
5915:the original
5910:
5900:
5889:. Retrieved
5885:the original
5875:
5865:, retrieved
5858:the original
5849:
5842:
5815:
5795:. Retrieved
5791:the original
5786:
5777:
5767:, retrieved
5753:
5728:. Retrieved
5724:
5714:
5703:. Retrieved
5694:
5685:
5664:
5624:. Retrieved
5604:
5596:
5569:
5565:
5555:
5524:
5517:
5508:
5488:
5484:
5471:
5462:
5449:
5427:(2): 18–26.
5424:
5420:
5414:
5392:(1): 38–44.
5389:
5385:
5379:
5368:. Retrieved
5361:the original
5347:
5336:. Retrieved
5332:the original
5327:
5314:
5306:
5300:. Retrieved
5296:
5286:
5277:
5247:
5234:
5226:
5211:
5204:
5195:
5180:
5173:
5159:
5152:
5139:
5132:
5123:
5108:
5101:
5092:
5072:
5068:
5055:
5047:the original
5032:
5023:
5007:
4987:
4981:
4973:
4966:. Retrieved
4959:the original
4954:
4941:
4933:
4927:. Retrieved
4923:the original
4918:
4909:
4901:
4895:. Retrieved
4879:The Guardian
4878:
4868:
4859:
4849:
4837:. Retrieved
4821:
4814:
4805:
4785:
4781:
4748:
4738:
4730:
4715:
4708:
4700:
4685:
4678:
4669:
4665:
4655:
4646:
4626:
4622:
4612:
4587:
4583:
4573:
4562:. Retrieved
4548:
4537:. Retrieved
4523:
4515:
4509:. Retrieved
4481:
4477:
4450:. Retrieved
4430:
4423:
4415:
4387:
4383:
4370:
4362:
4338:(7): 42–48.
4335:
4331:
4318:
4299:
4293:
4282:. Retrieved
4273:
4263:
4238:
4230:
4219:. Retrieved
4210:
4201:
4190:. Retrieved
4186:the original
4181:
4172:
4161:. Retrieved
4152:
4143:
4134:
4128:. Retrieved
4102:
4092:
4068:
4061:
4037:
4026:
4002:
3995:
3891:
3871:
3859:
3847:
3843:peer-to-peer
3832:
3808:
3774:
3743:
3708:
3686:(E2EE) is a
3682:
3662:
3639:civil rights
3636:
3614:to maintain
3609:
3606:
3599:
3589:unauthorized
3579:
3555:
3536:
3520:
3505:
3470:
3463:
3457:
3449:offered load
3431:to maintain
3422:
3409:
3402:
3395:
3380:
3356:
3312:
3311:
3254:
3237:
3224:
3220:
3190:
3180:
3169:networks as
3167:peer-to-peer
3164:
3151:
3144:
3123:
3091:
3087:internetwork
3084:
3079:IP addresses
3059:
3046:
3037:
3021:
3013:
3006:(VPN) is an
3001:
2989:
2965:
2949:
2932:
2916:
2908:
2897:
2885:
2865:
2852:leased lines
2841:
2827:
2799:
2786:
2777:
2703:Campus (CAN)
2624:
2603:
2580:
2574:
2553:Digital AMPS
2518:
2506:
2479:
2461:multiplexing
2455:
2439:
2436:Wireless LAN
2427:
2394:MAC bridging
2391:
2384:
2364:
2345:
2322:
2318:circuit mode
2303:
2274:
2261:technology.
2236:
2217:
2186:
2166:
2162:
2143:Ethernet hub
2140:
2129:
2117:
2091:
2079:
2025:
2003:
1992:, issued as
1966:
1953:technologies
1948:
1936:
1928:
1920:Terrestrial
1919:
1914:
1867:
1834:Twisted pair
1832:
1802:
1797:
1752:
1750:
1731:
1729:
1707:
1695:IP multicast
1676:
1665:
1650:
1647:
1639:peer-to-peer
1631:
1611:
1606:Tree network
1594:Mesh network
1580:Ring network
1570:wireless LAN
1562:Star network
1526:
1518:
1492:
1477:
1475:in between.
1473:payload data
1454:
1439:
1418:
1358:
1338:
1266:Louis Pouzin
1103:time-sharing
1092:digital data
1053:
1044:fax machines
1016:applications
1013:
1003:to organize
990:
959:
922:is a set of
919:
917:
880:Input/output
869:
666:Hierarchical
621:Random graph
469: /
458: /
440:Neighborhood
317:
282:Transitivity
262:Optimization
145:
130:
121:
111:
104:
97:
90:
78:
66:Please help
61:verification
58:
8329:Video games
8309:Digital art
8066:Concurrency
7935:Data mining
7847:Probability
7580:Interpreter
7279:Device file
7269:Boot loader
7183:Round-robin
7108:Cooperative
7044:Rump kernel
7034:Multikernel
7024:Microkernel
6921:Usage share
6294:(12): 4–6.
5320:Després, R.
4268:Kitova, O.
3758:Google Talk
3741:for radio.
3441:packet loss
3117:(WWW), the
2671:Local (LAN)
2498:low-latency
2442:IEEE 802.11
2414:IEEE 802.1X
2406:IEEE 802.1Q
2398:IEEE 802.1D
2337:IEEE 802.11
1957:IEEE 802.11
1943:transceiver
1827:power lines
1819:home wiring
1765:radio waves
1532:Bus network
1366:David Boggs
1343:Yogen Dalal
1316:Yogen Dalal
1298:describing
1208:NPL network
1192:reliability
860:File system
712:agent based
626:Erdős–Rényi
267:Reciprocity
232:Percolation
217:Small-world
8387:Glossaries
8259:E-commerce
7852:Statistics
7795:Algorithms
7753:Stochastic
7585:Middleware
7441:Peripheral
7209:protection
7165:algorithms
7163:Scheduling
7112:Preemptive
7058:Components
7029:Monolithic
6896:Comparison
6832:Networking
6708:2012-06-17
6690:James Ball
6644:2009-03-13
6612:2009-03-13
6543:2011-11-12
6518:2003-07-13
6339:2011-10-25
6250:2011-11-12
6226:2011-11-12
6197:2011-11-12
6164:2011-01-29
6154:TechTarget
6059:2022-05-09
6012:2022-05-09
5943:2008-04-08
5891:2014-03-01
5867:2011-11-12
5797:2013-05-25
5769:2011-11-12
5730:2023-05-07
5705:2018-04-09
5626:2021-03-08
5370:2017-09-11
5338:2013-08-30
5302:2024-06-05
5119:0824729005
4929:2020-02-18
4897:2020-07-31
4839:2020-09-15
4590:(1): 1–9.
4564:2022-02-12
4539:2022-02-12
4511:2022-02-12
4452:2021-06-04
4284:2021-10-11
4221:2020-01-23
4192:2020-01-23
4163:2020-01-23
4130:2020-05-26
4074:De Gruyter
3987:References
3924:Cyberspace
3875:IP address
3789:key escrow
3692:encrypting
3669:hacktivist
3653:, and the
3628:biometrics
3560:to deploy
3453:throughput
3383:throughput
3371:IP network
3264:throughput
2978:, and the
2725:Wide (WAN)
2691:Home (HAN)
2430:IEEE 802.3
2408:describes
2136:5-4-3 rule
1949:Radio and
1888:(SMF) and
1761:IEEE 802.3
1584:Token ring
1312:John Shoch
1296:Xerox PARC
1257:in Europe.
1175:Paul Baran
1150:mainframes
870:Networking
850:Interrupts
739:Categories
596:Efficiency
591:Modularity
571:Clustering
556:Centrality
544:Algorithms
368:Dependency
343:Biological
222:Scale-free
94:newspapers
8208:Rendering
8203:Animation
7834:computing
7785:Semantics
7476:Processor
7299:Partition
7216:Bus error
7143:Real-time
7123:Interrupt
7049:Unikernel
7014:Exokernel
6470:cite book
5933:webopedia
5911:About.com
5834:748332969
5749:R. Morris
5635:cite book
5505:1558-0857
4887:0261-3077
4746:(2000) .
4643:0018-9219
4604:0096-2244
4404:0018-9219
4352:0163-6804
4043:MIT Press
3835:workgroup
3735:telephony
3704:integrity
3673:Anonymous
3256:Bandwidth
3251:Bandwidth
2814:Bluetooth
2646:Nanoscale
2591:computers
2539:(EV-DO),
2509:last mile
2452:SONET/SDH
2265:Firewalls
2243:modulated
2052:firewalls
2032:repeaters
1922:microwave
1843:crosstalk
1746:OSI model
1714:multicast
1538:, called
1480:bandwidth
1404:Ron Crane
1331:Vint Cerf
1329:In 1974,
1290:In 1973,
1271:In 1973,
1162:In 1965,
1132:In 1959,
1129:in 1963).
1097:In 1959,
997:bandwidth
982:hostnames
924:computers
488:Bipartite
410:Component
328:Transport
277:Homophily
237:Evolution
212:Contagion
124:June 2023
8402:Category
8367:Category
8195:Graphics
7970:Security
7632:Compiler
7531:Networks
7428:Hardware
7345:Live USB
7207:resource
7097:Concepts
6935:Variants
6916:Timeline
6702:Archived
6674:12 March
6635:Archived
6606:Archived
6537:Archived
6330:Archived
6220:Archived
6158:Archived
6053:Archived
6006:Archived
5960:(2003).
5937:Archived
5763:archived
5699:Archived
5620:Archived
5441:34735326
5322:(1974).
5089:26876676
5020:Archived
4891:Archived
4830:Archived
4558:Archived
4533:Archived
4502:Archived
4498:26876676
4446:Archived
4412:26876676
4356:Archived
4278:Archived
4215:Archived
4157:Archived
4136:Meeting.
4121:Archived
4008:ABC-Clio
3912:See also
3867:extranet
3862:intranet
3811:Netscape
3766:Facebook
3744:Typical
3620:criminal
3552:Security
3445:blocking
3359:transmit
3201:printing
3094:Internet
3069:Internet
3062:extranet
3056:Extranet
3049:intranet
3043:Intranet
2810:FireWire
2735:Internet
2708:Backbone
2698:Building
2629:by scale
2606:bridging
2559:(iDEN).
2551:(DECT),
2547:(UMTS),
2543:(EDGE),
2533:CDMA2000
2527:(GPRS),
2490:Ethernet
2446:IEEE 802
2424:Ethernet
2386:IEEE 802
2381:IEEE 802
2212:Ethernet
2114:Repeater
2044:switches
1897:Wireless
1839:Ethernet
1769:infrared
1691:DiffServ
1643:Internet
1536:Ethernet
1469:trailers
1389:created
1359:Internet
1335:Bob Kahn
1300:Ethernet
1262:CYCLADES
1228:Bob Kahn
1040:printers
1020:services
875:Security
755:Software
717:Epidemic
699:Dynamics
613:Topology
586:Distance
523:Weighted
498:Directed
493:Complete
397:Features
358:Semantic
153:a series
151:Part of
8377:Outline
7340:Live CD
7294:Journal
7258:access,
7256:Storage
7133:Process
7039:vkernel
6906:History
6889:General
6585:2204780
5406:1558618
5274:2930578
4802:8172150
3889:(DNS).
3855:subnets
3799:SSL/TLS
3781:clients
3770:Dropbox
3754:servers
3750:clients
3643:privacy
3542:service
3493:CSMA/CA
3443:or the
3321:latency
3268:goodput
3231:), and
3171:sharing
3152:friends
3147:darknet
3141:Darknet
3105:of the
2666:Near-me
2585:direct
2576:Routing
2563:Routing
2529:cdmaOne
2523:(GSM),
2192:Routers
2048:routers
2040:bridges
1808:second.
1699:routers
1687:IntServ
1661:routing
1544:10BASE2
1540:10BASE5
1471:, with
1223:ARPANET
1214:at the
1196:routers
1074:(SAGE)
1050:History
966:servers
947:optical
936:digital
539:Metrics
508:Labeled
378:on-Chip
363:Spatial
272:Closure
108:scholar
39:Network
7148:Thread
7019:Hybrid
6997:Kernel
6836:Curlie
6817:, and
6583:
6573:
6431:
6265:"Maps"
6131:
6106:
6045:
5998:
5832:
5822:
5673:
5612:
5588:429216
5586:
5503:
5439:
5404:
5272:
5262:
5219:
5188:
5116:
5094:Walden
5087:
4994:
4885:
4800:
4756:
4723:
4693:
4641:
4602:
4496:
4438:
4410:
4402:
4350:
4306:
4251:
4113:
4080:
4049:
4014:
3768:, and
3746:server
3737:, and
3671:group
3667:. The
3649:, the
3546:faults
3525:
3497:window
3489:802.11
3403:In an
3387:jitter
3221:nm.lan
3197:E-mail
2494:frames
2412:, and
2259:DOCSIS
2227:Modems
2177:frames
2120:signal
2102:octets
1996:
1753:family
1693:, and
1488:queued
1391:ARCNET
1353:
1206:. The
1062:, and
750:Topics
604:Models
561:Degree
518:Random
471:matrix
460:matrix
450:Vertex
405:Clique
387:Graphs
333:Social
190:Theory
110:
103:
96:
89:
81:
7780:Logic
7614:tools
7350:Shell
7289:Inode
6766:from
6664:ZDNet
6638:(PDF)
6631:(PDF)
6581:S2CID
6462:(PDF)
6455:(PDF)
6333:(PDF)
6328:(4).
6318:(PDF)
6085:(PDF)
6078:(PDF)
5861:(PDF)
5854:(PDF)
5584:S2CID
5481:(PDF)
5459:(PDF)
5437:S2CID
5402:S2CID
5364:(PDF)
5357:(PDF)
5270:S2CID
5244:(PDF)
5164:(PDF)
5144:(PDF)
5085:S2CID
5065:(PDF)
5016:(PDF)
4962:(PDF)
4951:(PDF)
4833:(PDF)
4826:(PDF)
4798:S2CID
4648:work.
4505:(PDF)
4494:S2CID
4474:(PDF)
4408:S2CID
4380:(PDF)
4359:(PDF)
4328:(PDF)
4124:(PDF)
4107:(PDF)
3975:Cloud
3787:, or
3739:TETRA
3719:email
3711:HTTPS
3513:ITU-T
3260:bit/s
3160:ports
3103:DARPA
2834:ITU-T
2730:Cloud
2627:types
2486:cells
2410:VLANs
2323:In a
2233:Modem
2181:ports
1961:Wi-Fi
1812:ITU-T
1783:Wired
1084:modem
1076:radar
1032:audio
974:hosts
934:over
736:Lists
566:Motif
513:Multi
503:Hyper
480:Types
420:Cycle
202:Graph
115:JSTOR
101:books
7612:and
7485:Form
7481:Size
6911:List
6746:2547
6676:2013
6571:ISBN
6476:link
6429:ISBN
6408:1035
6374:5321
6292:2009
6129:ISBN
6104:ISBN
6043:ISBN
5996:ISBN
5830:OCLC
5820:ISBN
5671:ISBN
5645:link
5641:link
5610:ISBN
5530:IETF
5501:ISSN
5260:ISBN
5217:ISBN
5186:ISBN
5114:ISBN
5043:UCLA
4992:ISBN
4970:2017
4883:ISSN
4754:ISBN
4721:ISBN
4691:ISBN
4639:ISSN
4600:ISSN
4436:ISBN
4400:ISSN
4348:ISSN
4304:ISBN
4249:ISBN
4111:ISBN
4078:ISBN
4047:ISBN
4012:ISBN
3900:and
3752:and
3733:for
3731:ZRTP
3725:for
3717:for
3702:and
3641:and
3527:2914
3516:G.hn
3479:and
3363:link
3294:and
3286:and
3215:and
3203:and
3191:The
3129:and
3092:The
2926:and
2904:Cat5
2837:G.hn
2816:and
2808:and
2656:Body
2375:IPv6
2365:The
2329:HTTP
2241:are
2208:ADSL
2157:and
2036:hubs
1998:1149
1845:and
1815:G.hn
1659:and
1614:FDDI
1542:and
1467:and
1446:data
1380:X.75
1376:X.25
1333:and
1275:put
1210:, a
1185:for
1177:and
1139:OGAS
1042:and
1030:and
1018:and
445:Path
435:Loop
430:Edge
373:Flow
87:news
7367:PXE
7355:CLI
7335:HAL
7325:API
7128:IPC
6834:at
6743:RFC
6733:doi
6563:doi
6405:RFC
6395:doi
6371:RFC
6361:doi
6296:doi
6187:ITU
6035:doi
5988:doi
5574:doi
5547:675
5544:RFC
5534:doi
5493:doi
5429:doi
5394:doi
5252:doi
5077:doi
4790:doi
4631:doi
4592:doi
4486:doi
4392:doi
4340:doi
3779:of
3723:OTR
3715:PGP
3564:or
3523:RFC
3491:'s
3298:).
3266:or
3258:in
3156:F2F
3085:An
3060:An
3047:An
2990:An
2874:or
2806:USB
2333:TCP
2312:or
2074:ATM
2072:An
1994:RFC
1866:An
1672:map
1632:An
1415:Use
1355:675
1351:RFC
1232:IMP
721:SIR
415:Cut
70:by
8404::
7483:/
7110:,
6804:,
6773:.
6741:.
6731:.
6717:^
6700:.
6696:.
6662:.
6593:^
6579:.
6569:.
6472:}}
6468:{{
6403:.
6393:.
6369:.
6359:.
6326:16
6324:.
6320:.
6290:.
6267:.
6243:.
6218:.
6214:.
6185:.
6181:.
6156:.
6152:.
6051:.
6041:.
6029:.
6004:.
5994:.
5982:.
5931:.
5909:.
5828:.
5806:^
5785:.
5761:,
5757:,
5739:^
5723:.
5693:.
5653:^
5637:}}
5633:{{
5618:.
5582:.
5570:19
5568:.
5564:.
5542:.
5532:.
5528:.
5507:.
5499:.
5489:22
5487:.
5483:.
5461:,
5435:.
5425:47
5423:.
5400:.
5390:21
5388:.
5326:.
5305:.
5295:.
5276:.
5268:.
5258:.
5246:.
5225:.
5194:.
5122:.
5091:.
5083:.
5073:66
5071:.
5067:.
5041:.
4972:.
4953:.
4932:.
4917:.
4900:.
4889:.
4881:.
4877:.
4858:.
4804:.
4796:.
4784:.
4780:.
4768:^
4729:.
4699:.
4668:.
4664:.
4645:.
4637:.
4627:66
4625:.
4621:.
4598:.
4588:12
4586:.
4582:.
4514:.
4500:.
4492:.
4482:66
4480:.
4476:.
4461:^
4444:.
4414:.
4406:.
4398:.
4388:66
4386:.
4382:.
4354:.
4346:.
4336:40
4334:.
4330:.
4272:.
4247:.
4245:13
4213:.
4209:.
4180:.
4155:.
4151:.
4133:.
4119:.
4076:.
4072:.
4041:.
4006:.
3896:,
3772:.
3764:,
3760:,
3729:,
3721:,
3706:.
3572:.
3475:,
3468:.
3439:,
3389:,
3385:,
3369:.
3282:,
3278:,
3274:,
3213:IP
3199:,
3195:,
3162:.
3145:A
3030:.
3022:A
3002:A
2982:.
2966:A
2958:.
2950:A
2917:A
2898:A
2886:A
2866:A
2828:A
2800:A
2787:A
2535:,
2531:,
2404:.
2304:A
2280:.
2138:.
2046:,
2042:,
2038:,
2034:,
2030:,
1740:,
1689:,
1645:.
1459:,
1452:.
1314:,
1198:,
1058:,
1038:,
1026:,
999:,
988:.
968:,
964:,
957:.
918:A
155:on
7421:.
7401:e
7394:t
7387:v
7204:,
7114:)
7106:(
6874:e
6867:t
6860:v
6748:.
6735::
6711:.
6678:.
6647:.
6615:.
6587:.
6565::
6546:.
6521:.
6478:)
6437:.
6410:.
6397::
6376:.
6363::
6342:.
6302:.
6298::
6253:.
6229:.
6200:.
6167:.
6137:.
6112:.
6062:.
6037::
6015:.
5990::
5968:.
5946:.
5894:.
5836:.
5800:.
5733:.
5708:.
5679:.
5647:)
5629:.
5590:.
5576::
5549:.
5536::
5495::
5443:.
5431::
5408:.
5396::
5373:.
5341:.
5254::
5079::
5000:.
4842:.
4792::
4786:9
4762:.
4633::
4606:.
4594::
4567:.
4542:.
4488::
4455:.
4394::
4342::
4312:.
4287:.
4257:.
4224:.
4195:.
4166:.
4086:.
4055:.
4020:.
3154:(
2767:e
2760:t
2753:v
2396:(
1982:.
1963:.
1945:.
1821:(
1576:.
1152:.
907:e
900:t
893:v
799:e
792:t
785:v
719:/
137:)
131:(
126:)
122:(
112:·
105:·
98:·
91:·
64:.
41:.
34:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.